March 2, 2023 / by securium solutions
What is Metasploit
Metasploit is an open-source penetration tool that is used for developing and executing exploit code against a remote target machine. It was first developed by HD Moore in 2003 as a project to simplify the process of exploiting vulnerabilities majorly found in network testing. Later, it was purchased by Rapid and rewritten in Ruby language.
Features of Metasploit
One of the key features of Metasploit is its extensive library of exploits and payloads, which allows users to launch attacks on specific vulnerabilities using a variety of methods.
Metasploit also contains various modules. A module is a piece of software that the Metasploit framework uses to perform a task, such as exploiting or scanning targets.
Metasploit comes with pre-installed in kali and it’s stored in /usr/share/metasploit-framework directory as,

As it’s shown above, there are 7 types of modules available in metasploit:
Exploit: Exploits are programs that take advantage of vulnerabilities in software or systems to gain unauthorized access. Metasploit’s exploit module contains a vast library of exploits that can be used to target a wide range of vulnerabilities in various operating systems, applications, and services.

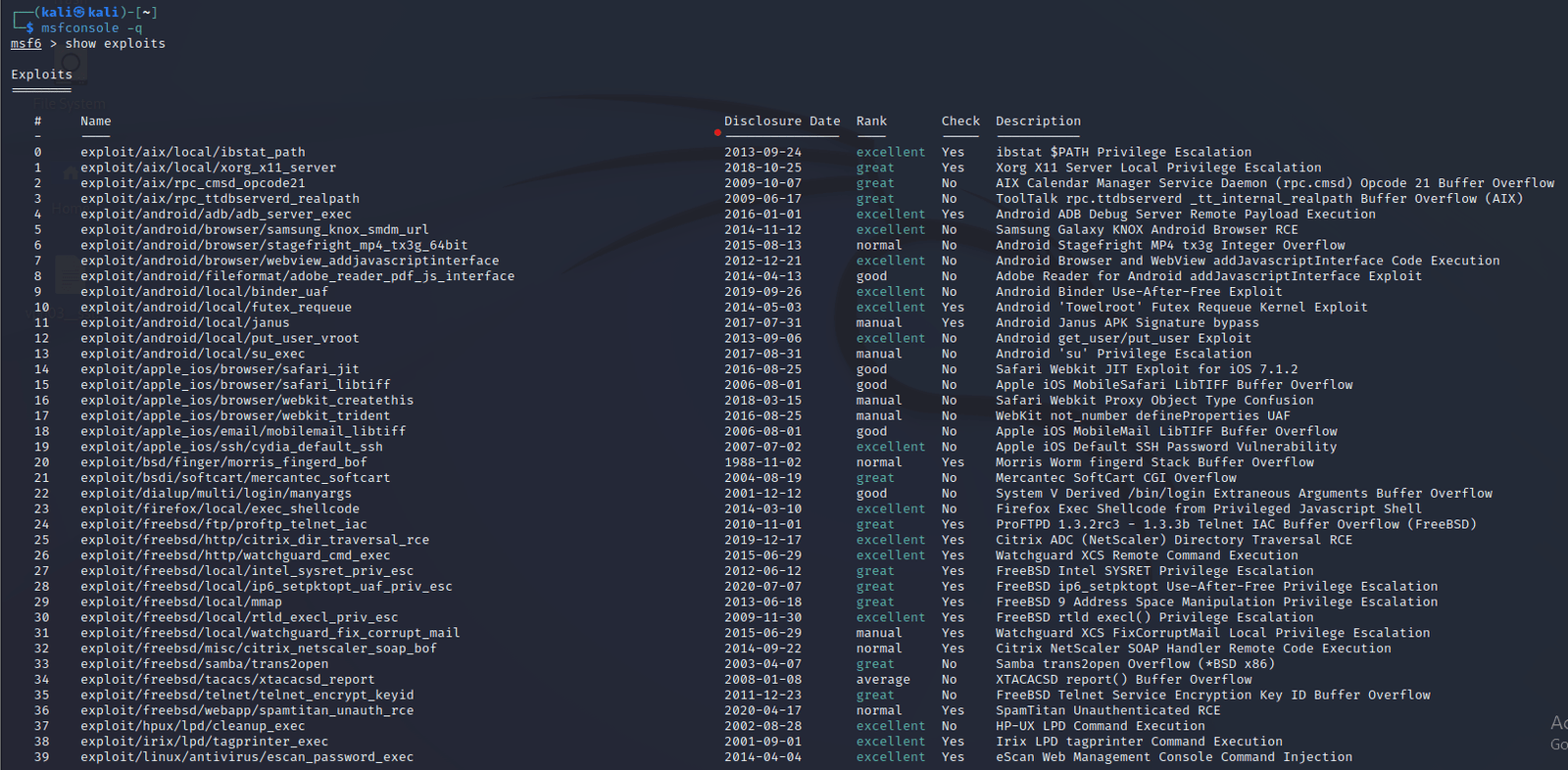
There are various exploits available for various software and can be viewed as,
Step 1: Open the terminal on kali and open Metasploit using “msfconsole –q” command to open metasploit silently.
