Greeting Everyone ! today In this Blog We will explore One Most Common Vulnerability which present in every website IDOR In this Post We Will Learn About IDOR How Attacker Able to misuse this Vulnerability . In Modern Web application IDOR Basically Found On API Section .
What is IDOR ?
Insecure direct Object Reference Which is Authorization issue Which mostly Found On Our Web application . Access control is directly related to authorization schema .
insecure direct object reference cause when an attacker able to direct access by using user-supplied input to an object that has no authorization to access. Attackers can misuse the authorization mechanism to access resources in the system directly by exploiting this vulnerability.

We have already post How idor Attack work Visit .
Here We will go through How IDOR allow us to access admin panel Without any Authorization .
Walk through :
Recon Is Main Thing When Your Doing Testing against Target always observe robots.txt file which sometimes leak critical Sensitive information .
Now For Testing purpose We have LAB : https://securiumsolutions.com/exploitation-against-idor-vulnerability/
Navigate to https://acf31f741e29ec2180260cc300680027.web-security-academy.net/ which is online Shop website
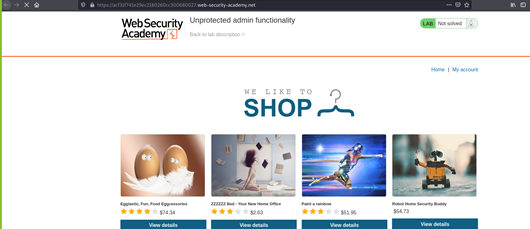
As above we see Our Application , Now navigate to path robots.txt
https://acf31f741e29ec2180260cc300680027.web-security-academy.net/robots.txt as below Picture

As above picture we see Another path Disallow: /administrator-panel which is exist On robots.txt to protect against web crawling .
Now Browse url https://acf31f741e29ec2180260cc300680027.web-security-academy.net/administrator-panel to see Is there any Authorization needed Or not , As Result

As above picture we see We are able to access Admin dashboard without any authorization schema which is Insecure Direct object reference That we access object directly .
As above scenario This is Another Way How to look for IDOR . Visit Our part1 blog https://securiumsolutions.com/exploitation-against-idor-vulnerability/ .
Conclusion : in this Blog we Discussed How IDOR Allow to Access Unprotected admin functionality without Any Authorization If your web application did not validating user supply Input as we discuss about IDOR And way To exploitation. Hope You Learned Something New
For References As Lab : https://portswigger.net/web-security/access-control/idor
Thanks For Reading……. See You In Another Blog!
Stick With Our Blog : https://securiumsolutions.com/



