What is OS Command Injection:-
OS Command Injection is a type of security vulnerability that occurs when an attacker is able to execute arbitrary operating system (OS) commands on a server or web application by exploiting improper handling of user input. This vulnerability arises when user-supplied data is improperly sanitized or validated, allowing the attacker to inject and execute commands on the underlying operating system, potentially compromising the server.
This lab practical is on PortSwigger.
Lab url:- https://0aac006a036da70d84d1dcd40004005e.web-security-academy.net
Steps to reproduce:-
1. Click on the “Access Lab” tab.
2. Open the blog page.
3. Click on the Submit Feedback.
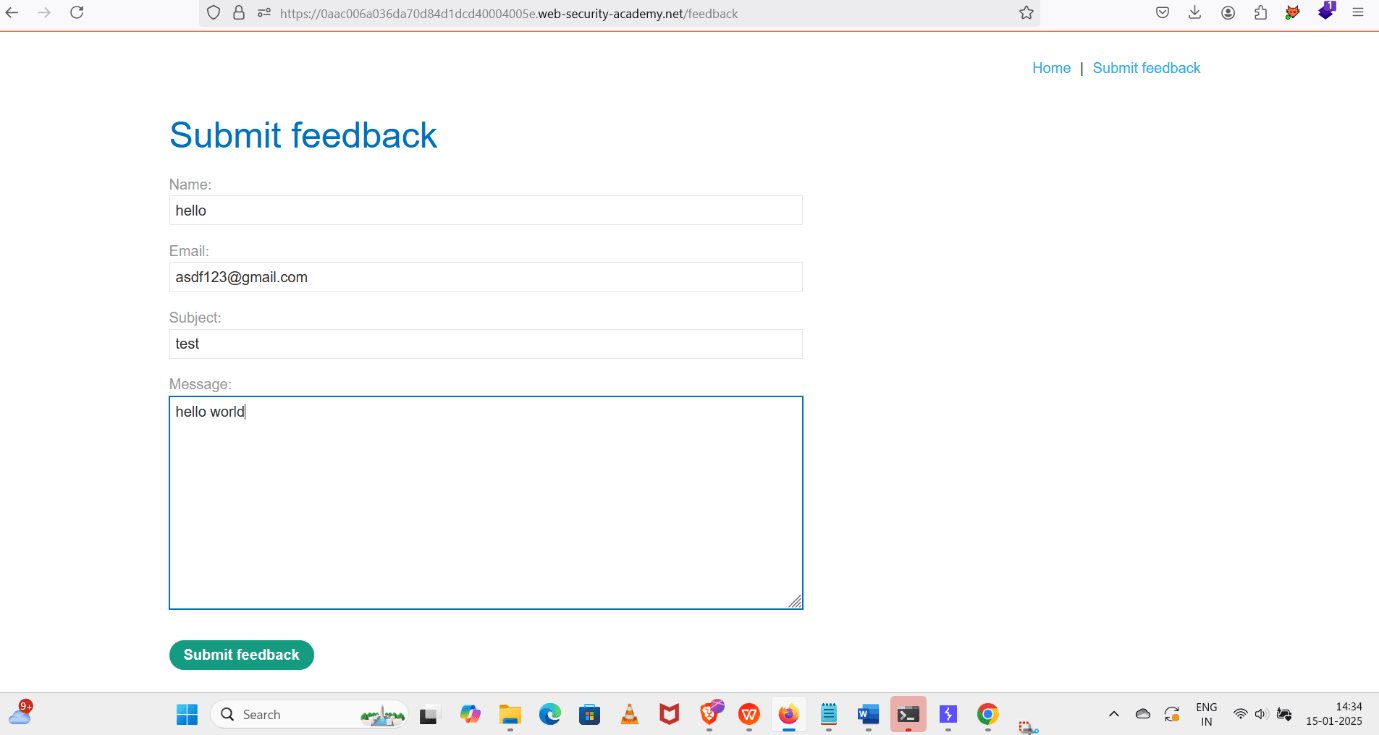
4. Fill in the blanks in the given column.
5. Open Burp Suite and turn on the proxy
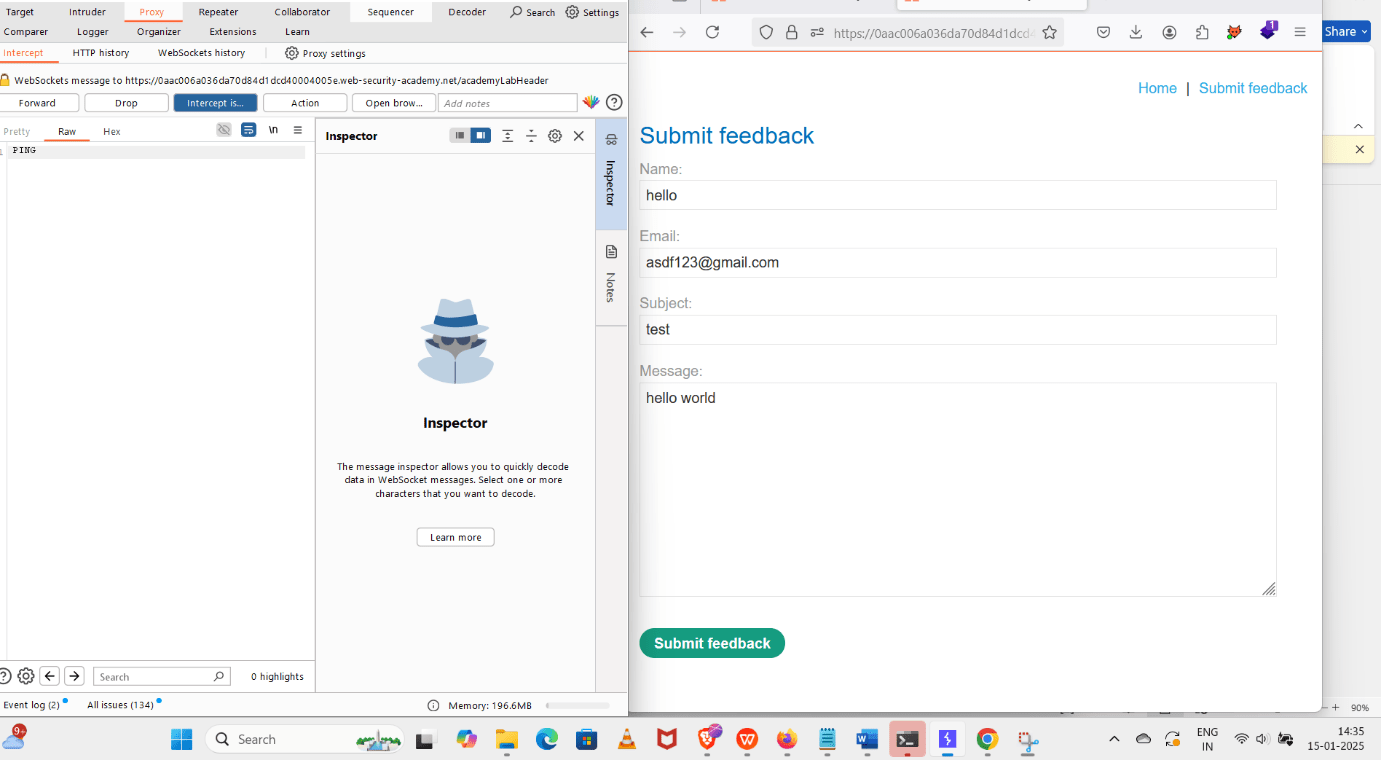
6. Click on the Submit Feedback button.
