INTEGRITY SECURITY CHECKSUM
HEY EVERYONE,
Today Let’s pickup where we left from the Last blog of mine(RE by Algorithm).
What is Integrity checksum ?
It is a security plagiarism which works on hashes and Flag Register. If the Integrity is void it will return an error opening the application. Simply we can say if you modify the application like we did in Algorithm Reversing it will not work. That’s it. We will be looking after Four Registers i.e JE, JNE, JZ, JNZ
JE – JUMP IF EQUALS JNE – JUMP IF NOT EQUALS JZ – JUMP IF ZERO JNZ – JUMP IF NOT ZERO
REQUIREMENTS: SMAC ADDRESS CHANGER(For Demo), Olly Debugger.
STEP 1: We can Do the Reverse Engineering as same as we do with Algorithm reversing, but in case with ISC it will secure the application from being modified, lets take a look at this type.
STEP 2: Here I Installed SMAC and I installed and gave some Wrong Key to register.
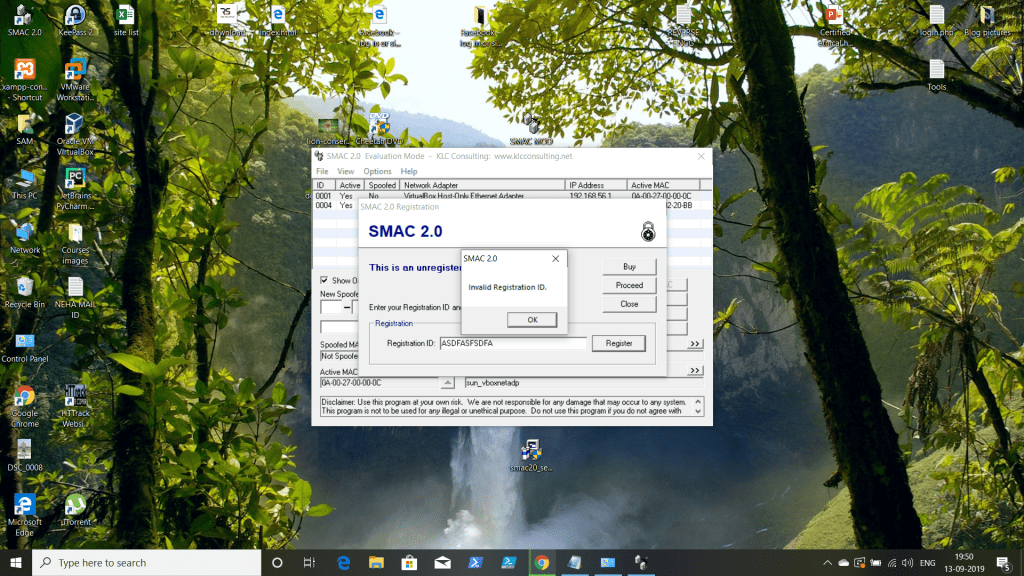
STEP 3: Copy the error and have in a text file, then Fire up OLLY debugger for Inspection and attach it.
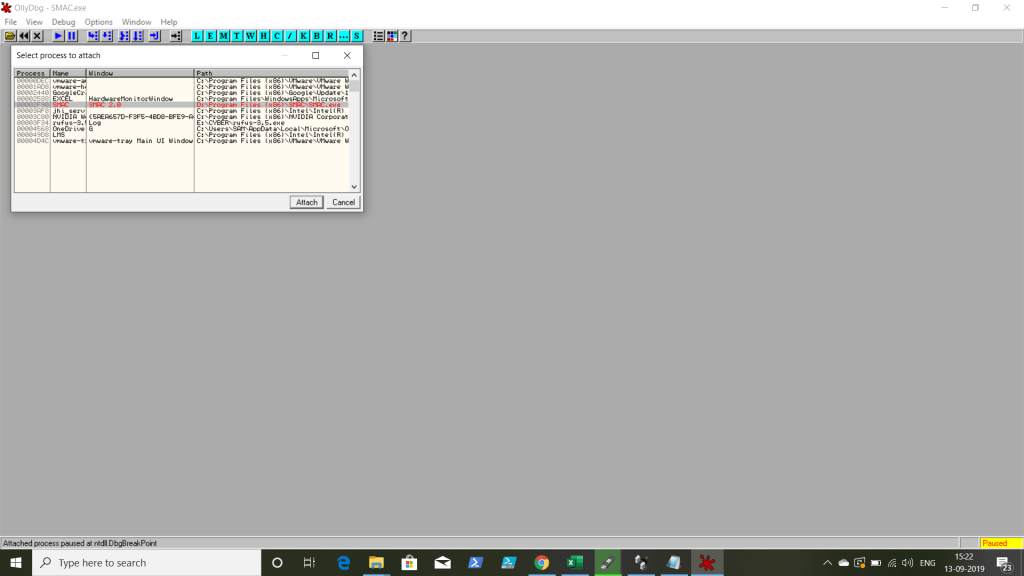
STEP 4: View–>Executables and select the SMAC application then press Enter. Then Click the play button only once.

