What is DOM XSS :-
DOM XSS (Document Object Model Cross-Site Scripting) is a type of Cross-Site Scripting (XSS) vulnerability that occurs when an attacker is able to inject and execute malicious scripts within a website’s DOM (Document Object Model) in the user’s browser. Unlike traditional XSS, which typically occurs when untrusted data is injected into the HTML or JavaScript of a web page from the server-side, DOM XSS happens entirely on the client side.
DOM XSS vulnerability:-
Dynamic Content Manipulation: DOM XSS happens when web applications dynamically generate or modify web content based on user input or other untrusted data (like URL parameters, local storage, or cookies) using JavaScript. If this input is not properly sanitized or validated, an attacker can inject malicious code into the DOM.
Client-Side Execution: The key distinction with DOM XSS is that the malicious script is executed on the client side, in the victim’s browser, rather than being injected from the server side. This means that the vulnerability often arises due to unsafe interactions between JavaScript and the DOM.
Injecting Malicious Content: The attacker can exploit DOM XSS by injecting malicious content (such as JavaScript code) through various channels, such as:
1. URL parameters: Data from the URL (e.g., query string) can be injected into the DOM.
2. Hash fragments: Data after the # symbol in the URL can also be manipulated.
3. User input: Any form fields, search bars, or other inputs that are used to generate dynamic content can be exploited.
Description:-
DOM XSS (Document Object Model Cross-Site Scripting) is a type of Cross-Site Scripting (XSS) vulnerability that occurs when an attacker is able to inject and execute malicious scripts in the Document Object Model (DOM) of a web page. This attack takes place entirely on the client side (in the user’s browser) and does not require server-side code injection. DOM XSS vulnerabilities arise when untrusted data is dynamically injected into the DOM through JavaScript, leading to the execution of malicious scripts.
This lab practical is on PortSwigger.
Lab url:- https://0a3d006e040d5b9e8298883700e70063.web-security-academy.net/
Steps to reproduce:-
1. Click on the “Access Lab” tab.
2.
3. Open the blog page.
4. 