7. Check the response in Burp Suite
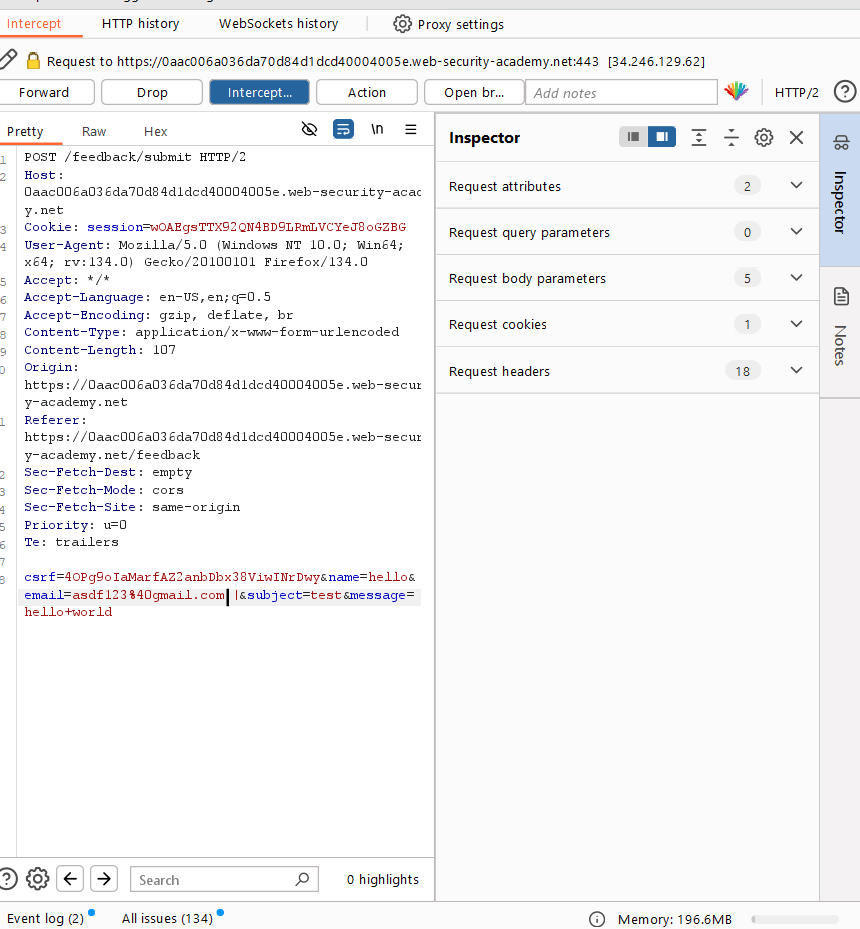
8. Edit the email column in Burp Suite and forward it.
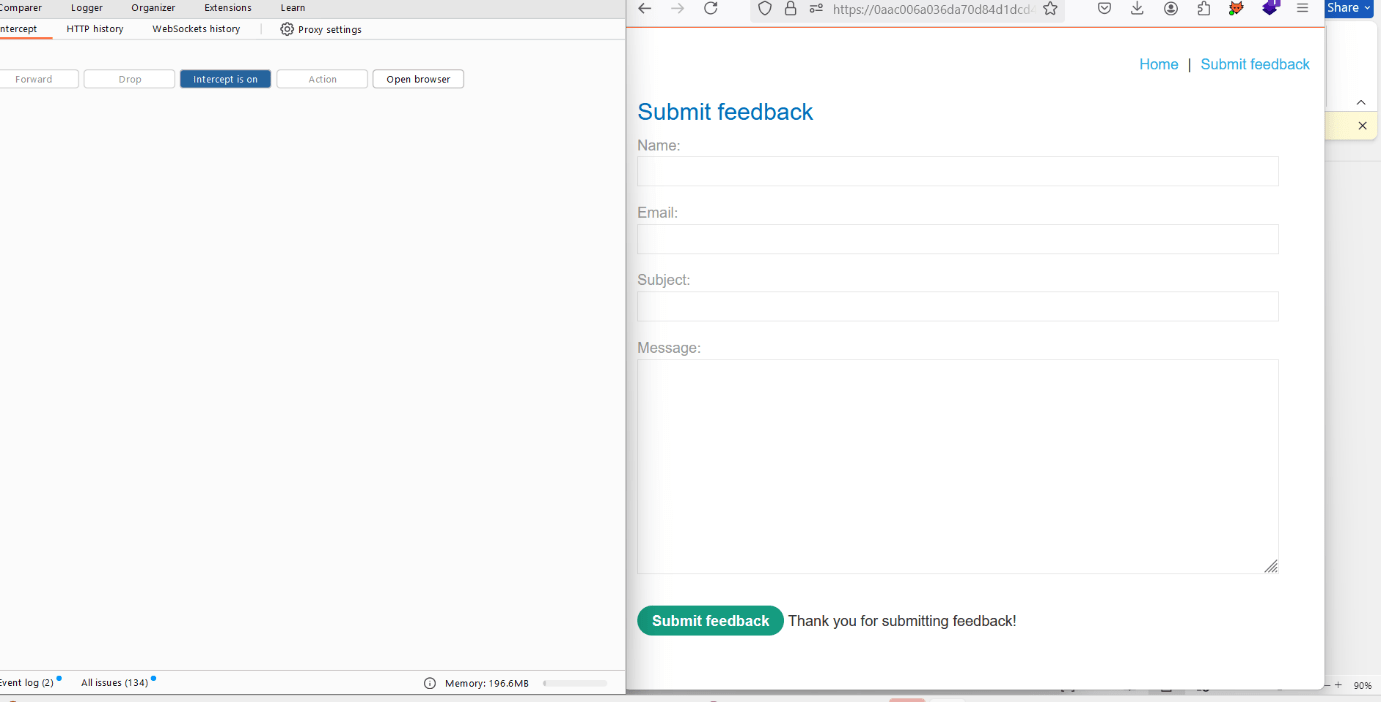
9. Respond to the submitted feedback and send a ‘Thank you’ message.