STEP 5: Check for the referenced text strings, then search for the error.
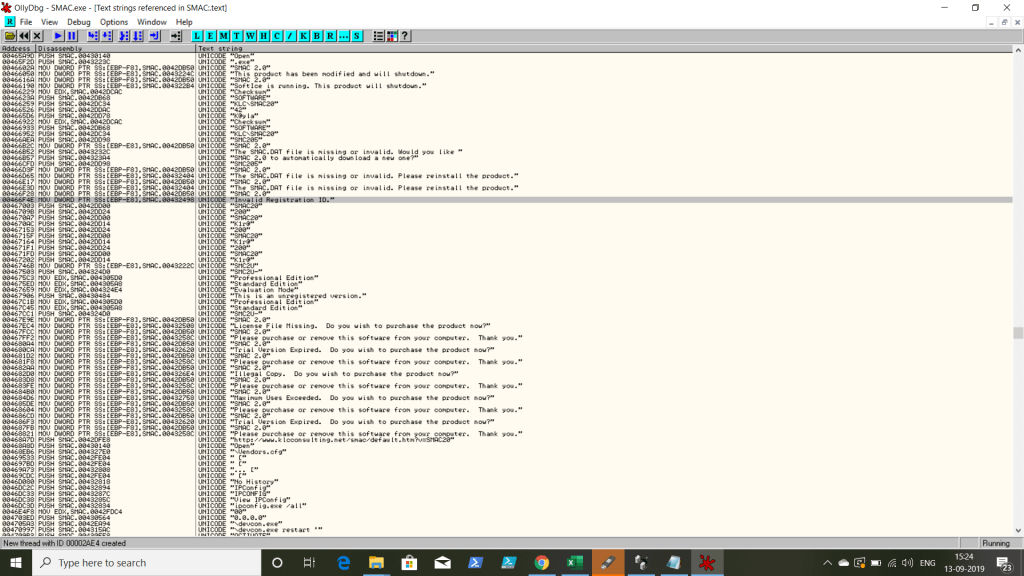
STEP 6: Try the algorithm reversing by changing the error message address to the successful one using JMP “ADDRESS”
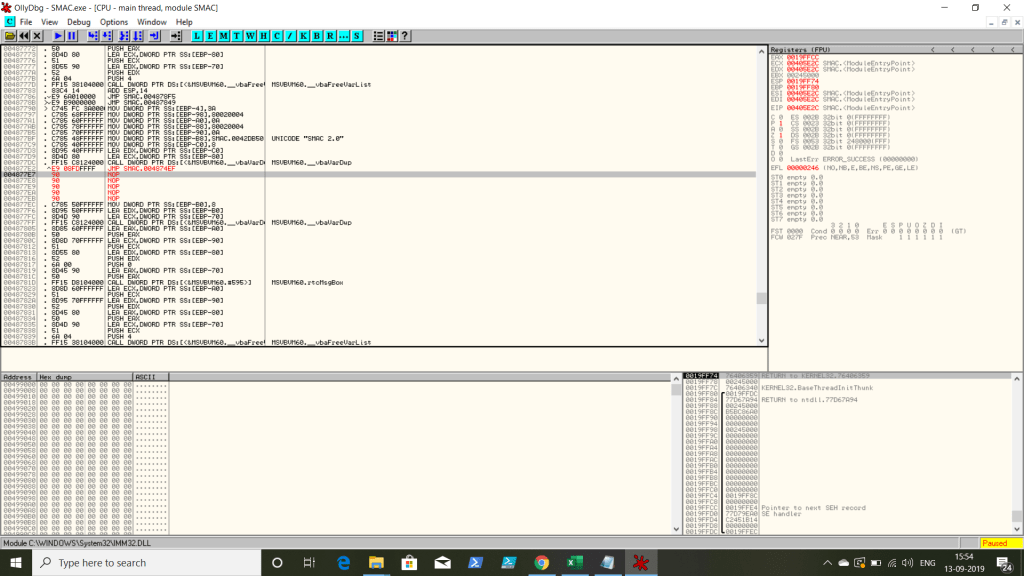
STEP 7: Copy the executable, then save the File with different name, then try running it.
