Spanning Tree Protocol?
Spanning Tree Protocol (STP) is a networking protocol that prevents loops in network topology by disabling redundant paths and determining the shortest path to the root bridge. This is done by electing a root bridge and calculating the shortest path to it, using factors such as port cost and priority. Spanning Tree Protocol is a critical protocol in network infrastructure, but it also has vulnerabilities that can be exploited by attackers. It is essential to configure STP correctly and implement security measures to prevent STP attacks, such as disabling unused switch ports, enabling port security, and using BPDU guard and root guard.
Is it a spanning Tree Protocol attack?
Spanning Tree Protocol (STP) attacks exploit vulnerabilities in the protocol to create network loops or bring down the network. Attackers can use a variety of methods, such as sending malicious Bridge Protocol Data Units (BPDU), to interfere with the STP calculations and force the network to use a sub-optimal path or even create a loop. STP attacks can cause network congestion, broadcast storms, and even network failures, which can have severe consequences for organizations. To prevent STP attacks, network administrators should disable unused switch ports, enable port security, and use BPDU guards and root guards.
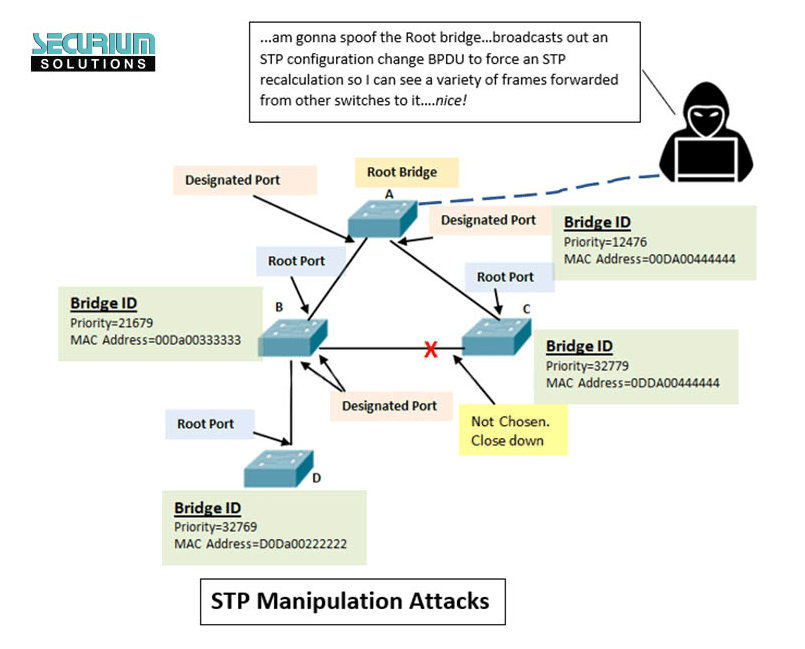
Example of an STP attack
In the following example, we will simulate an STP attack using Cisco Packet Tracer.
The network topology consists of three switches, with Switch 1 being the root bridge.
Step 1: The attacker connects to the network through Switch3.
Step 2: The attacker sends fake BPDU messages to the switches, pretending to be the root bridge.
Step 3: The switches receive the fake BPDU messages and recomputed the network topology, with Switch3 becoming the new root bridge.
Step 4: A network loop is created, causing network disruptions.
An STP Attack
First, the attacker gains access to the network.
Second, the attacker sends malicious Bridge Protocol Data Units (BPDU) packets.
Third, the BPDU packets alter the STP topology information.
Fourth, the network is forced to use a sub-optimal path or even create a loop.
Finally, the network experiences congestion, broadcast storms, or even failure. STP attacks can have serious consequences for organizations, including loss of data and downtime. To prevent STP attacks, network administrators should disable unused switch ports, enable port security, and use BPDU guards and root guards.
Preventing STP attack
- Disable unused switch ports.
- Enable port security.
- Use BPDU guard and root guard.
- Configure STP parameters carefully.
- Monitor the network for suspicious activity.