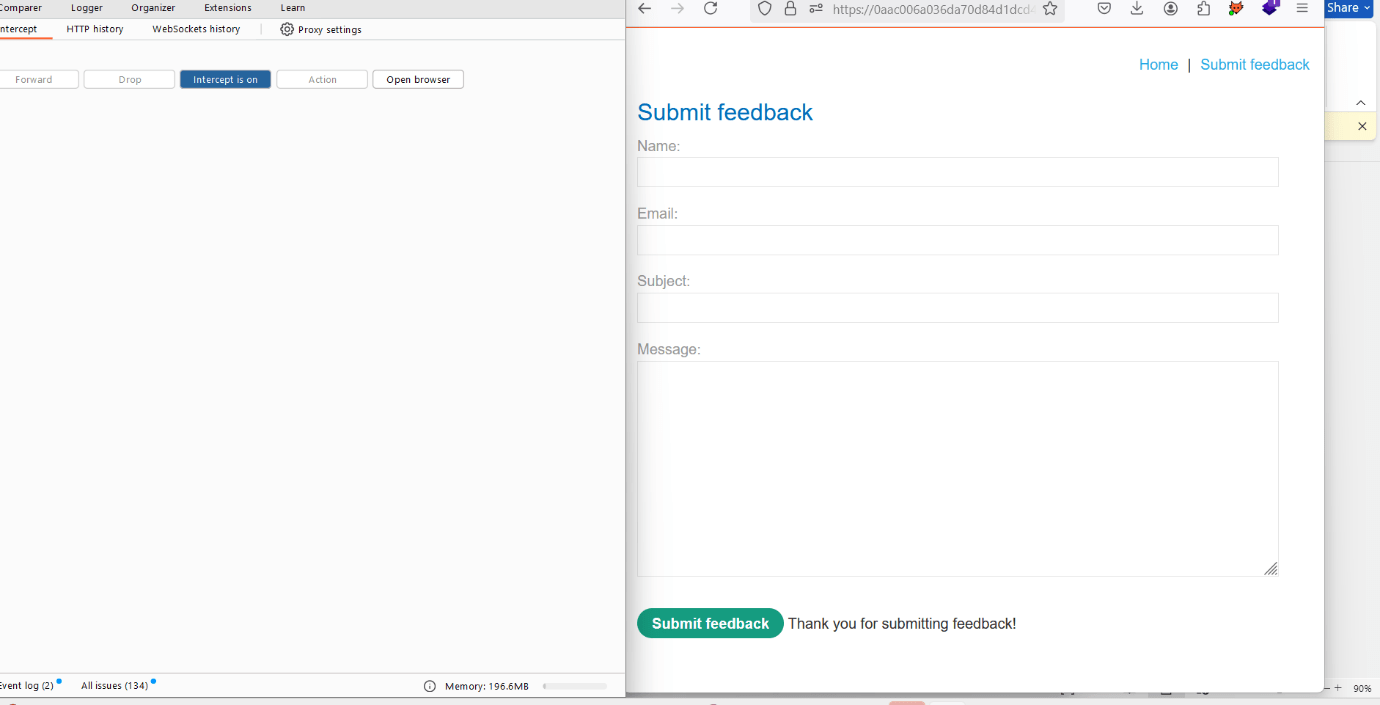
10. Fill in the submit feedback form again
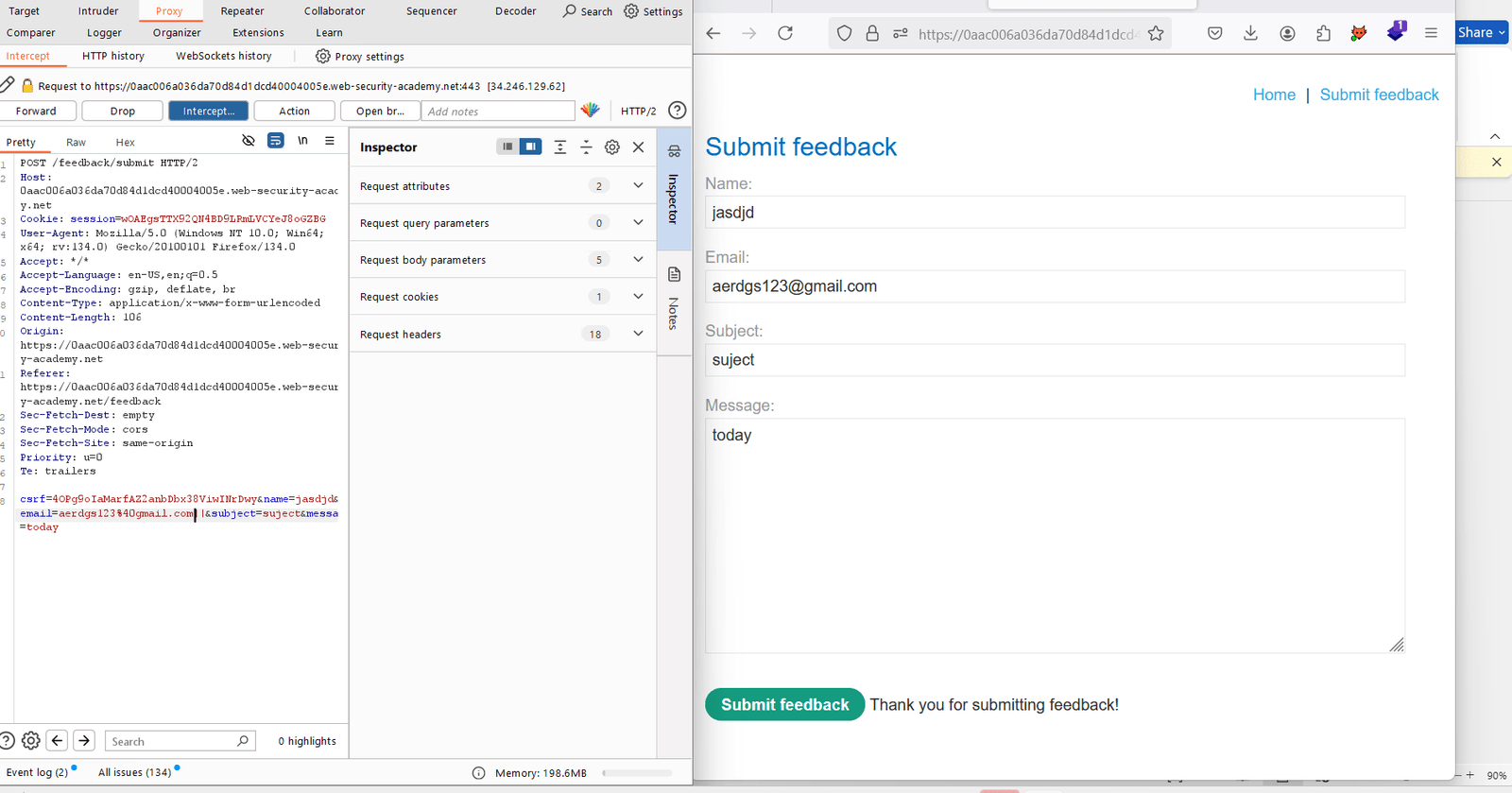
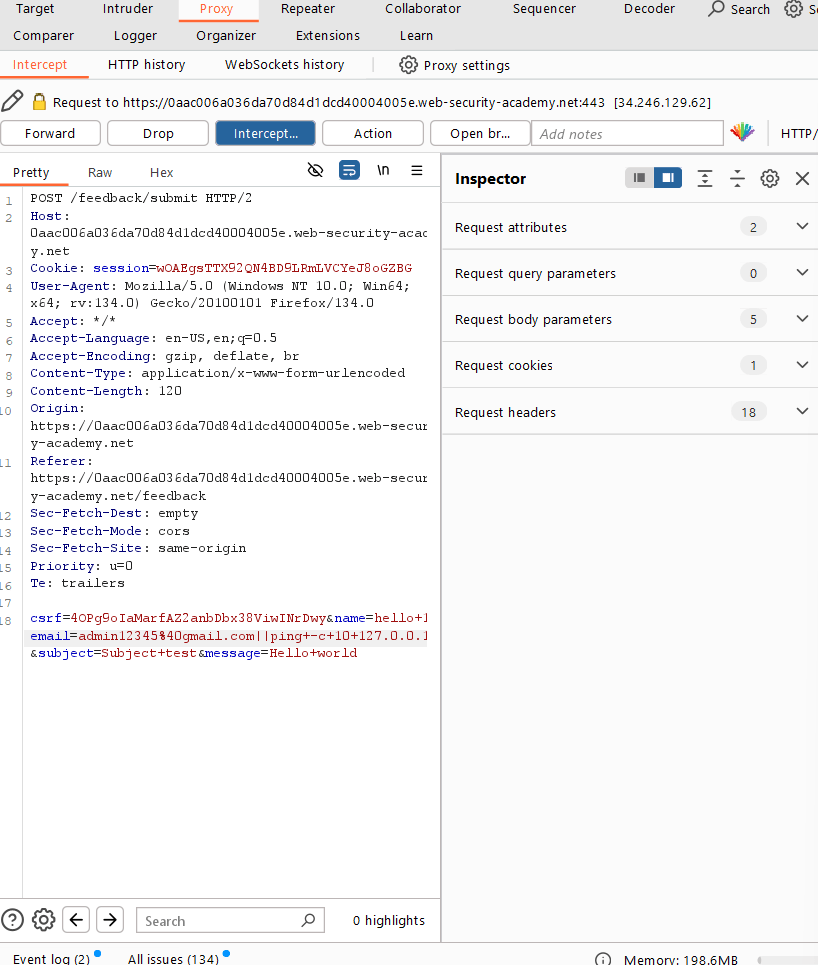
11. Edit the email column –||
