What is SNMP?
SNMP (Simple Network Management Protocol) is used for the management and monitoring of devices in a network. This protocol allows to read and modify configuration settings remotely in routers, switches, firewalls, and other network devices. It can also be embedded in Windows and Linux servers.
SNMP uses UDP port 161 and 162 by default.
How many SNMP Versions are there?
There are 3 versions of SNMP currently existing
1. SNMPv1 – Version 1 was the first implementation and used community strings as means of authentication.
2. SNMPv2c – Version 2 included enhanced functionality but still used community strings as an authentication method.
3. SNMPv3 – Version 3 added encryption and credential-based authentication making it the most secure version of SNMP.
Even though v3 is the most secure version, v1 and v2c are being still used in many networks.
What are Community Strings?
Historically “community string” were used instead of user credentials. Using community strings which functioned as both username and password had either read-only or read-write privileges. SNMPv1 and v2c uses these.
What are OIB (Object Identifiers)?
OIDs are unique addresses to identify managed objects in the hierarchy of a device. Each OIDs contains a value that represents the settings or status of a device. OID is a combination of numbers separated by dots. These OIDs can also be used to set a value.
Exploitation of v1 and v2c –
The exploitation of v1 and v2c is the same as they both use community strings for authentication. Since only community strings are needed, they are vulnerable to brute-force attacks.
Before brute-forcing the first step should be to try the default community strings, which are –
1. public – this is a default read-only community string.
2. private – this is a default read-write community strings.
They might be enabled and should be tried first before brute forcing for the community strings.
Since there are many tools to brute force, I will be mentioning two methods of doing so.
1. Metasploit – The module for this is
“auxiliary/scanner/snmp/snmp_login”
2. Nmap – The command of this is
“nmap -sU -p <> -n –script snmp-brute <ip> –script-args snmp-brute.communitiesdb=<wordlist>”
Note- Wordlists can easily be found on Github or other websites. If they do not work, you can generate your own wordlist.
Other than brute force, v1 and v2c are also vulnerable to sniffing attacks since they do not implement any encryption.
Considering you now have obtained community strings (preferably with read-write access), there are some tools that are very useful from here.
1. snmpwalk-
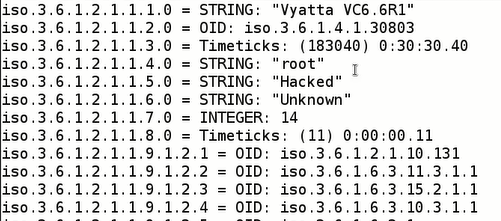
Running this command will retrieve all OIDs and their values. For example, the output of the command will be like:
Syntax – “snmpwalk -v -c <community_string> <ip>”

2. snmpget-
Similar to snmpwalk, there is snmpget. snmpget only retrieves value of the OIDs you specified not the complete output.
3. snmpset-
snmpset allows us to change the value of the specified OID.
Syntax – “snmpset -v -c <community_string> <ip> <iso> <s> Hacked”
Alternatively, nmap contains some specific scripts as well
–script=”snmp-interfaces” –script-args=”snmpcommunity=<>”
–script=”snmp-netstat” –script-args=”snmpcommunity=<>”
–script=”snmp-processes” –script-args=”snmpcommunity=<>”
Exploiting SNMPv3-
Brute forcing SNMPv3 does not necessary mean to brute force both username and password at the SNMP port. v3 uses MD5 or SHA1 algorithm for encryption and capturing a single SNMPv3 packet is all that is needed. Both Hashcat as well as John The Ripper are capable of decrypting the encrypted v3 password.
Author
Karan




