Hey today we are going to learn how to exploit insecure deserialization with some practical lab also
Manipulating the serialized object
This is kind of exploitation is easy if the developer in not verifying the user input in the serialized object. Here simply we can change the attribute in the serialized object and gain access to restricted resources
1. Modifying object attributes
When we are changing the attribute, we need to preserve the valid serialize object so the deserialize process will create a server side object with modified attribute values.
Let understand with example
Consider a website which creates a serialized user’s object to store the user session data in a cookie. We can decode it to find the following byte stream
O:4:”User”:2:{s:8:”username”;s:6:”carlos”;s:7:”isAdmin”;b:0;}
Now this is Admin attribute seems interesting and we can exploit it to gain admin priviledges. We will do it pratically on lab.
We are going to use the portswigger lab. Here is the link for it :-
Now after login we interrupt the request in the burp and we can see there that there is a cookie which stores the serialized object.

On decoding this cookie we see that it stores the user session information
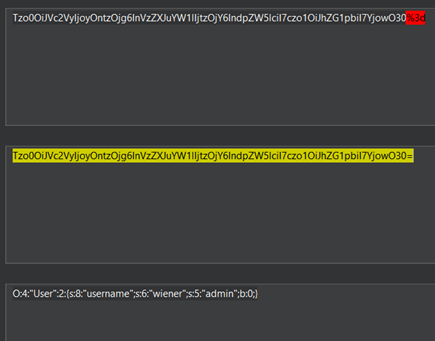
Now what if we change the admin attribute value from 0 to 1. Do we get the admin priviledeges or not?
Let’s do it and then see the result

After changing the attribute encode it to the base64.
Now copy this value and replace the session cookie value in your browser local storage using inspect option or you can use the cookie editor extension also.

Reload the website and you can see the admin panel option in website.

2. Modify The Data Type
This is another way of exploiting the insecure deserialization by modifying the data type. Suppose the website is using the PHP at it backend. Then it is vulnerable to this type of attack because of the behaviour of the loose comparision operator (==) when comparing different data type.
Example if we compare 5==”5 of something” then it will return the true result because this operator comvert the string data type to integer and ignore all the character other than the number. It become equal to 5==5 which always result true value.
Now exploit it in the practical lab to gain admin account.

Now login into the site and interrupt the request in the burp to check the cookie.

After decoding the cookie value we get this
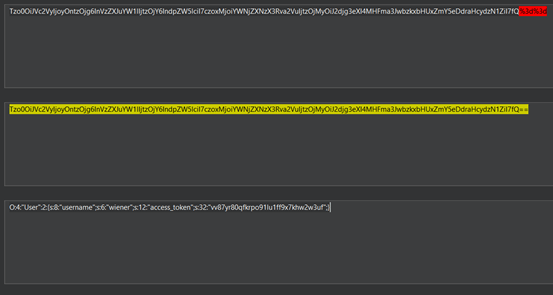
We can see that they are using the access token to verifing the user. Now what can we do with this token to get the access to admin account. At the backend the compare the user access token for authentication of user. What if we change the data type of access token so that when application compare at the backend will also result true.

Now we change username to administrator and access_token to integer type and encod it as the base64 value.
Now copy this value and replace the session cookie value in the browser using the inspect option or using the cookie editor.

Now reload it and you get access to the admin panel.