12. Forward the request
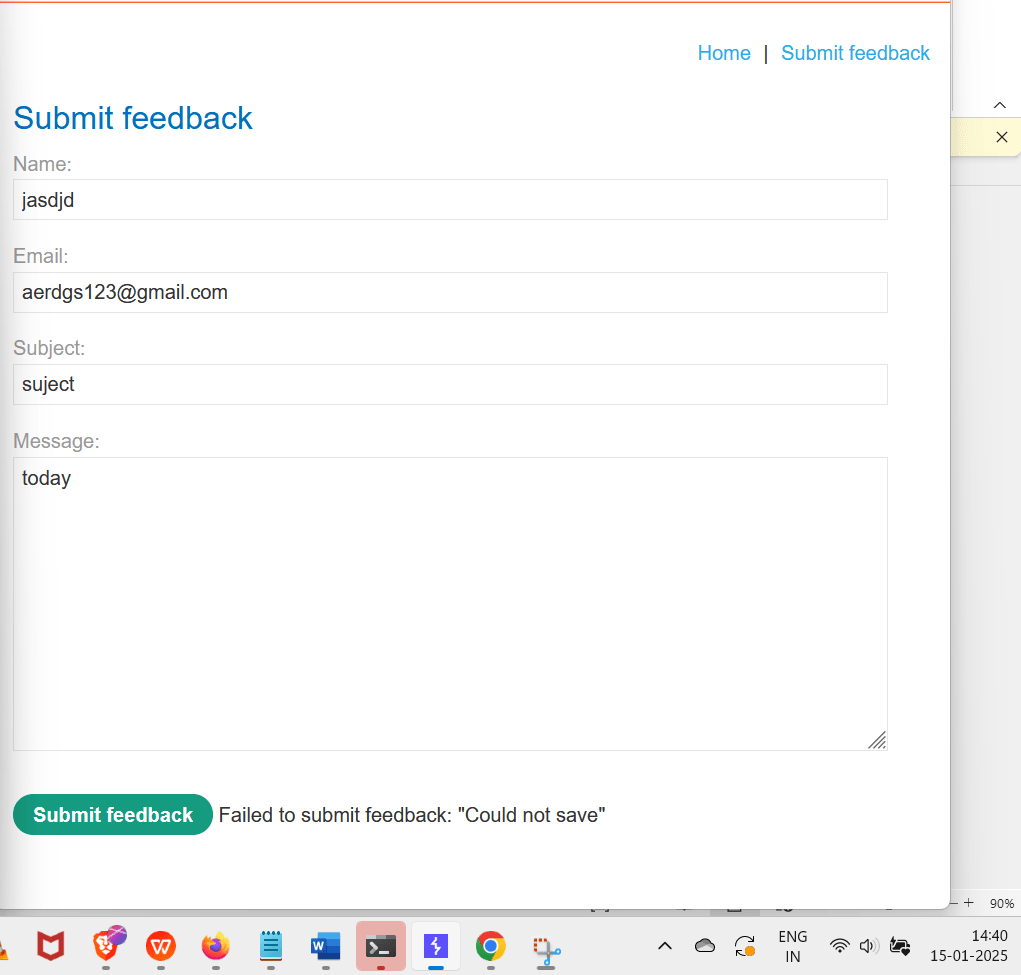
13. The message shows ‘Could not save,’ but try intercepting the request, editing the email column to ’email=x||ping+-c+10+127.0.0.1||,’ and then forward the request.