Step 2: Once the metasploit starts, then write the command show exploits. Then it’ll display all the exploits available for various software.
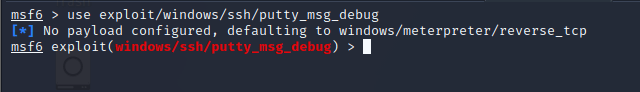
To use any module in metasploit, it’s required to use “use” command, and this will select the type of exploit , as
By using show options command, it’ll display the options that can be used to advance the type of attack.

- Auxiliary: Auxiliary modules are used to perform tasks that are not related to exploitation or payload delivery. These modules can be used to gather information about a target system, perform denial-of-service attacks, or brute-force passwords. Auxiliary modules are useful for reconnaissance and can help identify potential targets for exploitation.
To scan the ports of an IP using auxiliary can be achieved as:-
Step 1: Open Metasploit and search for port scan using “search portscan”.
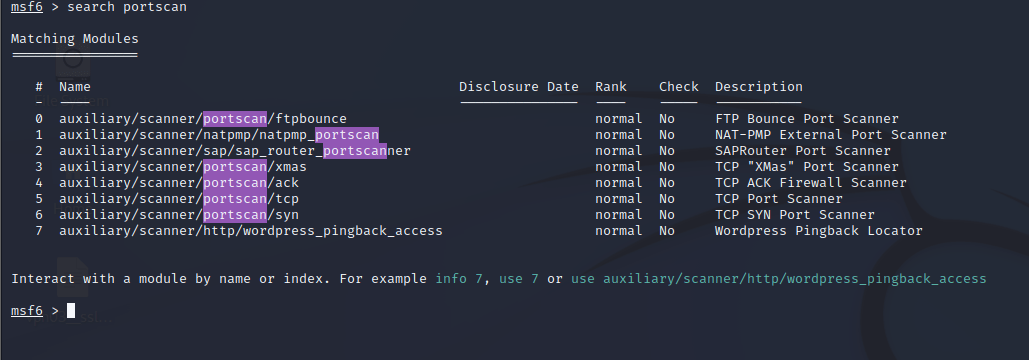
Step 2: Then it’ll display the various type of port scanning techniques, choose one of the type of scan (say tcp scan), and by using the show options command, it’ll display the modifications that are needed to be done.
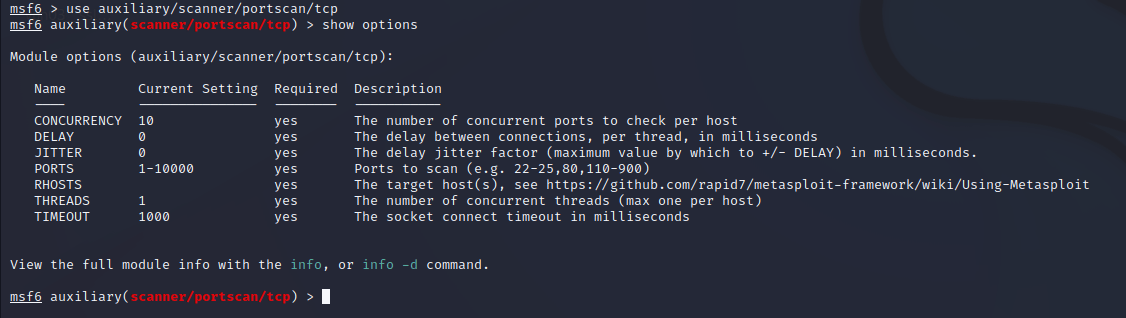
Step 3: Now, set the RHOSTS to the targeted IP and set the ports and threads as per the requirements, and then check for applied changes using the show options command.
