Home » Phishing Simulation Services
Welcome to Securium Solutions, your trusted partner in cybersecurity. We specialize in providing customized phishing simulation services to help businesses protect themselves from cyber-attacks. In this landing page, we’ll explain what phishing simulation is, why it’s important, how we’ll be targeting employees, and why you should choose Securium Solutions for live training and cybersecurity education.
Phishing simulation is a very effective way for businesses to protect themselves from cyber-attacks. It involves creating simulated phishing emails or social media posts that mimic real-world attacks and sending them to employees to see how they respond. By doing this, businesses can identify vulnerabilities in their security systems and train their employees to recognize and avoid phishing attacks.
Phishing attacks are a common and growing threat to businesses of all sizes. They involve sending deceptive emails, social media posts, or messages that appear to be from a trusted source but are actually designed to trick the recipient into divulging sensitive information or clicking on a malicious link. These attacks can lead to data breaches, financial losses, and damage to a business’s reputation.
Phishing simulation programs are an effective way to reduce the risk of these attacks by training employees to recognize and avoid them. By investing in a phishing simulation program, businesses can help protect their assets, information, and reputation from cyber threats.
Phishing simulation programs can be customized to fit a business’s specific needs. The simulations can be designed to mimic the types of phishing attacks that are most likely to target a business, and employees can be targeted based on their interests and position within the company. This targeted approach makes the simulations more relevant and effective.
Phishing simulation programs typically provide businesses with valuable insights into their security vulnerabilities. These insights can be used to identify areas where additional training or security measures are needed to reduce the risk of a successful phishing attack.

Template Creation: To begin, we’ll work closely with you to understand your business’s unique needs and vulnerabilities. We’ll assess your current security systems and identify the types of phishing attacks that are most likely to target your business. This will allow us to create customized phishing simulation templates that mimic those attacks and are tailored to your business’s specific needs.
Gathering Information about employees: Once we have the templates in place, we’ll work with you to identify the employees who are most at risk of being targeted by phishing attacks. We’ll take into account factors such as their job functions, level of access to sensitive data, and the types of communications they typically receive. This will allow us to target the simulations to employees who are most likely to encounter real-world phishing attacks.
Sending Phishing Links or Files: We’ll also take into account employees’ interests and hobbies to make the simulations more engaging and relevant. For example, if an employee is an avid sports fan, we may create a phishing simulation that purports to offer free tickets to a sporting event. This makes the simulation more enticing and increases the likelihood that the employee will engage with it.
Live Training by Securium Solutions
After a successful phishing attack, we believe that education and training are essential components of effective cybersecurity. That’s why we offer live training sessions after successful phishing attacks to educate and strengthen your team’s cybersecurity awareness.
Our live training sessions are conducted by expert trainers who have years of experience in the cybersecurity industry. We understand that every business is different, and that’s why we tailor our training sessions to meet your specific needs.
During our live training sessions, we cover a wide range of topics related to cybersecurity, including best practices for identifying and avoiding phishing attacks, how to create strong passwords, how to use two-factor authentication, and more. Our trainers use real-world examples and case studies to help your team understand the importance of cybersecurity and how it can impact your business.
We also provide hands-on training exercises to reinforce the concepts that we cover in our training sessions. These exercises are designed to simulate real-world cybersecurity scenarios, so your team can practice identifying and responding to potential threats.

