Introduction
Cybersecurity threats continue to evolve, and one of the often-overlooked vulnerabilities is username enumeration. This technique allows attackers to determine valid usernames on a system or website, increasing the risk of brute-force attacks, credential stuffing, and unauthorized access. This blog will explain what username enumeration is, how attackers exploit it.
What is Username Enumeration?
Username enumeration occurs when an attacker can determine whether a specific username exists in a system. This happens when an application provides different error messages or responses based on whether the username is valid or not. Attackers use this weakness to compile a list of valid usernames, which can then be used for further attacks.
How Attackers Exploit Username Enumeration
Login Pages: Some websites return different error messages for incorrect usernames and incorrect passwords. For example:
“Username does not exist” (reveals the username is incorrect)
“Incorrect password” (confirms the username exists but the password is wrong)
So let’s exploit this
Open a website login page, which shows these errors, And also open your burpsuite for further exploitation.
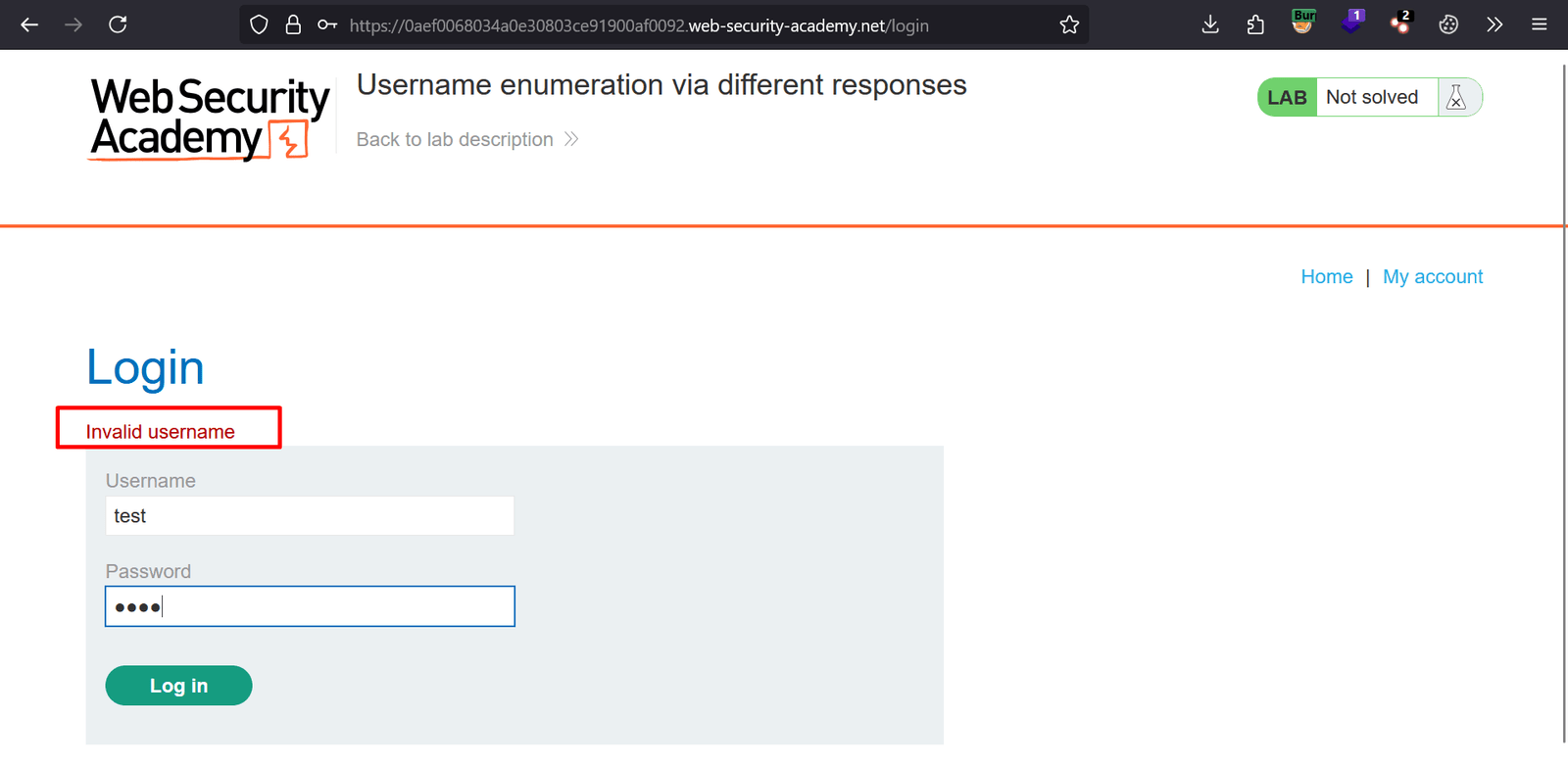
1. To investigating the login page submit a invalid username and password.
2. In burpsuite, go to Proxy > HTTP History and find the POST /login request.
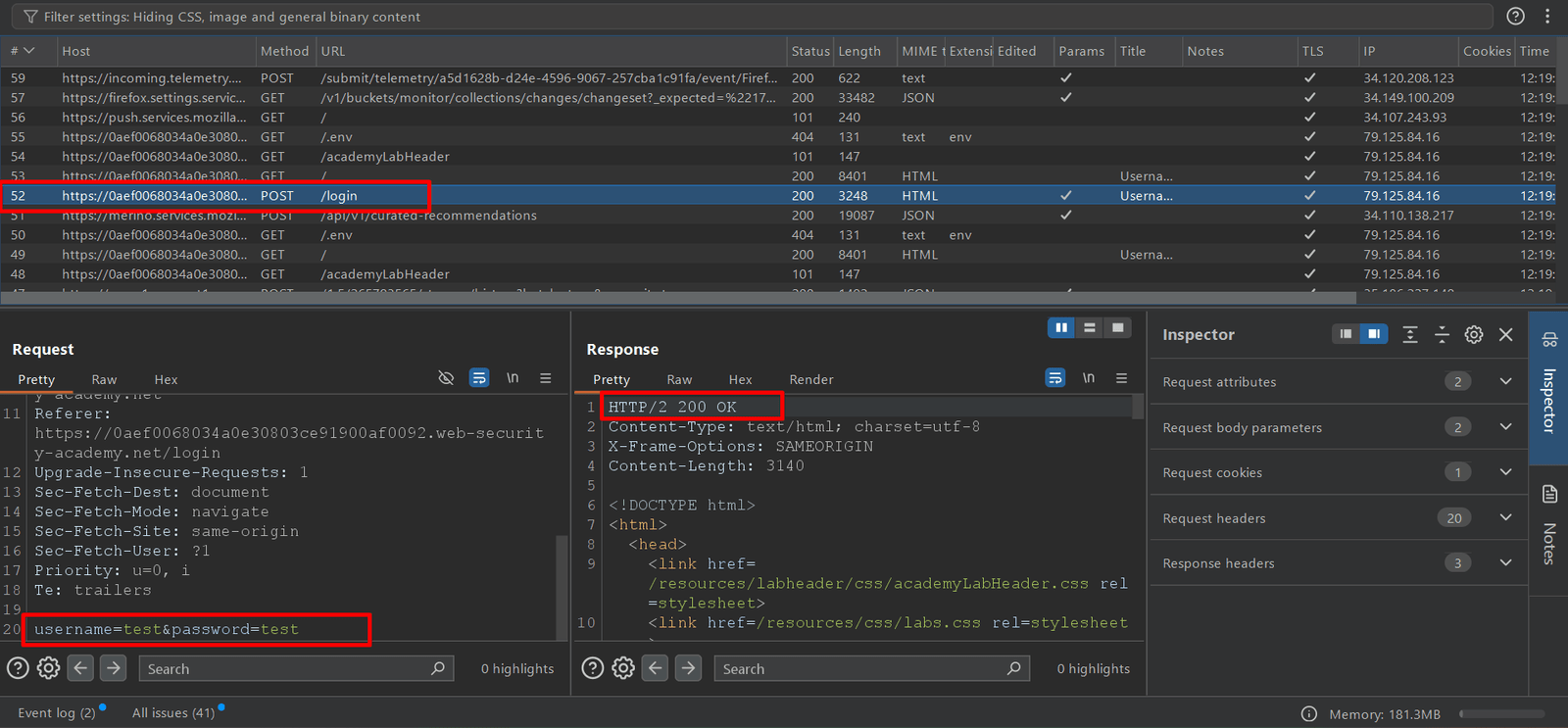
3. Now sent this request into the burp intruder tab, and select username parameter for example username=§invalid-username§.
