Hello Guys,
Today, We will be learning something about ICS and SCADA
What is ICS?
Industrial Control Systems (ICS) are in use in Heavy Industries to control the machineries and to carry out heavy Process and Transportations. Whatever around you that are heavy that needs to be lifted or carried out with Heavy Machines are made through Industrial Control Systems only.
What is SCADA?
Supervisory Control and Data acquisition(SCADA) systems. This act as a Supervisory system inside the Industrial Control Systems(ICS) like a CCTV used to monitor and manipulate the Industrial operations.
We have to discuss about lots of Devices when it comes to Operational Technology, ICS/SCADA. We will discuss all in the upcoming blog series.
Today we will be discussing about the Protocols we use in OT, ICS/SCADA Systems.
This is our Basics, once we are clear with what we are dealing. we can easily secure them.
Protocols in OT/ICS/SCADA.
Protocols has been standardized by several standard organizations such as IEC, ISO and ANSI. Most cases, these protocols are built by vendors according to their needs that requires specific hardware and software to create vendor-centric systems.
Since they were not designed with Security in mind and are insecure needs to be taken care off properly.
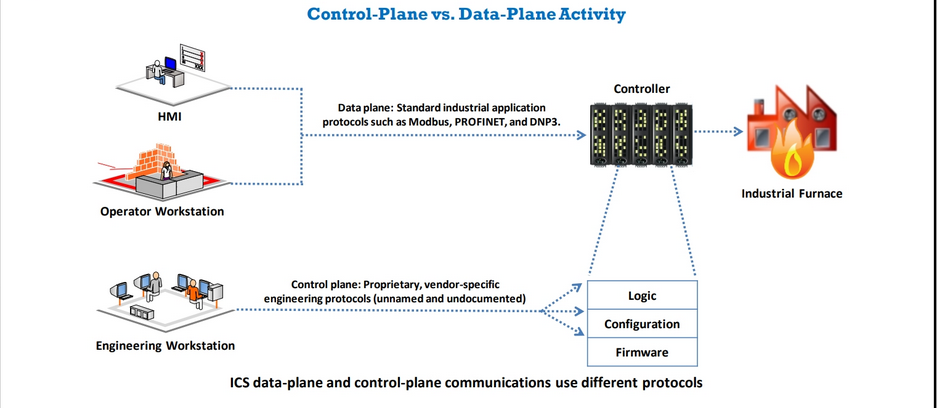
In ICS Networks, Protocols are separated as data plane and Control plane protocols.
Data Plane Protocols: Used to pass parameters and registers between human-machine interface(HMI) SCADA applications and Input/Ouput.
Control Plane Protocols: We can say these are Proprietary Protocols designed by the vendors with specific tools for reprogramming of controller, upload/download of firmware etc. There won’t be any documentation and names for few protocols that are created for specific task.
MODBUS:
Most Common Protocol. Placed at Application layer messaging Protocol at Level 7 of the OSI model. It provides Client/Server Communication between devices connected to different types of buses or networks.
Modbus is a method used for transmitting information over serial lines between electronic devices. It has been used by hundreds of Vendors to transfer Discrete/analog I/O and register data between control devices.
Modbus Master – The device that requests information
Modbus Slaves – The device that supplies information.
In a standard network there is one master and up to 247 Slaves, each with unique address from 1-247.
Modbus Protocol types
- MODUBUS TCP
- MODBUS Remote terminal Unit
- MODBUS ASCII
- MODBUS Plus
- MODBUS Daniels
- MODBUS Tek-Air
MODBUS MAP
- The kind of data the device reads and stores (e.g., temperature or pressure)
- The address at which the data are stored (e.g., voltage A-N at 40001)
- The format in which the data is stored (e.g., bits, UINT16, and SINT16)
- Engineering units of the points, if required
- Whether the device has ADU or PDU addressing
So, that’s what we have today, we will do learn how to do scanning for MODBUS Protocol and reconnaissance on that.
Stick with our Blog Series to Learn More
Stay safe and Secure
Author
Sam Nivethan V J
Security Analyst & Cyber Intern



