Introduction
Server penetration testing is like giving your server a stress test for security. It’s a methodical examination where ethical hackers try to break into your server to expose weaknesses. By mimicking real attacks, it helps identify vulnerabilities so that security measures can be strengthened, keeping data safe from potential breaches. Securing data and infrastructure is important. Pen testing helps ensure server and network security.
Understanding the Need for Penetration Testing Services
Services for server penetration testing are preventive steps to find and fix potential security flaws before bad actors can take advantage of them. These services help companies evaluate their security posture, strengthen their defenses, and protect against costly data breaches and cyberattacks by simulating real-world attacks.
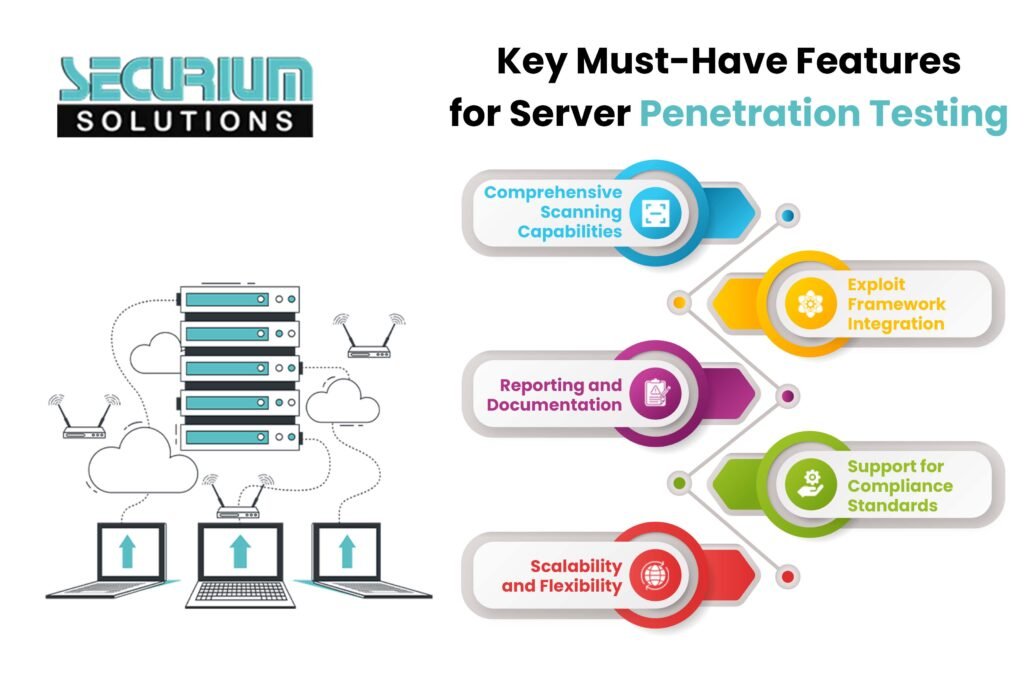
Server Penetration Testing Service: Strengthening Server Security
Server penetration testing is all about checking the security of servers, like operating systems and applications. It’s a methodical process to find vulnerabilities that hackers might exploit to get into systems or cause trouble.
In a server pen test, experts use different tools and methods to check how strong the server setup is. They look for weaknesses, scan for vulnerabilities, and even try to break in. Afterward, they analyze what happened and advise on how to make things more secure. The goal? To give practical tips to beef up cyber security and keep things running smoothly.
Network Penetration Testing Service: Securing Network Infrastructure
Network penetration testing goes beyond servers to check the whole network setup, including routers, switches, and firewalls. Its goal is to find weaknesses in network configurations that hackers could exploit to mess with data.
Experts use new tools and methods to hunt for potential weak spots in the network. They analyze traffic and run tests to see where hackers might sneak in. By doing this, they help companies tighten up their defenses and lower the chances of unauthorized access or data leaks, making the network more secure overall.
Benefits of Comprehensive Penetration Testing Services
- Risk Mitigation – Proactive vulnerability management reduces the risk of data breaches and cyberattacks, safeguarding organizations against costly incidents.
- Enhanced Security Posture – Organizations can prioritize investments in security measures to fortify their defenses by using penetration testing, which offers insightful information on how well-functioning current security constraints are.
- Regulatory Compliance – Regular penetration testing is mandated by numerous businesses and regulatory agencies as a component of compliance requirements. Organizations can stay out of possible trouble by following these guidelines.
- Better Preparedness for Incident Response – Penetration testing teams identify security flaws and establish effective response procedures for potential incidents, enhancing overall security for businesses.
- Customer Confidence – Regular penetration tests demonstrate a commitment to security, earning customer trust and confidence in the organization’s ability to safeguard their data.

Choosing the Right Penetration Testing Provider
When choosing a penetration testing provider, organizations should weigh various factors to ensure they receive thorough and impactful services tailored to their needs.
- Expertise and Experience – Find a provider with skilled security experts experienced in conducting penetration tests across different industries and technologies. Their expertise ensures thorough assessments tailored to your needs, enhancing your defenses against potential breaches across various sectors and technological landscapes.
- Comprehensive Testing Approach – Make sure the provider conducts holistic penetration testing, covering server and network infrastructure, applications, and services. This comprehensive approach ensures a thorough evaluation of vulnerabilities, strengthening overall security. It minimizes the risk of breaches and provides complete protection against potential threats across your infrastructure.
- Customized Solutions – Find a provider that offers personalized penetration testing services to match your organization’s individual security needs and tackle its unique challenges effectively.
- Compliance and Certification – Choose a provider that adheres to industry standards and holds relevant certifications, such as Certified Ethical Hacker (CEH) or Offensive Security Certified Professional (OSCP).
- Clear Reporting and Recommendations – Choose a provider that provides concise and actionable reports outlining identified vulnerabilities, their potential impact, and recommendations for remediation.
Conclusion
In today’s ever-evolving cyber threat landscape organizations need to take a proactive stance on security. Comprehensive server and network penetration testing services are pivotal in pinpointing and addressing security risks, bolstering defenses, and shielding sensitive data and infrastructure. Teaming up with a reliable penetration testing provider enables organizations to fortify their security posture, meet regulatory standards, and instill customer trust in their capability to fend off cyber threats effectively. This proactive approach is indispensable for staying ahead of adversaries and ensuring robust protection against emerging security challenges.




