Home » URL Filtering
URL Filtering is the related technology that controls the grants and access given to the users and accordingly what permissions have been designated to access the certain kind of information.
URL Filtering restricts access to certain URLs by assessing the addresses of websites that consumers are trying to go to from a database of permitted or blocked websites. The objective of it’s to prevent workers from accessing websites that will interfere with the performance of their company — such as websites not associated with work, websites with illegal or illegal material, or sites related to phishing attempts.
While unfettered net access is helpful for workers and may make them more effective, it may also introduce organizations to a vast variety of security risks, including propagation of dangers, data reduction or seizure, or legal troubles.
URL filtering matches web traffic from a database that is defined, then it allows or denies entry to some website based on whether it’s located in the database. A URL filtering database may assign catalogued sites a URL class, or category. Additionally, it will specify the conditions of access to this URL. By Way of Example, an address may be
Blocked: This may apply to deflecting sites, such as social media or local information provider sites, or sites known to sponsor different kinds of malware.
Attached to specified IT policies: Visits to a specific website could be structured and logged, so it could see who visits particular websites, and in what time.
Blocked or enabled URL classes: When activities are decided never on a site-by-site foundation, but instead from the group encompassing numerous websites. This may include classes for malware or phishing websites, innocent but deflecting sites, or suspicious websites.

Steps of URLs Filtering
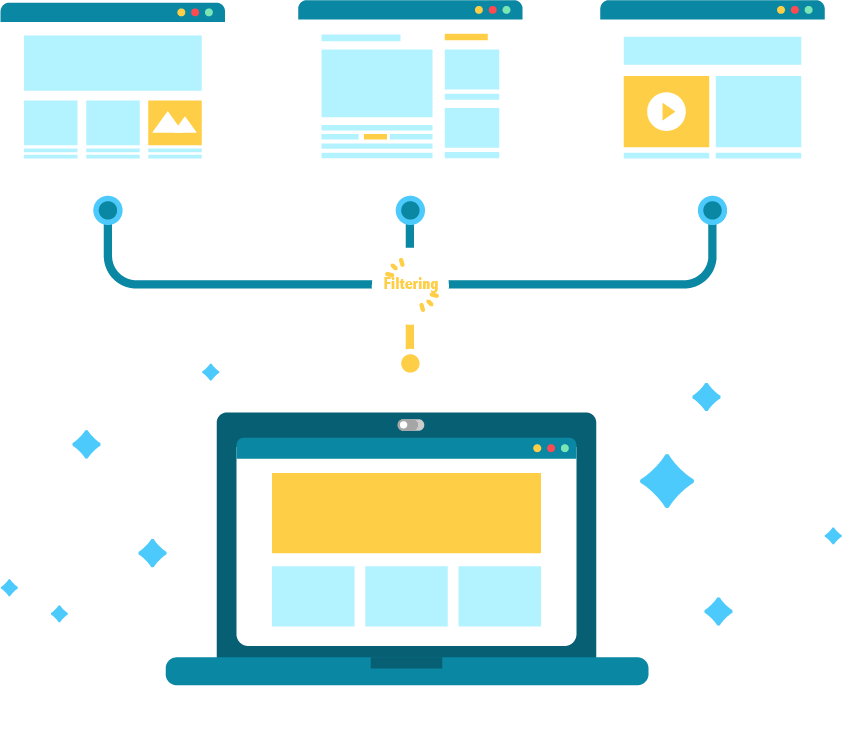
Policy Configuration: Define the desired web access policies, including allowed or blocked categories, specific URLs, or keywords.
URL Categorization: URLs are categorized into various groups based on their content, such as social media, adult content, or gambling.
Database Updates: Regularly update the URL filtering service’s database with new URLs and their associated categories to ensure accurate filtering.
Real-time Filtering: Incoming web requests are compared against the configured policies and the URL database to determine if access should be allowed or blocked.
Logging and Reporting: Maintain logs of web access attempts, including the blocked URLs and user activity, for auditing and reporting purposes.
Overrides and Exceptions: Allow administrators to override or create exceptions to certain policies for specific users or scenarios.
Ongoing Monitoring and Maintenance: Continuously monitor the effectiveness of the URL filtering service, make necessary adjustments to policies, and address any false positives or negatives.
URL filtering with headings provides several benefits. First, it improves website navigation by organizing content into logical sections, allowing users to quickly locate relevant information.
Second, it enhances search engine optimization (SEO) by providing clear and structured HTML tags, helping search engines understand and index the page’s content more effectively.
Third, it improves accessibility for users who rely on screen readers, as headings provide a hierarchical structure for easier comprehension.
Fourth, it aids in content management and editing, allowing webmasters to make changes efficiently by targeting specific sections.
Overall, URL filtering with headings improves user experience, SEO, accessibility, and content management, making websites more effective and user-friendly.


URL filtering services are essential for various individuals and organizations seeking to regulate internet access and enhance online security.
Educational institutions rely on URL filtering to ensure a safe browsing environment for students, preventing access to inappropriate content.
Similarly, businesses implement such services to enhance productivity and protect their networks from malicious websites and potential cyber threats.
Government agencies employ URL filtering to enforce compliance with regulations and restrict access to unauthorized or harmful websites. Additionally, parents utilize these services to safeguard their children from explicit or age-inappropriate content.
Overall, URL filtering services offer an effective means of controlling internet access and protecting users from potential risks and harmful online content.
URL filtering services play a crucial role in ensuring online security and productivity. By implementing these services, organizations can protect their networks from malicious websites, phishing scams, and inappropriate content.
Filtering URLs based on predefined categories allows businesses to enforce acceptable usage policies, safeguard sensitive data, and prevent malware infections.
Additionally, filtering URLs aids in improving employee productivity by blocking access to distracting or non-work-related websites. It helps organizations comply with legal regulations and maintain a safe digital environment.
By efficiently managing internet access and controlling web content, URL filtering services contribute to a secure and efficient online experience for individuals and businesses alike.
Securium Solutions offers top-notch URL filtering services that ensure comprehensive and effective web security.
With a wealth of experience and cutting-edge technology, Securium Solutions delivers advanced solutions tailored to meet the unique needs of organizations. Their filtering URL services provide robust protection against malicious websites, inappropriate content, and cyber threats, safeguarding networks and sensitive data.
By employing intelligent algorithms and real-time analysis, they accurately classify and filter URLs, granting users granular control over web access.
With an intuitive interface and customizable policies, Securium Solutions empowers organizations to enforce web usage policies, increase productivity, and maintain a secure online environment.
Filtering URL is a methodology that restricts the user from accessing and controlling the features of the websites being used.
Securium Solutions is a URL Filtering Company in Delhi NCR that provides solutions for integrating a safe environment for accessing the network. You contact her at support@securiumsolutions.com. to know about the URL Filtering in Delhi.
Securium Solutions offers URL Filtering services in Bangalore that would help you to make consistent space for work so that your information remains safe within the walls of the organization. For giving this services, Securium Solutions is considered to be the best URL Filtering Company in Bangalore.
For integrated solutions in URL Filtering in Mumbai & Kolkata you get to have extra security features by which you can extend your security walls by implementing extra walls by filtering the unwanted data from coming in the system.
To get URL Filtering services in India, Securium Solutions is the best Cyber Security company in Gurgaon. To get services you can contact at support@securiumsolutions.com to know about it.