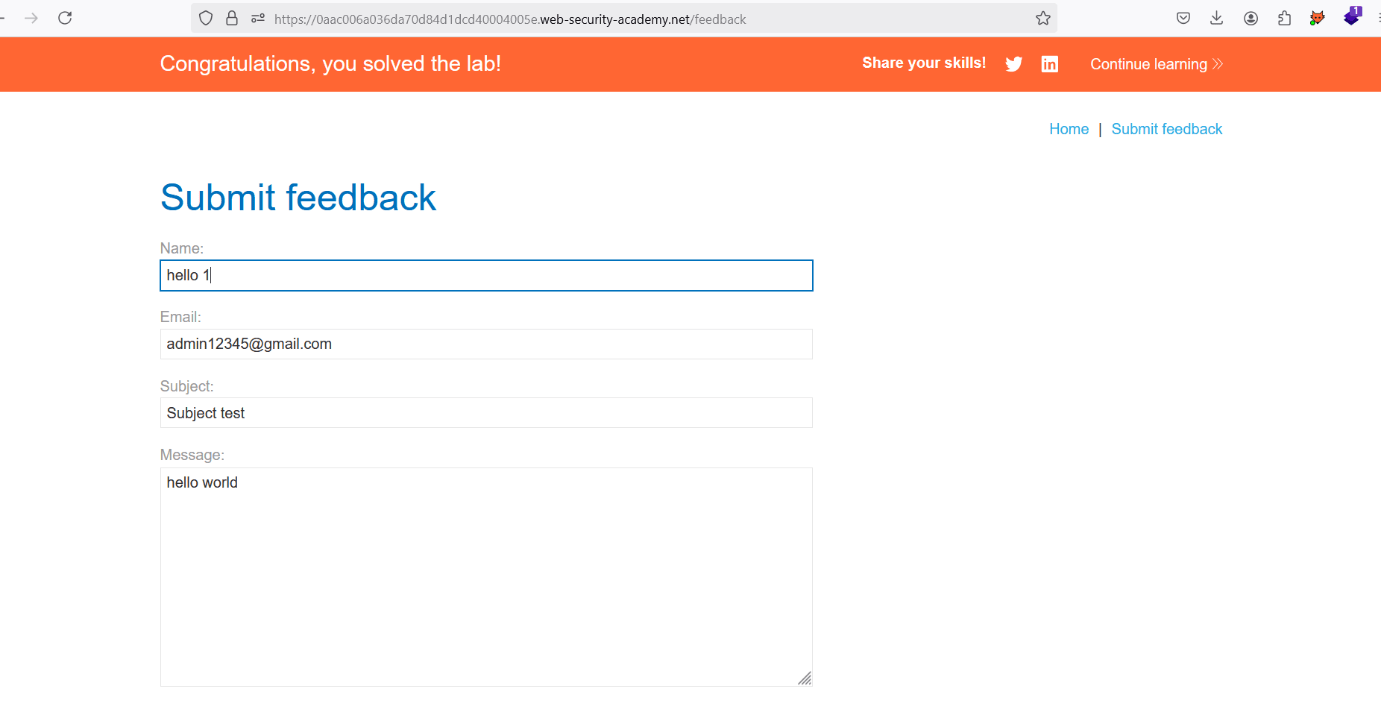
14. At least solve the lab.
Conclusion:-
No Direct Output: Unlike traditional OS command injection, where the results of the injected command are directly visible to the attacker, in blind OS command injection, the attacker cannot view the results. However, they can still manipulate the system and obtain feedback in an indirect way.
Indirect Feedback: The attacker must rely on the application’s behavior (like changes in response time, error messages, or status codes) to deduce the success or failure of the command injection.
Timing-Based Attacks: One common form of blind OS command injection is time-based blind injection, where the attacker sends a command that causes a delay (e.g., using sleep or wait commands). The attacker can then infer whether the command was executed by observing how long the application takes to respond.