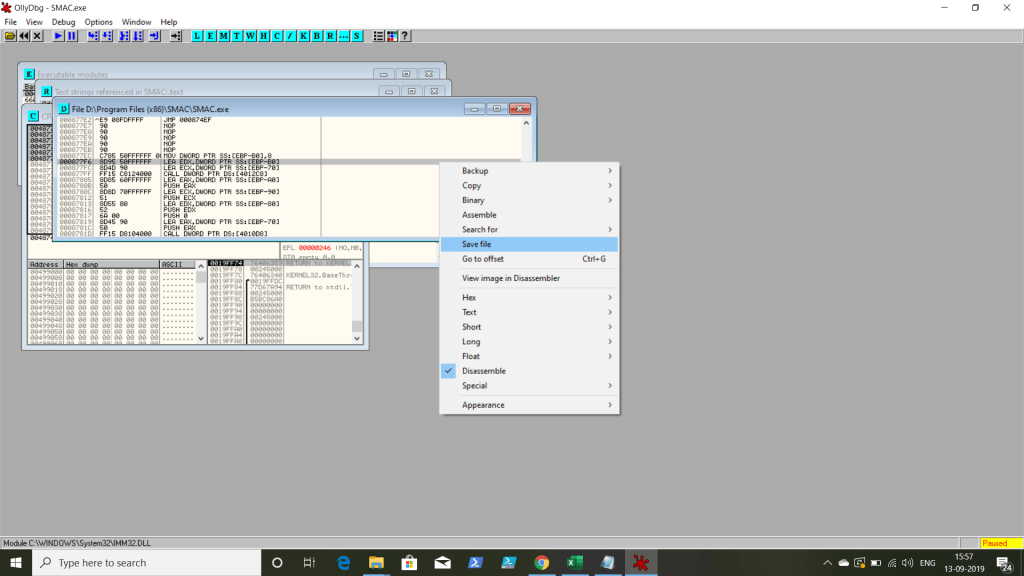
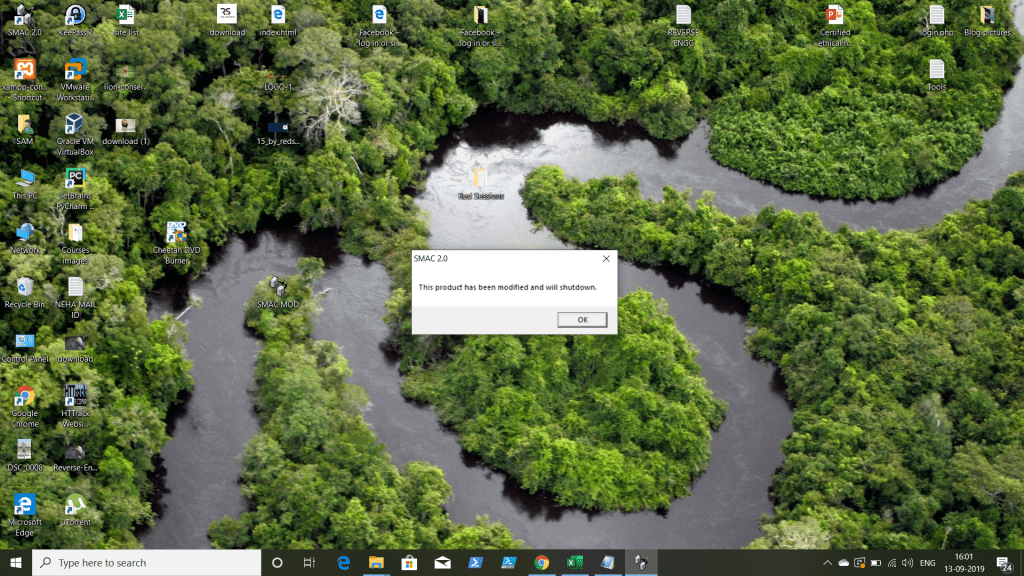
STEP 8: Now we are going to use the modified file with the OLLY debugger, this time don’t attach it open it.
