Greeting Everyone! Hope All going well today in this blog we are about to learn how to use Hashcat with practical scenario Hashcat is one of the best and most powerful tools which is used for cracking hashes. Now we are going to learn how to use hashcat cracking tool in simple steps which will help you in your cryptography journey.
1. Identify hash type – when we going to crack the hash we need to know the type of particular hash.
Unix style password hashes tools are very easy to recognize, as they have a prefix. The prefix tells you the hashing algorithm used to generate the hash. The standard format is $format$rounds$salt$hash.
Example sha-512 – $6$pKyalkutOw0Tqq0u$4j18Lbicto3.
Windows passwords are hashed using NTLM, which is a variant of md4. They’re visually identical to md4 and md5 hashes, so it’s very important to use context to work out the hash type.
| Prefix | Algorithm |
| $1$ | md5crypt, used in Cisco stuff and older Linux/Unix systems |
| $2$, $2a$, $2b$, $2x$, $2y$ | Bcrypt (Popular for web applications) |
| $6$ | sha512crypt (Default for most Linux/Unix systems) |
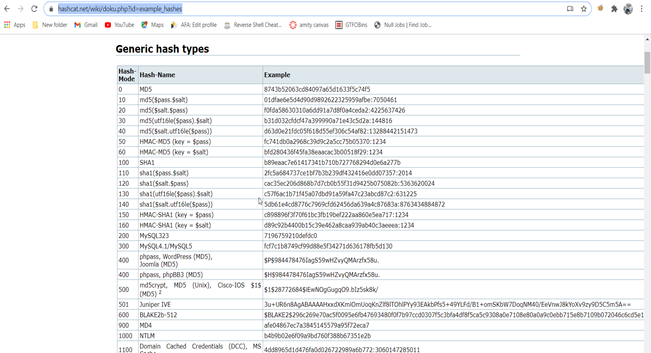
Now we know how to identify hash but where we can identify the hash. For identify hash go to website –> https://hashcat.net/wiki/doku.php?id=example_hashes
Example:-”$6$GQXVvW4EuM$ehD6jWi
MsfNorxy5SINsgdlxmAEl3.yif0/c3NqzGLa
0P.S7KRDYjycw5bnYkF5ZtB8wQy8Knsku
WQS3Yr1wQ0”
Now take the prefix from hash for example sha-512 hash prefix is $6$ go to website press Ctrl+f and put $6$ and take the hash-mode 1800 from first column.

2. Crack the hash –> Put hash into the file I give the name of file hash.txt Hashcat powerful cracking tool use certain keywords like ( -a -m –force )
| Tag | Information |
| -a | It use for give the attack-mode |
| -m | It use for give the hash-mode of hash |
| –force | Hashcat crecking tools will work without using of GPU. UPDATE: As of Kali 2020.2, hashcat 6.0 will run on the CPU without –force. I still recommend cracking on your host OS if you have a GPU, as it will be much much faster. |
hashcat -a 0 -m 1800 hash.txt /usr/share/wordlists/rockyou.txt –force

Now hash is cracked by powerful cracking hashcat powerful tool and we got the password spaceman
$6$GQXVvW4EuM$ehD6jWiMsfNorxy5SI
NsgdlxmAEl3.yif0/c3NqzGLa0P.S7KRDYjy
cw5bnYkF5ZtB8wQy8KnskuWQS3Yr1wQ0
:spaceman
I attached for you some hash try to crack this.
$2a$06$7yoU3Ng8dHTXphAg913cyO6B
js3K5lBnwq5FJyA6d01pMSrddr1ZG
$1$VvsOtV46$afqpbBUvmX.2jVjtxoFkt/
Happy Hacking !!!
Stick With Our Blog : https://securiumsolutions.com/
Author : Shubham Jaiswal (WAPT Intern)




