Hello Everyone,
Hope you are doing well…
Today we will discuss about Clickjacking with form input data prefilled from a URL parameter
What is Clickjacking?
Clickjacking is an attack that tricks a user into clicking a webpage element which is invisible or disguised as another element. This can cause users to unwittingly download malware, visit malicious web pages, provide credentials or sensitive information, transfer money, or purchase products online.
What is the impact of a successful Clickjacking attack?
The user assumes that they’re entering their information into a usual form but they’re actually entering it in fields the hacker has overlaid on the UI. Hackers will target passwords, credit card numbers and any other valuable data they can exploit.
There are several variations of the clickjacking attack, such as:
- Likejacking – a technique in which the Facebook “Like” button is manipulated, causing users to “like” a page they actually did not intend to like.
- Cursorjacking – a UI redressing technique that changes the cursor for the position the user perceives to another position. Cursorjacking relies on vulnerabilities in Flash and the Firefox browser, which have now been fixed.
Clickjacking attack example
- The attacker creates an attractive page which promises to give the user a free trip to Tahiti.
- In the background the attacker checks if the user is logged into his banking site and if so, loads the screen that enables transfer of funds, using query parameters to insert the attacker’s bank details into the form.
- The bank transfer page is displayed in an invisible iframe above the free gift page, with the “Confirm Transfer” button exactly aligned over the “Receive Gift” button visible to the user.
- The user visits the page and clicks the “Book My Free Trip” button.
- In reality the user is clicking on the invisible iframe, and has clicked the “Confirm Transfer” button. Funds are transferred to the attacker.
- The user is redirected to a page with information about the free gift (not knowing what happened in the background).
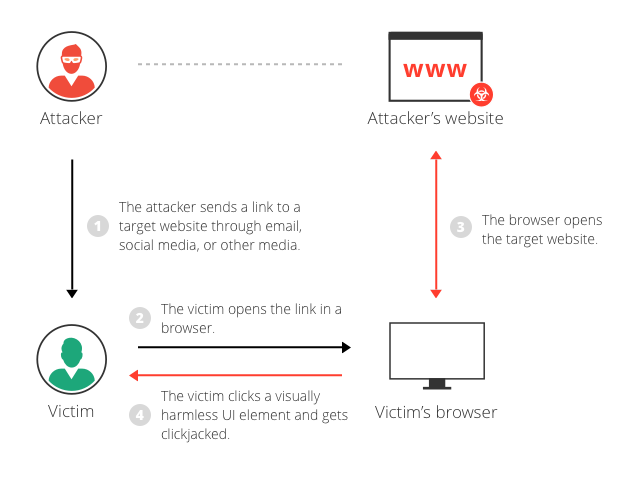
This example illustrates that, in a clickjacking attack, the malicious action (on the bank website, in this case) cannot be traced back to the attacker because the user performed it while being legitimately signed into their own account.
Clickjacking mitigation
There are two general ways to defend against clickjacking:
Client-side methods – the most common is called Frame Busting. Client-side methods can be effective in some cases, but are considered not to be a best practice, because they can be easily bypassed.
Server-side methods – the most common is X-Frame-Options. Server-side methods are recommended by security experts as an effective way to defend against clickjacking.
STEP 1-
- Log in to the account on the target website.

USERNAME – wiener, Password – peter
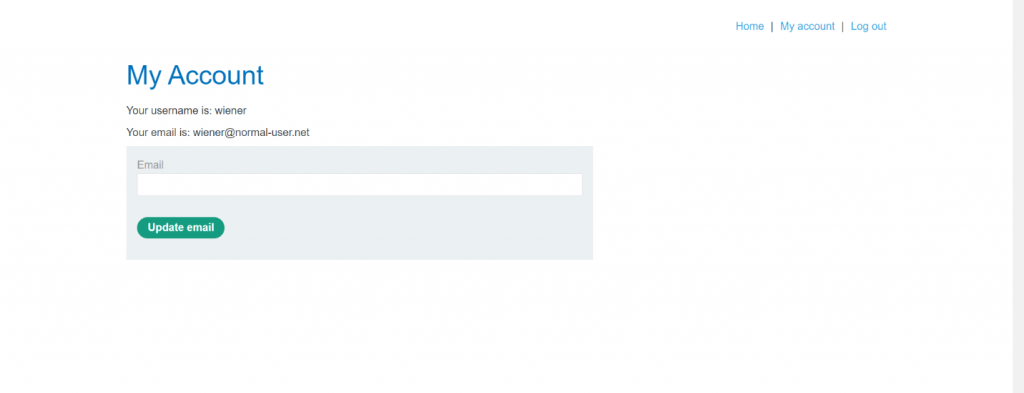
STEP – 2
Go to the exploit server and paste the following HTML template into the “Body” section :
<style>
iframe {
position:relative;
width:$width_value;
height: $height_value;
opacity: $opacity;
z-index: 2;
}
div {
position:absolute;
top:$top_value;
left:$side_value;
z-index: 1;
}
</style>
<div>Test me</div>
<iframe src=”$url?email=hacker@attacker-website.com”></iframe>