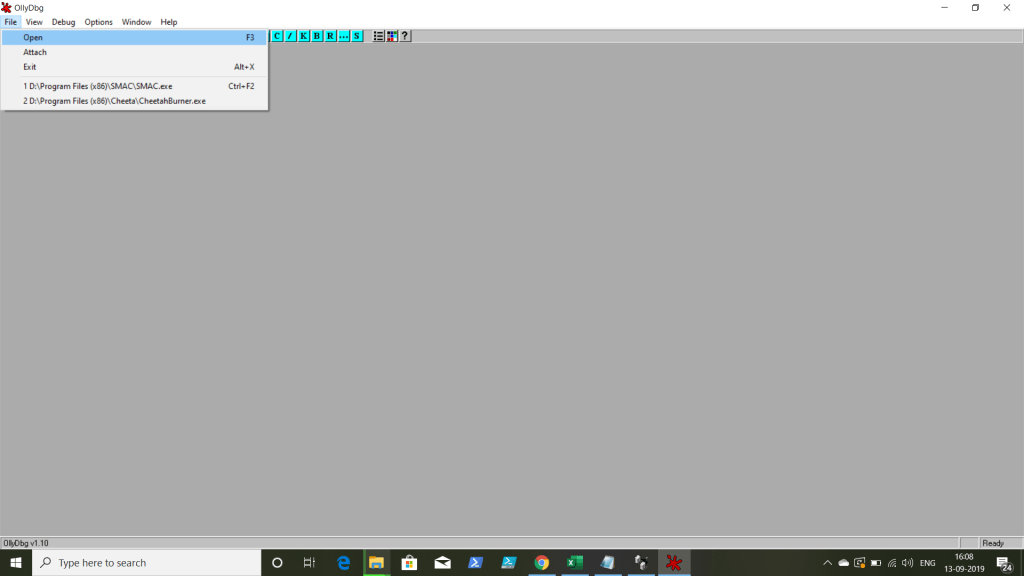
STEP 9: Now we can proceed with view executables, we shouldn’t click play button when we are playing with ISC. Then we can Search for the Referenced string, using error (latest one).
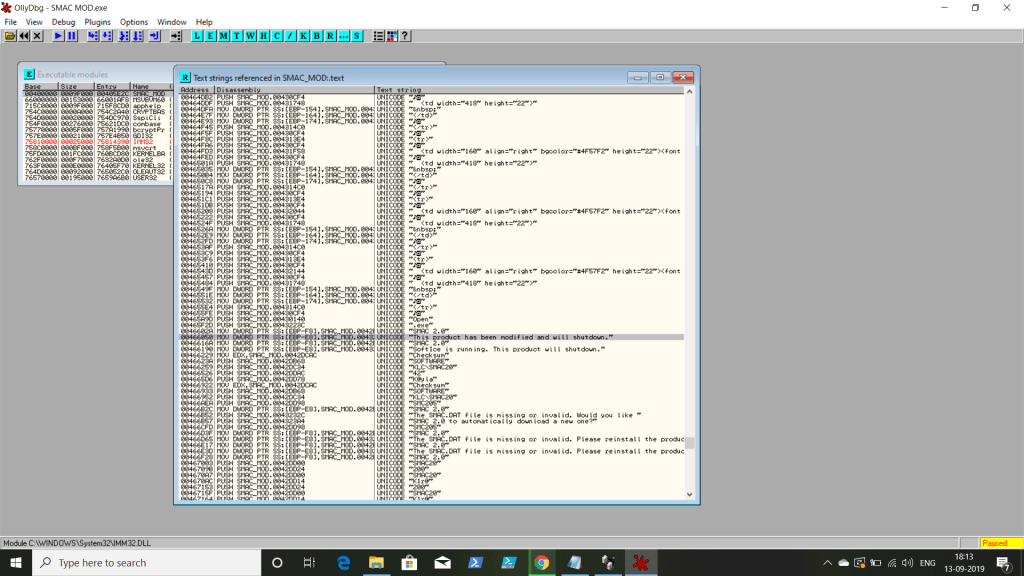
STEP 10: Double click the error to open the assembly page and look for ‘JE’ and ‘JNE’. why? Assume we are in 0 condition(False) i.e ‘JZ’ condition. Now just change the ‘JE’ register to ‘JNE’, now our condition automatically will proceed to ‘JNZ’ flag to make it as “True”.
STEP 11: Now as usual we can Copy the executables, save it and use it.
NOTE: YOU WILL BE FACING MANY FALSE ERRORS, FALSE SUCCESSFUL MESSAGES, KEYS, FIND THE REAL ONE. THEN EVERYTHING IS GOOD TO GO.
See you guys in next Blog 🙂



