Greeting Everyone ! Hope Everything Is Going Well And Good Today in this blog we will explore XXE attack Which Is Critical Vulnerability Found on Web Application . We Will Explore In Details What is XXE , How Successfully Perform XXE Attack against Your Target Application .
What is XXE Attack ?
XXE Attack Which appear when an application parses XML. When malicious xml parsing Not filtered web application and underlying server as result an insecure XML file parsing process. XXE attack Found On XML Based Application .
XML Extensible markup language (XML) was originally created to be used among publishing services but has now become a preferred way for various varieties of applications to exchange data among one another and is usually used in many situations more than HTML for data interchange.
What are XML External Entities?
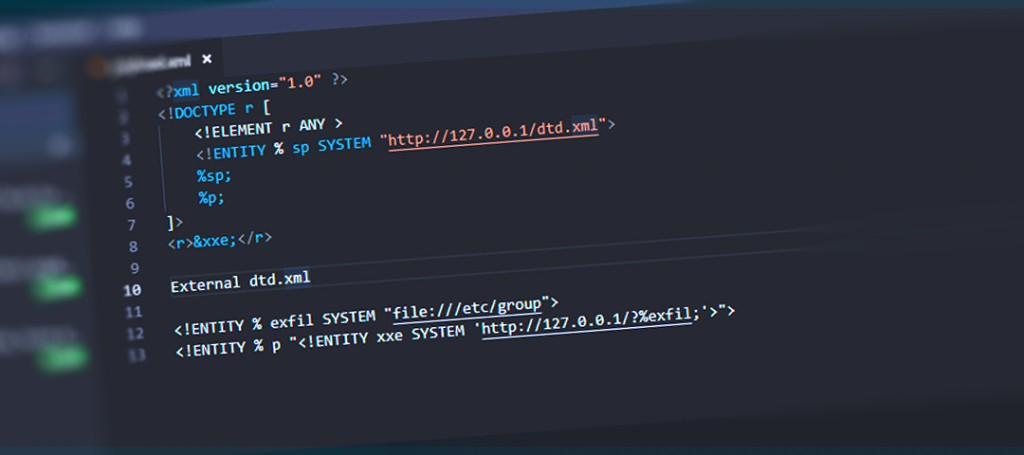
XML file documents which contain “entities” that are defined as DOCTYPE header and have the power to access control remote external systems or local content found within the server hosting the net application and XML parser. When the web application parses the XML document, it has power to switch the “entity” with the value that’s specified an as It give Result as output .
External entities which define the sources and destinations of information entering and leaving the system.
How To Supply Successful XXE attack
Exploiting XXE attack using external entities to retrieve files We will exploit against entity.
As LAB: https://portswigger.net/web-security/xxe/lab-exploiting-xxe-to-retrieve-files Here we have Online ecommerce Application
As above Picture We See Home Page Here We have Option Check stock as Below Picture

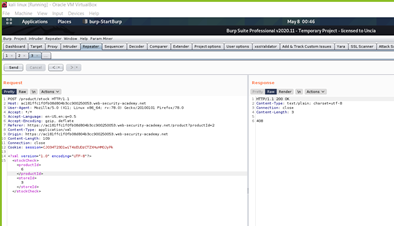
As Above Picture If we analyse it Response Through Burp Data is parsing Through xml Which Share as Below Code Structure
<?xml version=”1.0″ encoding=”UTF-8″?><stockCheck><productId>2</productId><storeId>1</storeId></stockCheck>
As Above We See Product ID Store ID Which Contain two variable And It call product using XML .
As We already Captured Request using Burp :

As Above Picture We How XML file Parsing User Data to Server Now Here We will See Response If we change Product value 5 to 6 As Response See Below Picture :
As Above Picture We Have different Response For Different variable Value Now We Will try to inject XML Entity Through XMl

As above We Inject Entity Which parse User Command And Execute It to Target System As Above We set ENTITY xxe SYSTEM file:///etc/passwd And We will Inject xxe Value to our Product variable Which is present with entity
- <?xml version=”1.0″ encoding=”UTF-8″?>
- <!DOCTYPE foo [ <!ENTITY xxe SYSTEM “file:///etc/passwd”> ]>
- <stockCheck><productId>&xxe;</productId><storeId>3</storeId></stockCheck>

As Above Result Out system Command Was Executed Which we Supplied through Entity with Product Variable And We able To manipulate /etc/passwd Which Internal File .
As Above We Successfully Verified if application is not properly validate entity And attacker can able to Perform Command Injection , Remote Code Injection SSRF through This Misconfiguration . SSRF Through XXE
Mitigation Against Risk :
- use less complex data formats such as JSON, and avoiding serialization of sensitive data.
- Implement positive (“whitelisting”) server-side input validation, filtering, or sanitization to prevent hostile data within XML documents, headers, or nodes.
Conclusion:
Today We Discussed How XXE Attack work We Discussed Common Attack which allow an attacker to perform OS command Injection , Rce if application Is Fail to Protect against user Supplied Input Which cause Impact . We Successfully Completed Our LAB .



