Home » Secure DevOps/DevSecOps Services
In today’s rapidly changing technological landscape, cybersecurity has become more important than ever before. Companies need to ensure that their software and applications are secure from cyber threats. Secure DevOps/DevSecOps is an approach that helps organizations integrate security into their DevOps processes. It is a combination of development, operations, and security practices to enable rapid and secure delivery of software applications.
Securium Solutions is a leading provider of Secure DevOps or DevSecOps Services, helping organizations of all sizes to secure their applications and software. We offer a range of services and solutions to help companies adopt a DevSecOps approach and implement the necessary security measures to protect their systems and data.
Development: In the development phase, developers write code and create software applications. In a DevSecOps environment, security is integrated into the development process from the very beginning. This means that developers must be trained in security best practices and security testing is conducted during the development process. This ensures that security is a fundamental part of the application design and that potential vulnerabilities are identified and addressed early in the development cycle.
Operations: In the operations phase, the software is deployed and operated in production environments. Operations teams are responsible for managing the infrastructure and ensuring that the software is performing as expected. In a DevSecOps environment, operations teams work closely with development teams to ensure that security is maintained throughout the deployment and operations process. This includes monitoring for security vulnerabilities and responding quickly to any potential security incidents.
Security: In the security phase, security measures are implemented to ensure that the software is secure and protected from cyber threats. Security teams are responsible for identifying potential vulnerabilities and implementing security controls to mitigate the risk of cyber attacks. In a DevSecOps environment, security is integrated into the entire development and deployment process. This means that security teams work closely with development and operations teams to ensure that security is maintained throughout the software development life cycle.
Adopting a DevSecOps Cyber Security Strategy
Adopting a DevSecOps cyber security strategy involves integrating security into the software development life cycle from the beginning. This means that security is not just an afterthought or something that is added at the end of the development process. Instead, security is an integral part of the software development process, with security considerations being included at every stage of the development cycle.
The first step in adopting a Secure DevOps/DevSecOps or DevSecOps cyber security strategy is to ensure that everyone involved in the software development process is aware of the importance of security. This includes developers, operations staff, and security personnel. All team members should receive training on security best practices, including secure coding techniques, security testing, and incident response procedures.
The next step is to implement security testing throughout the development cycle. This can include both static and dynamic analysis testing to identify vulnerabilities in the code. Static analysis testing involves analyzing the code without executing it, while dynamic analysis testing involves analyzing the code as it runs.
Another important aspect of a DevSecOps cyber security strategy is to implement security controls to protect against known threats. This can include access controls, firewalls, intrusion detection and prevention systems, and encryption. These controls should be integrated into the development process and tested thoroughly to ensure that they are effective.
Finally, incident response procedures should be developed and tested to ensure that the organization is prepared to respond to a security incident.