4. Make sure sniper attack is selected.
5. In payloads side panel, make sure the simple list payloads type selected.
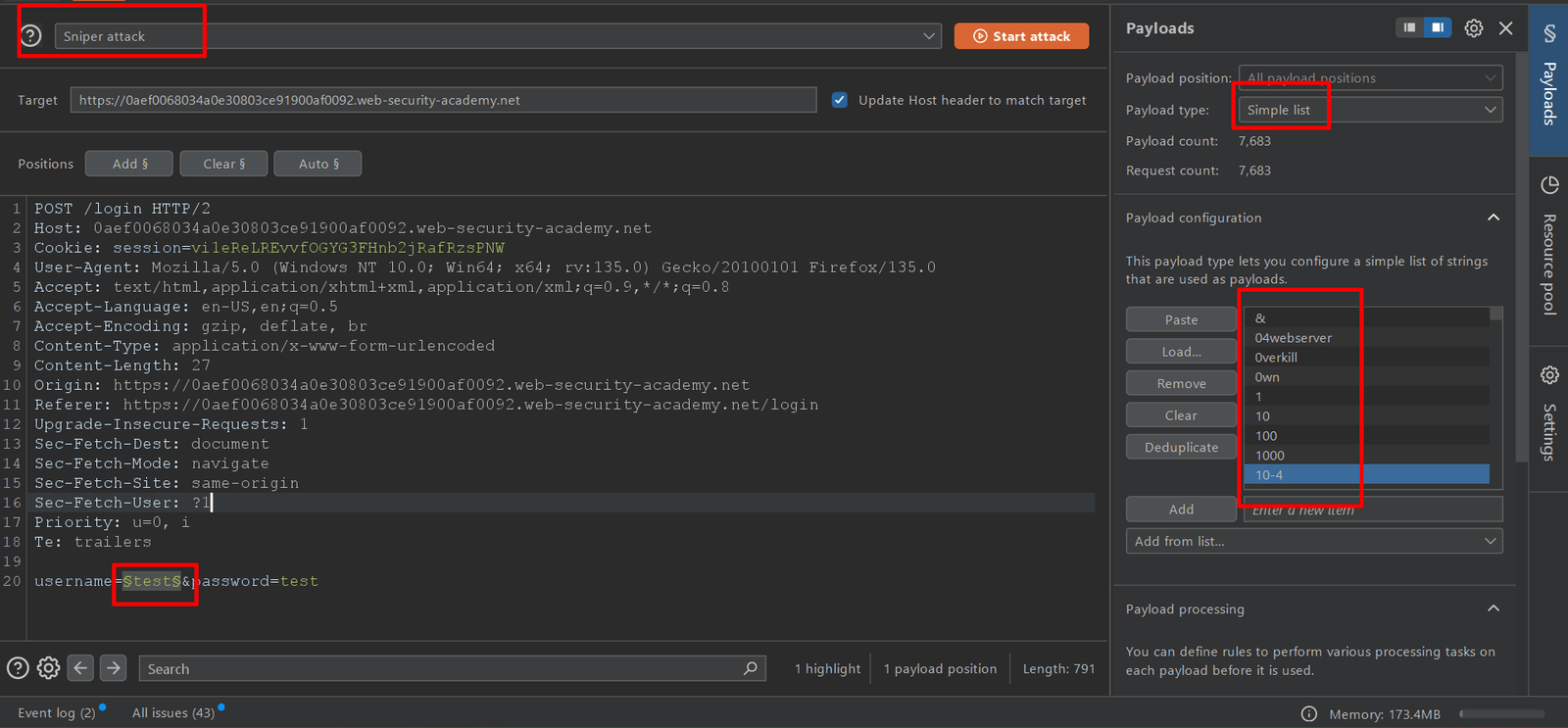
6. Under payload configuration, paste the list of candidate usernames. Finally click Start attack.
Conclusion
Username enumeration might seem harmless at first, but it provides attackers with critical information to compromise user accounts. By implementing secure authentication practices and limiting exposure of valid usernames, organizations can significantly reduce the risk of cyberattacks. Always stay updated on security best practices to protect both user data and system integrity.
Stay safe online, and keep your applications secure!




