Greeting Everyone! Today In This Blog we will Explore Another XSS Victor Which Is Possible through SVG file Upload Functionality Due To Improper Validation Of file it got Executed to Our Backend Server.
As You guys Know about What is XSS We have already discussed Previously about Different XSS Attack Previous Blog.
Today In This Blog We Will See How Due to SVG How it possible for Stored XSS.
Every Web Application has Upload Functionality In Some cases Upload Functionality Fail to Protect Against data validation which user Uploaded And As Result User Script Got Executed To it server. File upload vulnerability is a vulnerability where an application allows a user to upload a malicious file directly which is then executed Due to Insecure File Upload An attacker Can Perform Different Attack Scenario It leads to OS Command Injection , XSS , SSRF etc .
Walk through (SVG File Upload):
How to Look for Stored XSS Using SVG upload
Which End Point Are Vulnerable :
- Profile Picture Upload
- File Upload On Another Functionality
- File Upload through Comment Section.
Now We have Application www.xyz.com Which Is Vulnerable for Execute File through File Upload and Here We have option User can Upload any File On Email Template Section .

As Above picture we see Upload Functionality and here Upload A file with Extension .svg And which Includes Below Code:
<?xml version="1.0" standalone="no"?>
<!DOCTYPE svg PUBLIC "-//W3C//DTD SVG 1.1//EN" "http://www.w3.org/Graphics/SVG/1.1/DTD/svg11.dtd">
<svg version="1.1" baseProfile="full" >
<polygon id="triangle" points="0,0 0,50 50,0" fill="#009900" stroke="#004400"/>
<script type="text/javascript">
alert("xss");
</script>
</svg>
And Save the Above File As xss.svg.
Now Upload it And It Successfully Uploaded As below Picture

Now Browse Uploaded file you will se generated url www.target.com/jl-landing-page-assets/11053/SVG_XSS1.svg As Result you will see :
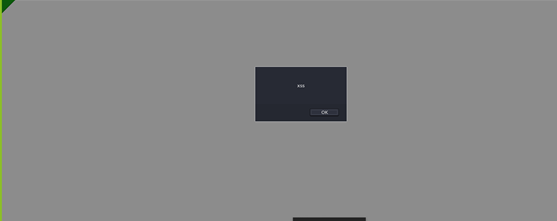
In the Above picture, we see our script successfully executed Which we bind through svg As a result We got stored XSS due to improper validation of file extension or its metadata.
As Result this allow an attacker to steal user session, take over user account, make redirect the user to attacker-controlled site.
Mitigation:
- Always filter files and Restrict the content type of the uploaded files
- Always check the metadata that the upload file contains.
Conclusion: In this blog, we discussed How an attacker able to misuse an insecure file upload vulnerability which leads to stored xss we discuss how an attacker able to inject a script inside svg extension hope this cleared your Doubt. Feel free to Ask your Questions.