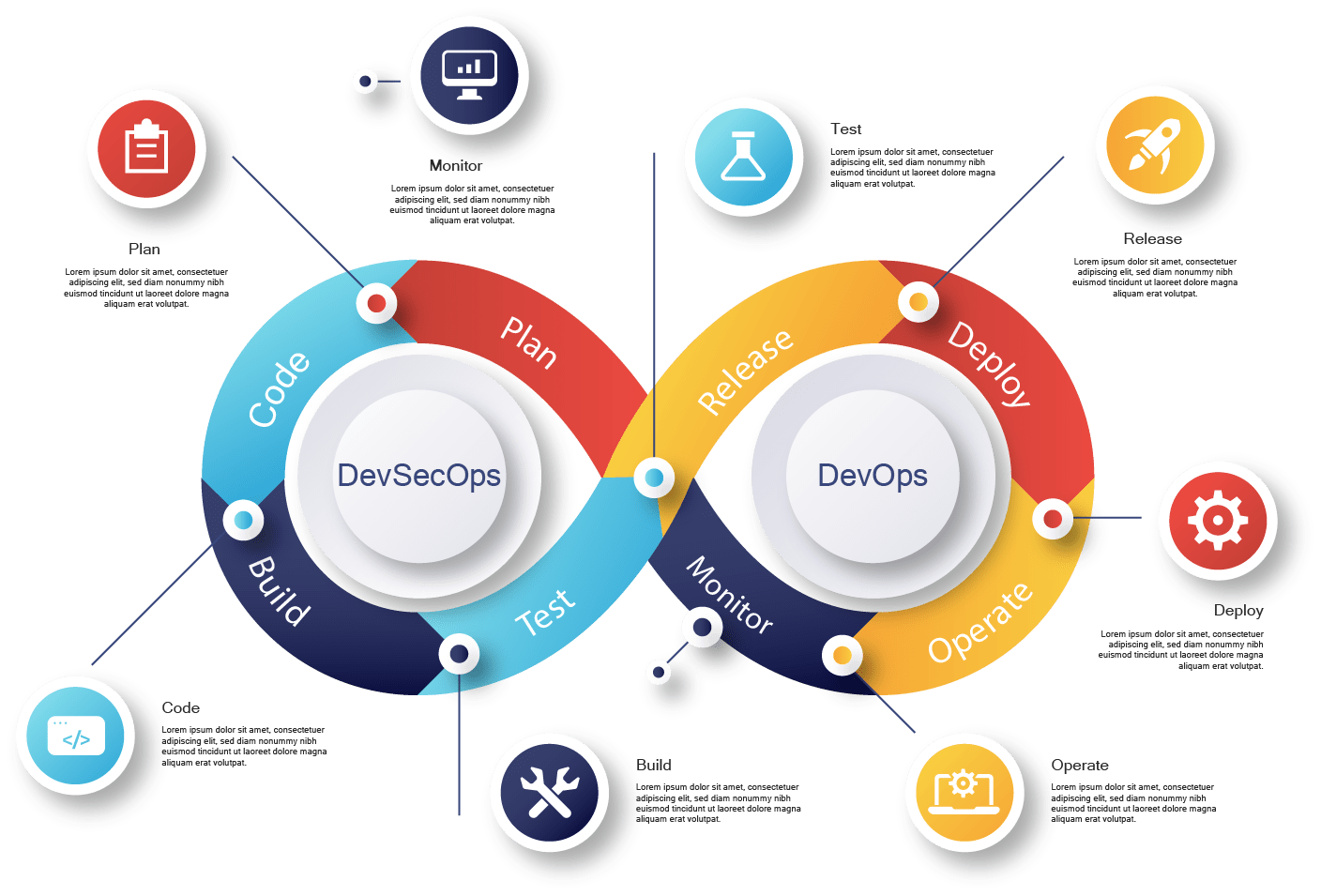
Focus: The primary focus of Secure DevOps/DevSecOps is security, while the primary focus of DevOps tools is collaboration and communication between development and operations teams.
Integration: devsecops tools integrate security into every step of the software development life cycle, while DevOps primarily focuses on the development and deployment phases.
Tools: DevSecOps incorporates additional security tools and processes to identify and remediate vulnerabilities in the software application, while DevOps primarily focuses on automation and agile methodologies.
Testing: DevSecOps places a greater emphasis on testing and validation of security controls throughout the development cycle, while DevOps primarily focuses on testing and validation of functional requirements.
Benefits: DevSecOps can help organizations reduce the risk of security incidents and data breaches by identifying and remediating vulnerabilities early in the development cycle, leading to cost savings and reduced downtime. DevOps can help organizations deliver high-quality software releases quickly and efficiently, leading to improved customer satisfaction and increased competitiveness.
Assess your current security posture: Start by assessing your organization’s current security posture and identifying any vulnerabilities or gaps in your security program. This will help you determine where to focus your DevSecOps efforts and identify areas for improvement.
Develop a DevSecOps strategy: Secure DevOps/DevSecOps a strategy that outlines how you will integrate security into the software development and deployment process. This strategy should include specific goals, timelines, and metrics for success.