5. Store the data in the search bar to fill in the data from the string.
6. 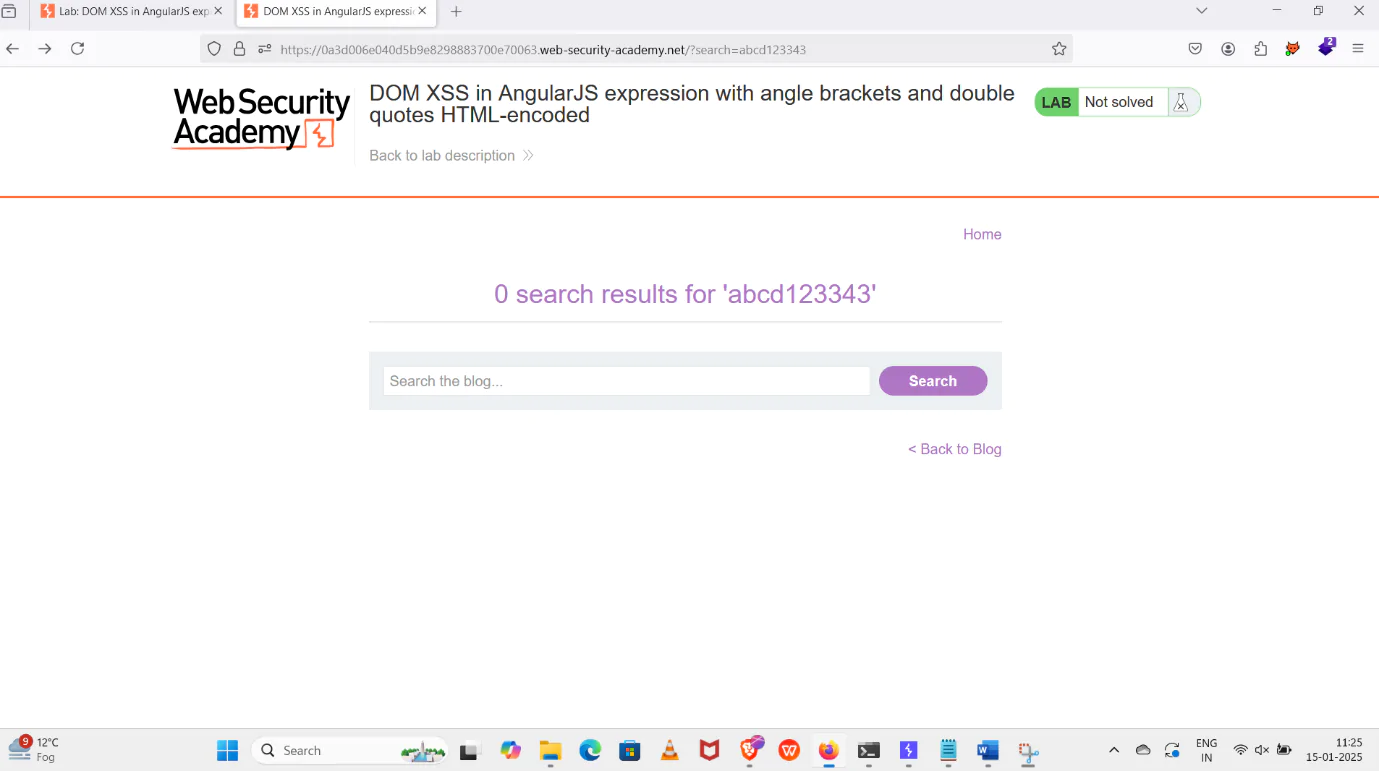
7. After the data is filled, include the alert command in the blog page and submit it.
8. {{$on.constructor(‘alert(1)’)()}}
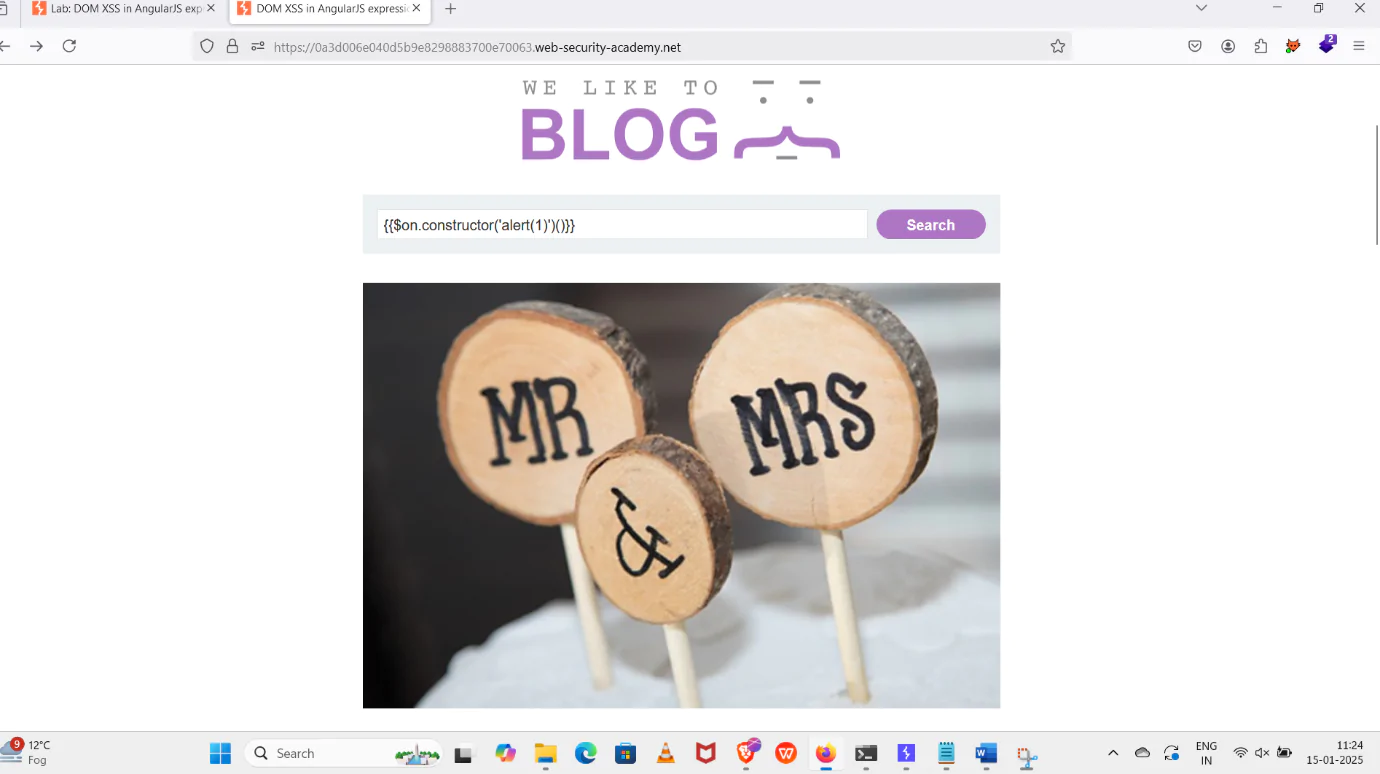
9. Click on the search option tab, then create a pop-up and click OK.
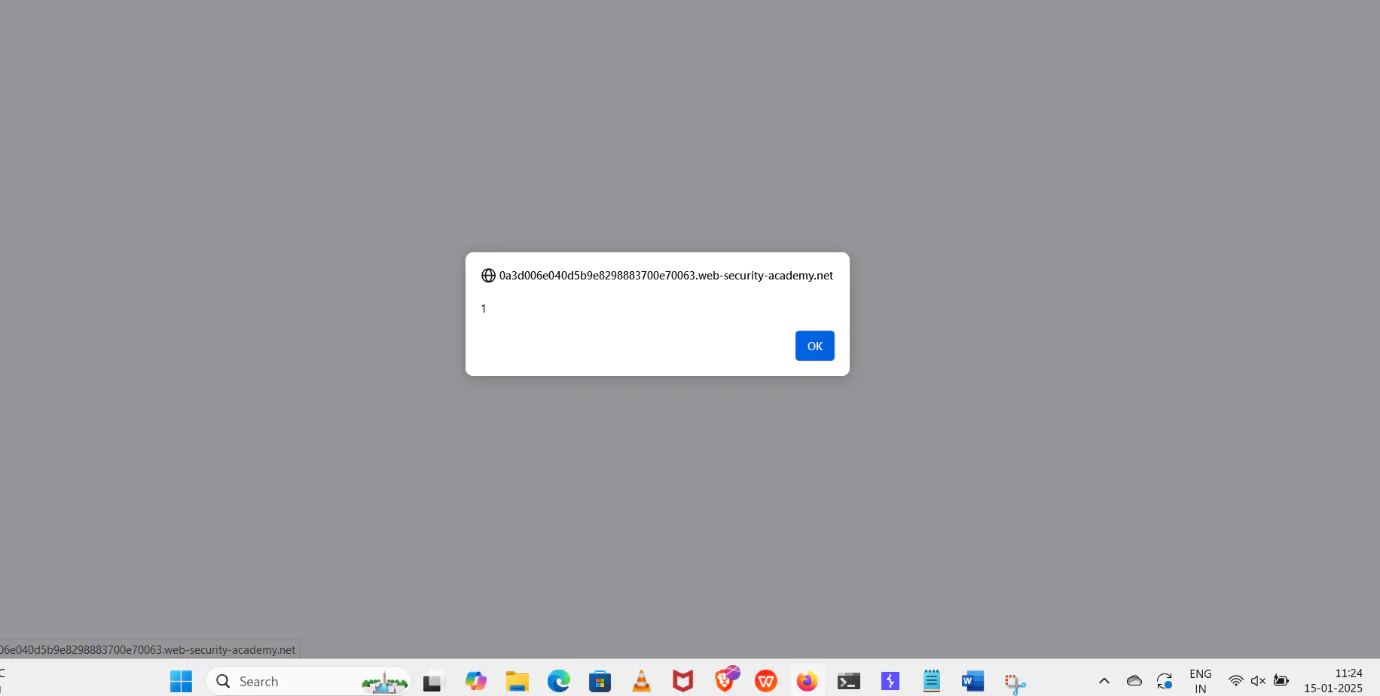
