Greeting Everyone ! Hope Everything is going well And Good ! Today In this blog We will discuss Different Techniques to utilize Web Content Discovery Phase If your doing Web Application Penetration Testing This step must important Before Go further So Here we will cover 5 most Common Technique That help us In Our Content discovery Phase .
Content discovery This phase can be used to discover content and functionality which is not linked from visible content for all users that you can browse to or spider. In this phase we will use use different Techniques to discover hidden content Against Our Web Application .,
Techniques / tool
- Dirb
- Dirsearch
- Arjun
Dirb
Dirb is kali based cli tool which is design to Implement testing phase and able to look for valid hidden directory of our targeted website . dirb will make a http request and it will give as result with http request according to directory structure 200, 403, 302 with respective http code .
Usage : This tool default with kali linux, parrot To run this command Open your kali terminal ,
Use command: dirb (to see all flag that we will use )

As above picture we able to see flag and basic command structure for dirb tool,
Now , How to implement scanning phase against target ,
Use command : dirb http://target.com

As above picture we see We got some hidden directory structure with their response code . This tool really help you to discover hidden directory folder against Your targeted website .
Dirsearch
Dirsearch which functionality same as dirb , Dirsearch is based on command-line tool designed to brute force directories and files in webservers and able to manipulate hidden directory structure.
Usage Of dirsearch:
Installation :
git clone https://github.com/maurosoria/dirsearch.git
cd dirsearch
python3 dirsearch.py -u <URL> -e <EXTENSIONS> eg: aspx,php,josn,xml
Now to check Functionality of dirsearch tool we will use command
Command used : ./dirsearch -h

As above picture we able to see flag and basic command structure for dirsearch tool,
Now , How to implement scanning phase against target ,
Use command : ./dirsearch -u www.target.com -e aspx.json,xml,php
As here we used flag -u which define our targeted website /url and -e define that extensions we are going to bruteforce .

As above picture we see it bruteforce against all directory with huge wordlist and this tool also give result with their respective code eg : 200 that mean directory is accessable , 403 that mean directory can’t be accessable , 302 it redirecting .

As above picture we got response code with 200 that mean directory’s are access able for everyone which we found by discovery hidden content .
Arjun tool
Arjun is cli based tool which help to find our all hidden parameters against our target website . Arjun helps to passively extract parameters from JS . If your doing web application penetration testing arjun tool help us to manipulate all the hidden parameter’s which carries juice information .
Usage Of Arjun: Now to check Functionality of dirsearch tool we will use command
Command used : pyhton3 arjun.py -h
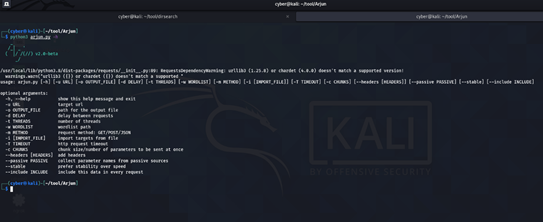
As above picture we able to see flag and basic command structure for dirb tool,
Now , How to implement scanning phase against target ,
Use command : pyhton3 arjun.py -u www.target.com
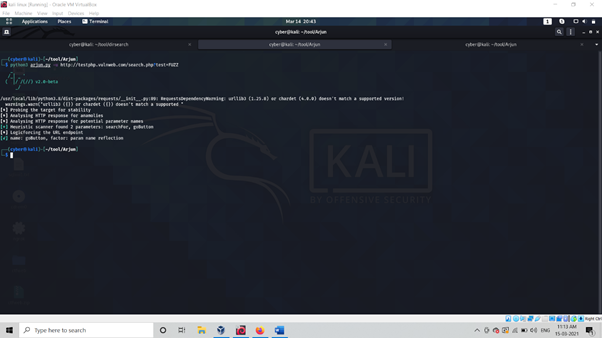
As above picture we see Arjun successfully find out hidden parameter value against our targeted website .
Conclusion : In this Blog we discussed some tools such dirb , dirsearch, arjun and we see how this tool help us to discover hidden content against our targeted website . We found directory structure using dirb and dirsearch tool and we found hidden parameter using arjun tool .
Thanks For Reading……. See You In Another Blog!
Stick With Our Blog : https://securiumsolutions.com/
Author : Pallab Jyoti Borah | VAPT Analyst