Collaborate across teams: DevSecOps requires collaboration across development, operations, and security teams. Encourage communication and collaboration between these teams to ensure that everyone is aligned with the DevSecOps strategy.
Automate security processes: Automate security processes as much as possible to improve efficiency and reduce the risk of errors. Use tools like continuous integration and deployment (CI/CD) pipelines, security testing tools, and configuration management tools to automate security processes.
Monitor and measure success: Monitor and measure the success of your devsecops tools program using metrics like mean time to remediate (MTTR) and security incident response time. Use this data to identify areas for improvement and make adjustments to your DevSecOps strategy as needed.
Improved security: DevSecOps integrates security into every step of the software development life cycle, reducing the risk of security incidents and data breaches. This leads to increased customer trust and reduced downtime.
Increased efficiency: By automating security processes and integrating security into development and deployment workflows, DevSecOps improves efficiency and reduces the risk of errors.
Improved collaboration: DevSecOps requires collaboration between development, operations, and security teams, leading to improved communication, teamwork, and alignment across the organization.
Regulatory compliance: DevSecOps can help organizations comply with regulatory requirements related to security and data privacy, reducing the risk of penalties and legal issues.
Better customer satisfaction: DevSecOps can improve customer satisfaction by delivering high-quality software that meets or exceeds customer expectations.
Expertise: Securium Solutions has a team of highly skilled experts in software development, operations, and security. They have extensive experience in implementing DevSecOps and can provide guidance and support throughout the process.
Customized solutions: Securium Solutions offers customized DevSecOps solutions that are tailored to meet the specific needs and goals of each organization. They work closely with clients to understand their requirements and develop solutions that meet their unique needs.
Advanced tools and technologies: Securium Solutions uses the latest tools and technologies to implement DevSecOps, including continuous integration and deployment (CI/CD) pipelines, security testing tools, and configuration management tools.
Proven methodology: Securium Solutions follows a proven methodology for implementing DevSecOps, including assessing current security posture, developing a DevSecOps strategy, collaborating across teams, automating security processes, implementing security controls, and monitoring and measuring success.
Regulatory compliance: Securium Solutions has experience helping organizations comply with regulatory requirements related to security and data privacy. They can provide guidance and support to ensure that clients meet all relevant regulations.
Comprehensive approach: Securium Solutions takes a comprehensive approach to DevSecOps, integrating security into every step of the software development life cycle. This leads to improved security, faster time to market, increased efficiency, and cost savings.
When considering DevSecOps, it’s important to ask key security questions to ensure that your organization is fully prepared to adopt this methodology. Here are some frequently asked questions related to costing, timing, and other important considerations:
The cost of DevSecOps implementation can vary widely depending on factors such as the size of the organization, the complexity of the software development and deployment processes, and the level of security required. It’s important to work with a DevSecOps provider like Securium Solutions to assess your needs and determine the most cost-effective approach.
The timeline for DevSecOps implementation can also vary widely depending on factors such as the size and complexity of the organization and the level of security required. It’s important to work with a DevSecOps provider to develop a customized implementation plan and timeline.
DevSecOps is designed to improve the efficiency of software development and deployment, but it can also impact timelines by adding security measures and testing processes. It’s important to work with a DevSecOps provider to develop a plan that balances security requirements with project timelines.
DevSecOps can address a wide range of security risks, including those related to application vulnerabilities, access controls, data privacy, and compliance. It’s important to work with a DevSecOps provider to identify and prioritize the most critical security risks and develop a plan to address them.
DevSecOps requires close collaboration between development, operations, and security teams to ensure that security is integrated into every step of the software development life cycle. It’s important to work with a DevSecOps provider to develop a plan for effective communication and collaboration across teams.
DevSecOps can help organizations comply with regulatory requirements related to security and data privacy by integrating security into every step of the software development life cycle. It’s important to work with a DevSecOps provider to ensure that your implementation meets all relevant regulations.