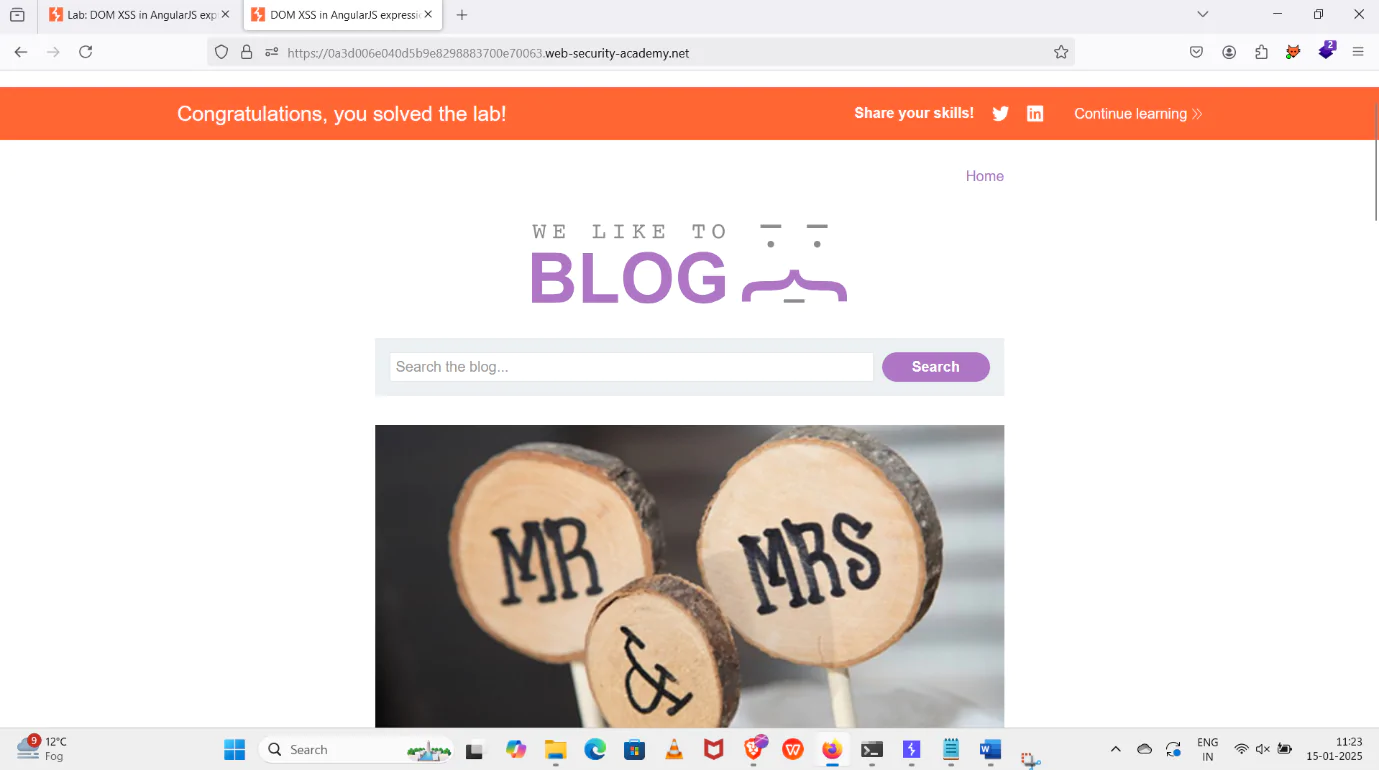
Conclusion:-
1. Client-Side Execution: DOM XSS attacks occur on the client side, meaning the vulnerability lies in how JavaScript on the page processes user input or other dynamic data and modifies the DOM.
2. Injection and Execution: The attacker injects malicious JavaScript into the DOM through sources like user input or URL parameters, and this script is executed in the context of the user’s browser, potentially leading to theft of sensitive data, manipulation of user interactions, or other malicious actions.
3. Difficult to Detect and Mitigate: Since the malicious code executes client-side, traditional server-side XSS protections are ineffective. It requires proper client-side measures to sanitize and handle data securely.




