In previous blog we performed firmware analysis, which gave us an idea about device’s file system, OS, sensitive files, hardcoded credentials, services and softwares running, among other things. Next, what we need to do and will be doing is “firmware simulation” which can be browser based, allowing us to-do web app based exploitation or CLI based.
Browser based Firmware Simulation:
What we will actually do is we use the tool fat.py (firmware-analysis-toolkit) on our command line, then provide name of the firmware image to simulate (have it copied to the dir of fat).
Fat.py might ask for some passwords (in old versions of attifyos) while running, following are the credentials:
- firmadyne:firmadyne
- attify:attify
- attify:attify123
If everything goes well, we will see a CLI message informing that a network interface is started. If not, then try to re-run the fat.py or try googling the error or better try other firmware.
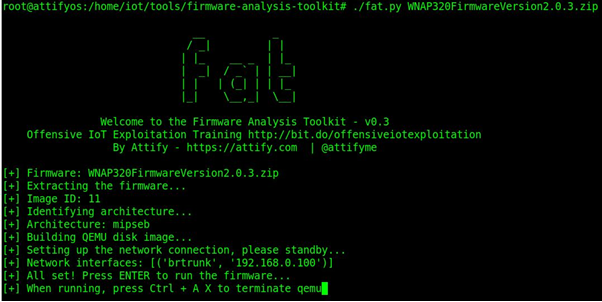
And with this we have successfully simulated our firmware via browser, just go to the IP provided on your CLI, mine is 192.168.0.100, open it in browser, and you will see the router’s homepage (as I’ve done simulation for router’s firmware).

Here, you can try to brute force the password with Burp or try some common pairs like admin:admin, admin: , admin:password.
Note: admin:admin is the pair to go here.
With this, we are inside the router’s homepage, try browsing different settings like
- default wifi password and name
- services like ssh,telnet which are running by default and their creds
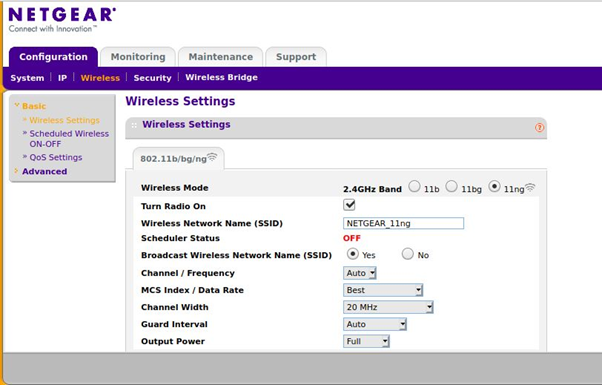
Lets go to the attack phase, try scanning the ip with nmap to see ports open, find exploits for those services and execute them in our controlled environment.
Note: With firmare simulation we are preparing our attack to almost perfect by attacking in our controlled environment, having access to victim’s device(via simulation), we can also see what effects our attack has on target device and what preventive measures to follow. After perfecting the attack, we will just execute it on target with higher chance of success.

Also try to perform common web app based attacks like OWASP top 10 to find any vulnerabilities. Use routersploit/msfconsole to exploit device.
Terminal Firmware based simulation
This is an alternative to browser simulation( this is the better one ) where we use busybox to run router’s commands from our CLI as seen below after going to the dir where its present in the firmware.
“BusyBox is a software suite that provides several Unix utilities in a single executable file. It provides replacements for most of the utilities you usually find in linux. One can extremely customize the commands on needs. BusyBox provides a fairly complete environment for any small or embedded system.
BusyBox has been written with size-optimization and limited resources in mind.
”
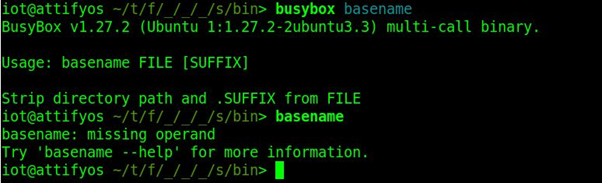
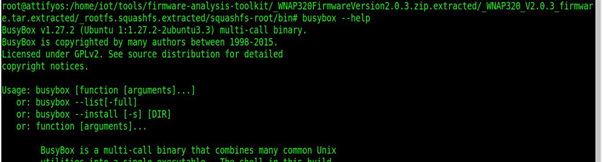
Use “busybox –help” command to know allowed commands in the firmware, explore it & exploit it.
Conclusion:
This concludes this article, here we learned what is firmware simulation, how to perform it, whys its done and its different types. In our next blog we will be talking about firmware backdooring so do check that out.
Authors: Vishal Thakur & Mohammad Usman Rais | Network Security Analyst Interns