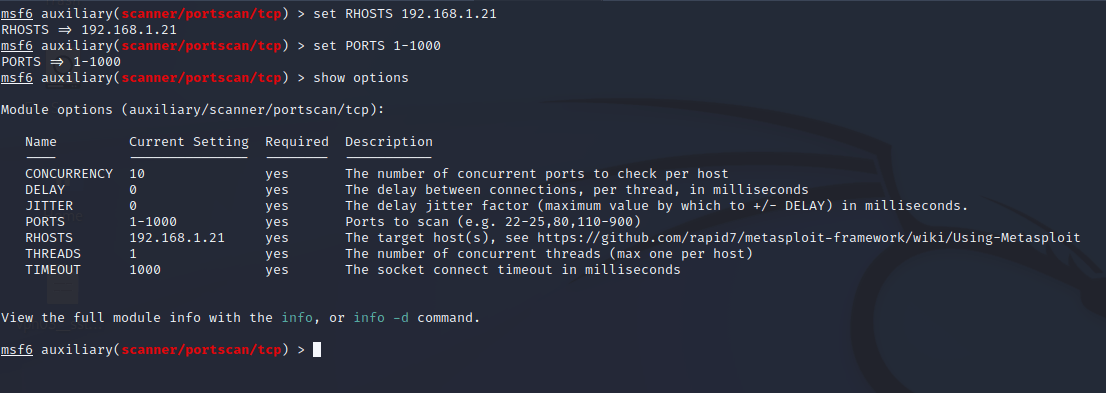
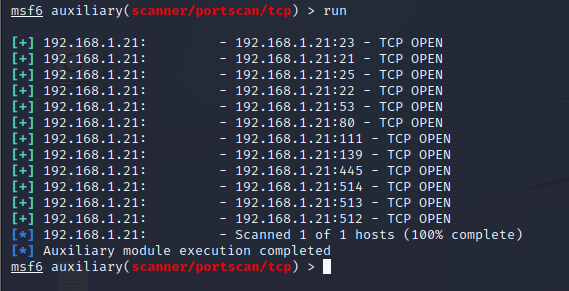
Step 4: Then give run command to scan for the open ports.
- Payloads: A payload is a set of instructions that are executed on a target system after a successful exploit. It’s the malicious program that allows hackers to obtain their objectives, such as opening a remote shell, downloading and executing files, or stealing data from the target system.
Metasploit’s payload module contains a variety of payloads that can be customized to suit specific targets and scenarios.
- Encoders: Encoders are used to obfuscate or encode payloads to avoid detection by antivirus software or other security measures. Metasploit’s encoder module contains several encoders that can be used to modify payloads to evade detection.
- Nops: Nops are small pieces of code that are used to pad the payload and ensure that it is properly aligned in memory. Metasploit’s nop module contains several nops that can be used to ensure that payloads are properly aligned and executed.
- Post-exploitation: Post-exploitation modules are used to maintain access and control of a compromised system after a successful exploit. These modules can be used to escalate privileges, add new user accounts, or install backdoors on the target system. Metasploit’s post-exploitation module contains several modules that can be used to maintain control of a compromised system.
Evasion: Evasion modules are used to bypass or defeat security measures that are designed to detect and prevent exploits. These modules can be used to modify payloads, change the order of commands, or use different methods of delivery to evade detection. Metasploit’s evasion module contains several modules that can be used to bypass antivirus software and other security measures.
Author
Abhi Gaur
(Cyber Security Intern)