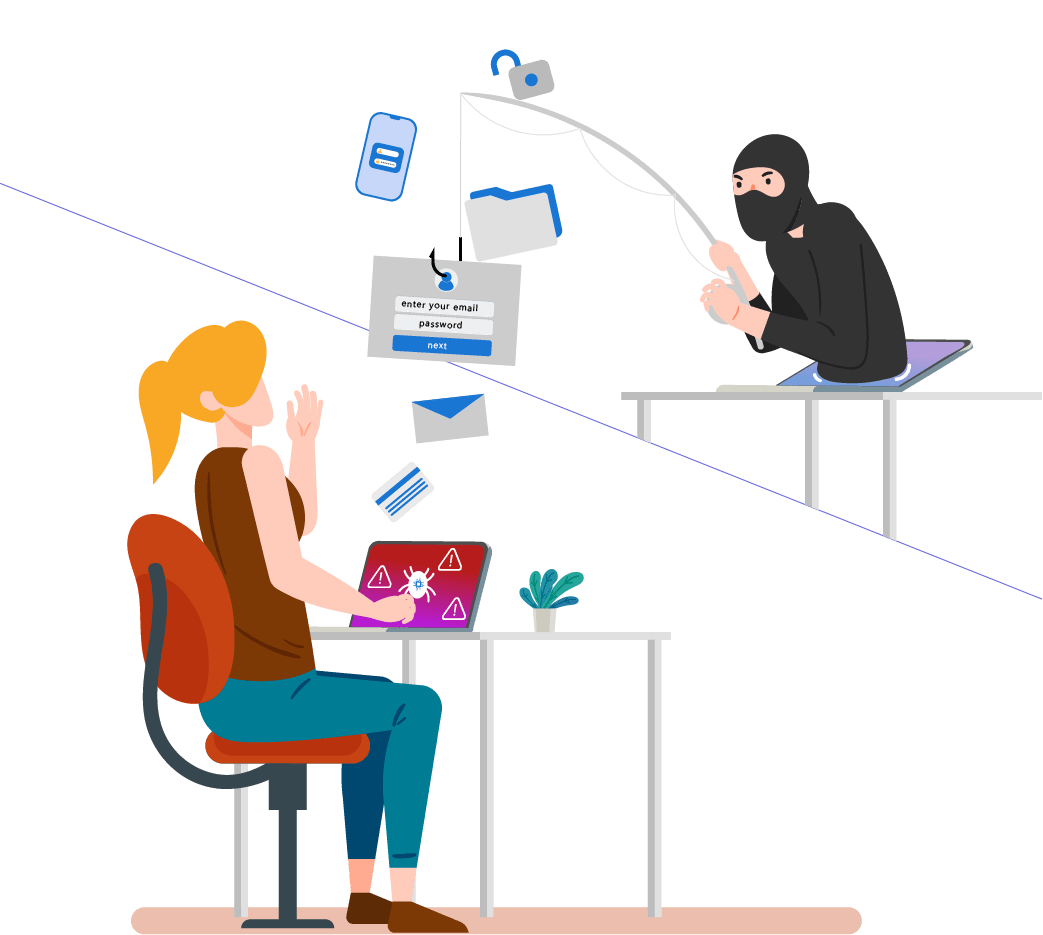
Security Awareness: Phishing simulations help raise awareness among employees about the risks and techniques used by cybercriminals. By experiencing realistic phishing attempts, employees become more vigilant and can identify and report suspicious emails or links.
Training and Education: Simulations provide valuable training opportunities to educate employees about the potential dangers of phishing attacks. They learn how to recognize phishing indicators, such as misspellings, suspicious URLs, or requests for personal information.
Risk Mitigation: By regularly conducting phishing simulations, organizations can proactively identify vulnerabilities in their security systems. This allows them to take necessary measures to strengthen defenses and mitigate the risk of successful phishing attacks.
Incident Response Improvement: Phishing simulations serve as a practice ground for employees to understand how to respond to a potential attack. They learn proper incident reporting procedures and can be trained on the steps to take if they accidentally fall victim to a phishing attempt.
Expertise: Our team of cybersecurity experts has years of experience in the industry, and we stay up-to-date with the latest trends and threats in order to provide the most effective solutions for your business.
Customized template: At Securium Solutions, we understand that every business is unique, and that’s why we provide customized phishing simulation templates that are tailored to your business’s specific needs. We’ll work with you to identify the types of phishing attacks that are most likely to target your business, and we’ll create templates that mimic those attacks.
Targeted approach: We’ll target employees based on their interests and position to make the simulations more relevant and effective. By doing this, we can ensure that your team is trained on the types of attacks that are most likely to affect them. This targeted approach helps ensure that your team is fully prepared to recognize and avoid phishing attacks.
Live training sessions: We believe that education and training are essential components of effective cybersecurity. That’s why we offer live training sessions after successful phishing attacks to educate and strengthen your team’s cybersecurity awareness.
Reporting and analysis: Our reporting and analysis tools provide you with valuable insights into your business’s security vulnerabilities, so you can take action to address them. We’ll provide you with detailed reports that show which employees are most susceptible to phishing attacks, which types of attacks are most successful, and more.
The cost of phishing simulation can vary depending on the provider, the number of employees being trained, and the level of customization required. At Securium Solutions, we offer competitive pricing and can provide a customized quote based on your specific needs.
The duration of a phishing simulation can vary depending on the complexity of the templates and the number of employees being trained. Typically, a simulation can be completed within a few hours or a few days. At Securium Solutions, we’ll work with you to create a timeline that meets your business’s needs.
It’s recommended that businesses conduct phishing simulations on a regular basis, such as quarterly or bi-annually. However, the frequency of simulations may vary depending on your business’s specific needs and the level of risk. At Securium Solutions, we’ll work with you to determine the best frequency for your business.
At Securium Solutions, we use a targeted approach to ensure that employees receive training that is relevant to their roles and responsibilities. We’ll work with you to identify the types of phishing attacks that are most likely to affect your business, and we’ll create templates that mimic those attacks.
At Securium Solutions, we offer live training sessions after successful phishing attacks to educate and strengthen your team’s cybersecurity awareness. Our expert trainers will guide your team through best practices for identifying and avoiding phishing attacks, giving your business an added layer of protection against cyber threats.
At Securium Solutions, we provide detailed reports that show which employees are most susceptible to phishing attacks, which types of attacks are most successful, and more. This information can help you make informed decisions about how to improve your business’s security.