May 03, 2023 / By Securium Solutions
Two types of User Accounts in Linux:
There are two main types of user accounts in Linux operating system –
1. Root account – Super user that have the highest privileges and have unlimited access and control of the system.
2. User account – Normal users that have limited privileges that can be defined by the root user.
When a shell is obtained, it is most likely to be of a user or a service that has limited privileges. To obtain full control of the system or to access any file, root privilege are required. Shell of the root user can be obtained by privilege escalation by the means of SUID and GUID.
What are SUID & GUID?
SUID (Set owner User ID up on execution) and GUID (Set owner Group ID up on execution) are permissions set on a binary execution. When a binary with SUID or GUID bit set is executed, it will execute with the privileges of the owner user or group. This can be exploited to gain shell of another user, preferably root.
How to Detect SUID and GUID for Privilege Escalation:
SUID – The “s” in the fourth character specifies SUID bit is set. This binary will execute as the root user which is the owner user of the binary.

GUID – The “s” in seventh character specifies that GUID bit is set. This binary will execute as the root group which is the owner group of the binary.

How to find binaries with SUID and GUID set?
Command to find all SUID binaries->
find / -perm -4000 -type f -ls 2>/dev/null
Here, we are using find command to search any file (“-type f”) with SUID bit set (“-perm -4000”) in the root directory (“/”) and discarding all errors caused by inaccessible directories to /dev/null. “-ls” will output the results in a list format with permissions displayed.
Similarly for GUID, -perm -2000 should be used.

How to Exploit SUID Binaries for Privilege Escalation:
There are certain binaries that will have SUID bit set in all Linux systems like su, sudo, passwd, and gpasswd. These are system binaries and are almost certainly secure. It is more likely to find a vulnerability in other non-system binaries.
Exact method of exploitation is varied between different binaries. Checking whether there is any exploitation method in GTFObins is a good start.
Some Practical Exploit Examples
Privilege escalation using functionality of SUID binaries (with Python) –
If python has SUID bit set, the following command can be used to spawn root shell.
python -c ‘import os; os.execl(“/bin/sh”, “sh”, “-p”)’

Privilege Escalation by Using Known Exploits (with exim) –
![]()
After a quick searching, exploit for CVE-2016-1531 can found. It allows privilege escalation in exim-4.84-3. Using the exploit results in the privilege escalation.

Privilege Escalation by Exploiting Relative Paths in SUID Binary Calls –
![]()
suid-env has SUID and GUID bit set and can be executed by anyone.

service binary is called to start apache2 but no absolute path is used. This can be exploited by compiling a new binary with the following C language code:
int main() {
setuid(0);
system(“/bin/bash -p”);
}
The name of the complied binary must be same as “service”.
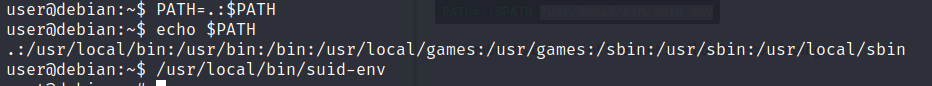
The current directory (the one with the complied C binary) is added to the PATH variable then suid-env is executed. Once it is executed, the operating system first checks our newly added entry to the PATH variable and executes our malicious “service” binary.
Author
Karan Sachdeva
Cyber Security Intern




