In this blog post we would like to introduce the pentesting framework for docker. The pentesting framework is used as a development and testing tool. For pentesting, the docker container image can be installed on a system such as our Ubuntu with root access or included in another container.
In this blog post we will explain what you need to do in order to get it up and running on your computer and show you how you can use it for pentesting purposes by installing a pentest framework into a Pentesting Docker container image.
In today’s post, we will learn how to install and use a pen-testing framework. We will set up a docker-based pen-testing environment for pentesters to make installing and configuring various pentesting tools simple and quick. Using pentesting framework we can perform a penetration test by using images that contain an automated attack system which includes tools such as nmap, sqlmap etc.
NMAP: Now let’s continue with our first pentest tool which is used to scan ports and IP addresses is known as Nmap. As a superuser, open your terminal on your local system and run the following command to download and build the docker package.
# docker pull instrumentisto/nmap

After pulling image of Nmap, we will use nmap docker image for network scanning using following command:
# docker run –rm -it instrumentisto/nmap -sV <ip>

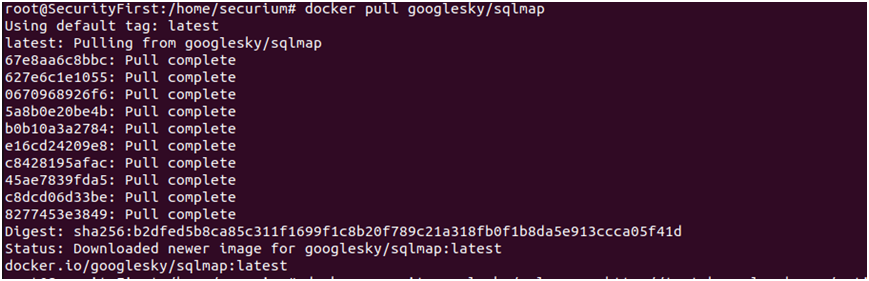
Sqlmap: Now we have already learned how to develop our own docking pentesting assessment framework. Our second pentest tool is Sqlmap which is used for SQL Injection testing on websites. Run the command given below to pull docker image of sqlmap.
# docker pull googlesky/sqlmap
Now we will use this docker image to do SQL Injection testing on our target website which is testphp.vulnweb.com
# docker run -it googlesky/sqlmap -u http://testphp.vulnweb.com/artists.php?artist=1 –dbs –batch

Metasploit: Next pentest tool is Metasploit. Metasploit is the most delegated and relevant tool for pentesting. Run the following command pull docker image of Metasploit docker in our local machine.
# docker pull metasploitframework/metasploit-framework

After pulling metasploit’s docker image, run the command given below in the terminal and we can see that it work exactly same as Ubuntu system.# docker run –rm -it -p 443:443 -v ${PWD}:/root/.msf4 metasploitframework/metasploit-framework

Dirbuster: Move on to our next pentest tool which is “Dirbuster”. Dirbuster scours the web pages and we directories for sensitive data hidden within the web application. To get the Dirbuster docker image, type the following command:
# docker pull hypnza/dirbuster

To start testing for enumeration of web pages and web directories using docker image of dirbuster, we will run the following command:
# docker run -it hypnza/dirbuster -u http://testphp.vulnweb.com/

John the Ripper
Next pentest tool is John the Ripper tool. It is a passwod cracking and hash cracking tool. By executing the given commnd we will pull the docker image of Johntheripper tool.
# docker pull obscuritylabs/johntheripper

Now if we have a hash file in our machine, we can crack the password from this hash file by running the following command:
#docker run –rm -it -v ${PWD}:/root obscuritylabs/johntheripper –format=NT /root/hash
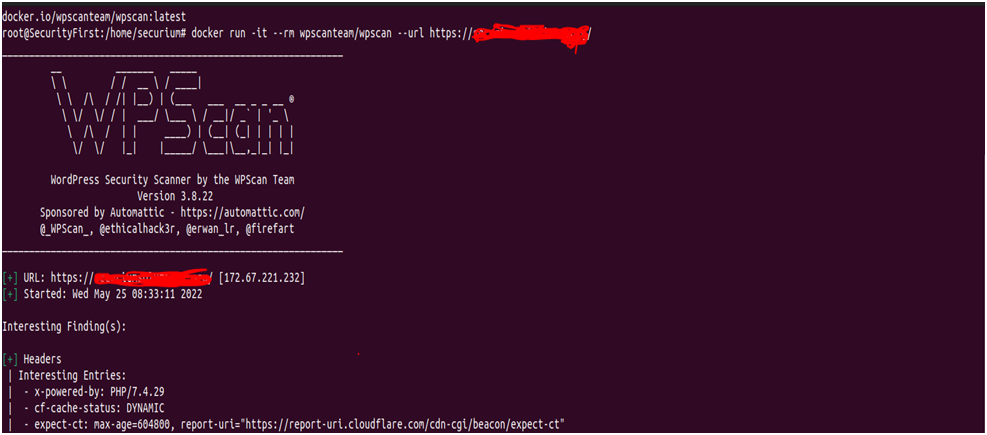
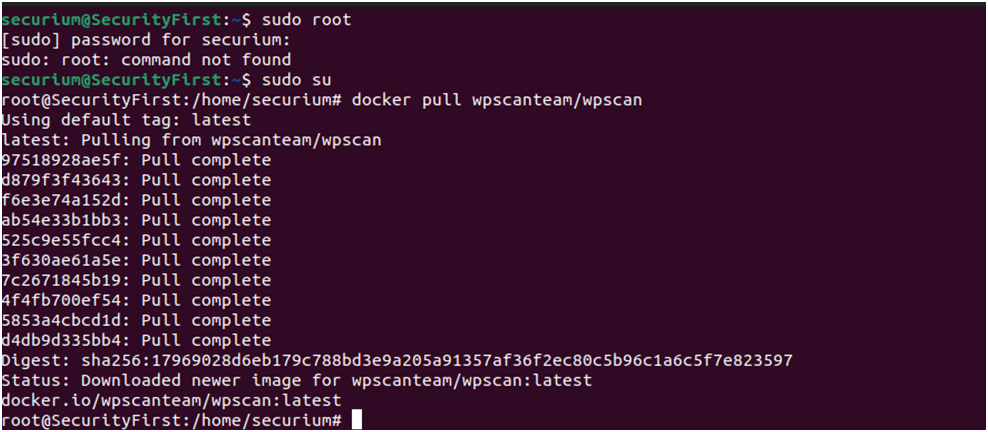
WPScan: Last but not the least pentesting tools are WPScan which is used to scan the WordPress website. We can pull the docker image of WPScan by running the following command:
# docker pull wpscanteam/wpscan
After getting the image, we can start pentesting of WordPress by running the following command:
# docker run -it –rm wpscanteam/wpscan –url <URL>