March 22, 2023 / By Securium Solutions
Description
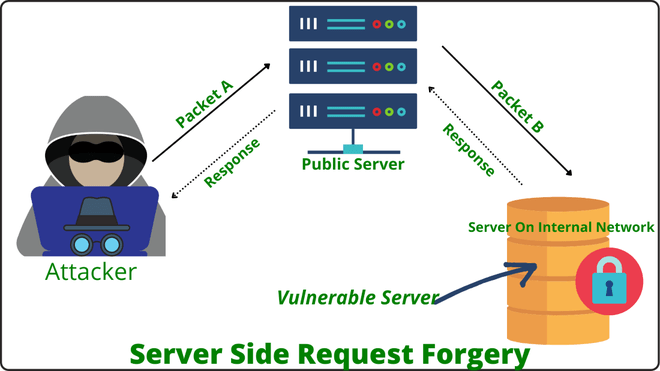
Server Side Request Forgery (SSRF) Attack is a security vulnerability that occurs when an attacker is able to send a request to a server from the server itself. This vulnerability can be exploited to gain unauthorized access to resources that should not be accessible from the server.
So thus, An SSRF Attack fault occurs when a web application retrieves a remote resource without checking the URL provided by the user. This enables an attacker to force a program to send a forged request to an unintended recipient, even when protected by a firewall, VPN, or some other type of network access control list.
Types of SSRF Attacks:-
- Basic SSRF:- In this type of attack, the attacker sends a request to the server to access a resource that is not intended to be accessible. The server will process the request and return the response, potentially revealing sensitive information or executing unauthorized actions.
- Blind SSRF:- This type of attack is similar to basic SSRF Attack, but the attacker is unable to directly view the response from the server. Instead, the attacker may need to use other techniques, such as timing attacks or error messages, to infer information about the response.
- Out Of Band(OOB) SSRF:-OOB Server Side Request Forgery Attack use the server to communicate with external systems, such as by making DNS queries or sending HTTP requests. This can be used to extract sensitive data or carry out other malicious activities.
- Intra-Protocol SSRF:-In this type of attack, the attacker sends a request to a server within the same protocol or application, such as by sending a request to a database server or web server within the same network. This can be used to bypass firewalls and other security mechanisms.
The following are some of the possible consequences of an SSRF attack:-
Access to Internal Systems: If a server is vulnerable to SSRF, an attacker can use it to access internal systems that are not meant to be accessed from the outside. This can give the attacker access to sensitive data, such as employee records or financial data.
Data Theft: An attacker can use SSRF to steal data from the server by requesting files or data from the server and sending them to a remote server controlled by the attacker.
Launching Further Attacks: Once an attacker gains access to a vulnerable server, they can use it as a launching pad for further attacks, such as spreading malware, launching DDoS attacks, or stealing credentials.
Mitigation
Input Validation: Input validation is a critical step in preventing SSRF attacks. All user input, including URLs, should be validated and filtered to ensure that they do not contain malicious code or requests.
Restricting Outbound Traffic: Outbound traffic should be restricted to only the necessary services and resources. This can be achieved through firewall rules and network segmentation.
Using Whitelisting: Whitelisting is an effective method for preventing Server Side Request Forgery Attack. By only allowing access to trusted resources, organizations can prevent attackers from exploiting SSRF vulnerabilities.
Patching Vulnerabilities: Vulnerabilities in software should be patched as soon as possible to prevent attackers from exploiting them.
Using Reverse Proxies: Reverse proxies can be used to prevent Server Side Request Forgery Attack by acting as a buffer between the user and the server. Reverse proxies can be configured to filter out malicious requests before they reach the server.
Author
Lokesh Yadav
(Cyber Security Intern)