STEP – 3
Make the following adjustments to the template:
- Replace $url with the URL of the target website’s user account page, which contains the “Update email” form.
- Substitute suitable pixel values for the $height_value and $width_value variables of the iframe (we suggest 700px and 500px respectively).
- Substitute suitable pixel values for the $top_value and $side_value variables of the decoy web content so that the “Update email” button and the “Test me” decoy action align (we suggest 400px and 80px respectively).
- Set the opacity value $opacity to ensure that the target iframe is transparent. Initially, use an opacity of 0.1 so that you can align the iframe actions and adjust the position values as necessary. For the submitted attack a value of 0.0001 will work.

Step – 4
Click “Store” and then “View exploit”.
STEP – 5

Hover over “Test me” and ensure the cursor changes to a hand indicating that the div element is positioned correctly. If not, adjust the position of the div element by modifying the top and left properties of the style sheet.
STEP – 6
Once you have the div element lined up correctly, change “Test me” to “Click me” and click “Store”.

How to prevent Clickjacking Attack.
Here are four ways to prevent your business and employees from becoming part of a clickjacking scam:
Protect the Browser First
In order to prevent your organization from falling prey to this type of attack, you must start with the browser. The most likely scenario is that your users will become clickjacking victims during their normal Web activities. One way to reduce risk is to evaluate and install browser plugins such as NoScript and NotScript, which prompt users to allow javascript actions on sites they visit, as well as specify trusted domains. Some users can be put off by this, but most are becoming sensitive to the amount of cybercrime out there and appreciate the measures companies take to protect them.
This action is less time consuming than others and can greatly reduce risk from the onset.
Take the X-Frames Option
Most common browsers, including Microsoft IE, Google Chrome, Apple Safari and Firefox, support the HTTP Header X-FRAME-OPTIONS check, allowing the host to specify whether or not it is another page to frame it or not. You can take advantage of this functionality by specifying your webserver to send an X-FRAME-OPTIONS response header with the value “DENY.” You can read more on the X-FRAME-OPTIONS response header here.
Also, you add javascript in your source code to check and see if your site is framed. Many IT departments are large enough and experience enough turnover this this is piece of information can go unnoticed unless someone specifically asks about it.
Splurge on Web Application Firewalls
Web Application Firewalls (WAFs) will prevent someone from interjecting your site and inputting code. But organizations still put this in the “like to have” category instead of “need to have.” Why? Because they are expensive and take a lot of time to manage. They are well worth it. Recent data has shown that nearly 70 percent of all SMBs were hacked in some capacity in 2010. If you can’t build and maintain firewalls for your organization, by lack of sheer resources, consider outsourcing to the pros. It can take a huge burden off your plate, greatly reduce risks (of all kind) and may cost less than you think.
Evaluate Email Protection
Install and implement a strong email spam filter, and check it often. A clickjacking attack usually begins by tricking a user through email into visiting a malicious site. This is largely accomplished through forged or specially crafted emails that look completely authentic. By blocking illegitimate emails, you reduce a potential attack vector for clickjacking and a slew of other attacks as well. You’ll need to warn your employees that this measure has been taken so they regularly check their junk mail.
Some hacks steal data right from the company’s private networks, while others destroy the company from the outside in by way of victimizing site visitors. This is one of those hacks, and it can be extremely damaging to a company’s brand. A few simple steps can significantly lessen the likelihood that your visitors will become clickjacking victims.
Thank-you for your time.



