Discover 4 ways to bypass login pages effortlessly. Gain access and unlock restricted content with these easy-to-follow techniques
Bypass by SQL Injection:-
I am taking an example of testphp.vulnweb.com for demonstration.

So now we can put the SQL injection payloads In it. The payload is “’ OR 1 — – ”.

see what happens when we press enter.
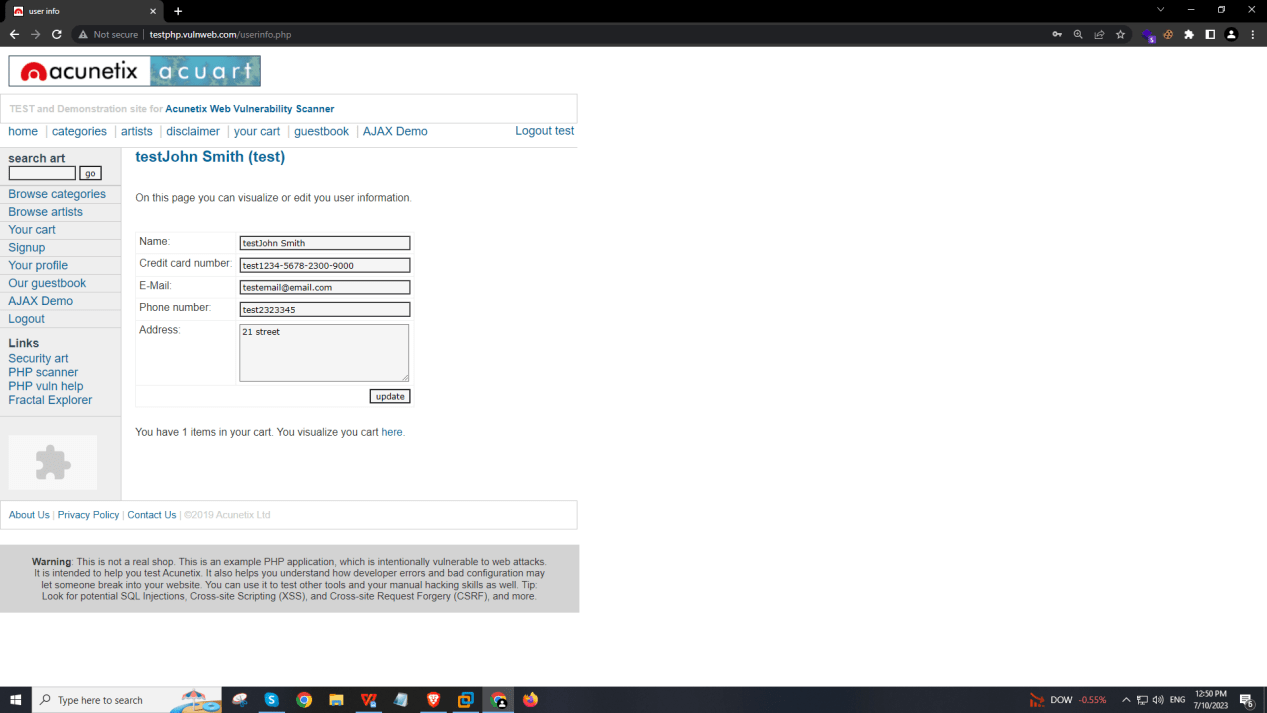
we are logged in as an admin!!!!!!
use tools like sqlmap to dump all the usernames and passwords.
Bypass by Brute Force Attack:
This occurs when site does not set a time limit and repeating limit. When the site does not show this kind of error then you can try this method.
First, enter your credentials and intercept the request .
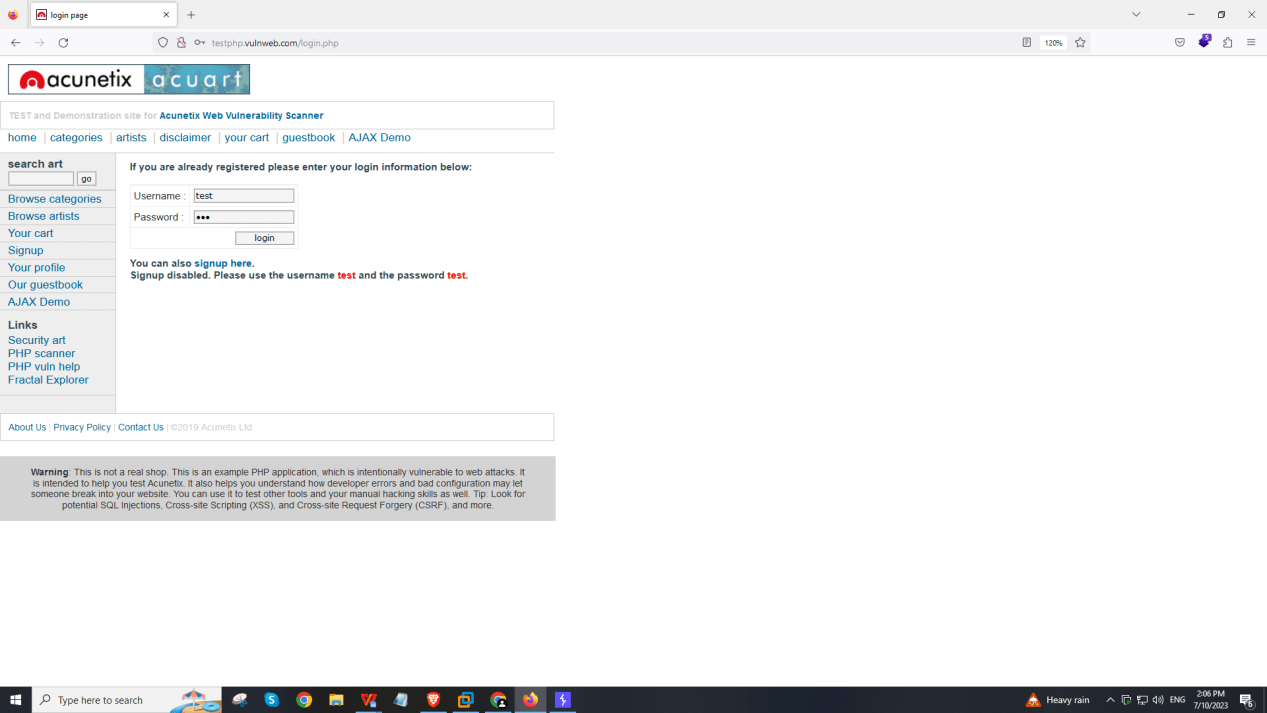
Send it to the intruder and clear all positions And select the attack type as a Cluster bomb .

For payloads set 1 . payload type: simple list. Paste the username list.
For payloads set 2. payload type: simple list. Paste the password list.
Finally, start an attack and find a larger value of length. If you find this, you can hit the target.
Bypass by Default credentials:-
When the developer creates the site, he often creates some default credentials for testing purposes. However, it frequently happens that these default credentials are not removed from the system, either intentionally or inadvertently. Consequently, when the site allows users to set their own passwords, there is a risk that many individuals will choose weak passwords, which the site will accept. As a result, it is crucial to consider checking for the presence of default credentials. These default credential lists can be easily found through search engines like Google. Some commonly encountered default credentials include combinations such as admin: admin, admin: password, and username:pass12345, among others.
By Removing Parameter in Request:-
When you enter your credentials site shows an error username or password is incorrect or does not match, You can try this method.
-First, you intercept the request remove the password parameter in the request, and forward the request and the server logs you into the site.
this occurs when the server does not validate the request properly.




