Hello Everyone,
Hope you are doing well…
Today we will discuss about what precautions we should take while using Dark Web.
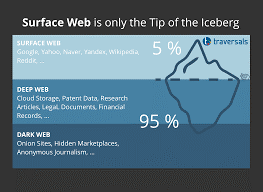
What is Dark Web?
The dark web refers to encrypted online content that is not indexed by conventional search engines. Sometimes, the dark web is also called the dark net. The dark web is a part of the deep web, which just refers to websites that do not appear on search engines.

Some of the Important points related to Dark Web.
- The dark web refers to encrypted online content that is not indexed by conventional search engines.
- Specific browsers, such as Tor Browser, are required to reach the dark web.
- As with the early Internet, the dark web has also gained a reputation as a haven for illegal activities.
- The dark web helps people to maintain privacy and freely express their views.
How to access the dark web safely?
If you have a legitimate or viable need to access the dark web, you’ll want to make sure you stay safe if you decide to use it.
7 Tips for safe access to the dark web
- Trust your intuition. To avoid being scammed, you’ll want to protect yourself with smart behavior on the web. Not everyone is who they seem. Staying safe requires that you watch who you talk to and where you visit. You should always take action to remove yourself from a situation if something doesn’t feel right.
- Detach your online persona from real life. Your username, email address, “real name,” password, and even your credit card should never be used anywhere else in your life. Create brand-new throwaway accounts and identifiers for yourself if necessary. Acquire prepaid, unidentifiable debit cards before making any purchases. Do not use anything that could be used to identify you — whether online or in real life.
- Employ active monitoring of identify and financial theft. Many online security services now offer identity protection for your safety. Be sure to take advantage of these tools if they are made available to you.
- Explicitly avoid dark web file downloads. Fear of malware infection is significantly higher in the lawless territory that is the dark web. Real-time file scanning from an antivirus program can help you check any incoming files in case you do opt to download.
- Disable ActiveX and Java in any available network settings. These frameworks are notorious for being probed and exploited by malicious parties. Since you are traveling through a network filled with said threats, you’ll want to avoid this risk.
- Use a secondary non-admin local user account for all daily activities. The native account on most computers will have full administrative permissions by default. Most malware must take advantage of this to execute its functions. As such, you can slow or halt the progress of exploitation by limiting the account in-use to strict privileges.
- Always restrict access to your Tor-enabled device. Protect your children or other family members so they aren’t at risk of stumbling across something no one should ever see. Visit the Deep Web if you’re interested, but don’t let kids anywhere near it.

Top Five Safe Ways to Use a Dark Website (Do & Don’t).
Do #1: Ensure Tor is Always Updated.
Don’t #1: Use Tor for Torrenting.
Using a torrent client bypasses Tor’s protection and blows your anonymity by sending your real IP address to the torrent service and other ‘peers.”
Do #2: Create a new identity when necessary.
If you’re worried that your privacy has been compromised, do the following:
- Click the onion icon on the toolbar.
- Choose “New Identity.” This option will restart the Tor browser and reset your IP address, so you can carry on browsing as a fresh user.
Don’t #2: Maximize the Tor Window.
Leave Tor browser windows at their default size because maximizing them allows websites to determine the size of your monitor. This suggestion may not seem significant on its own, but combined with other data, it may provide the “extra” information websites need to identify you.
Do #3: Use a VPN Alongside Tor.
It’s important to remember that Tor is a proxy rather than a VPN, which only protects traffic routed through the Tor browser.
Several VPNs offer features explicitly designed for Tor users, including:
- ProtonVPN, which lets you access servers pre-configured to redirect traffic through the Tor network.

- ExpressVPN, which enables you to sign up anonymously through its ‘.onion’ website.

- AirVPN, which routes traffic through the Tor network first and then through the VPN.

Read here for Best VPN for 2022
Don’t #3: Search The Web Using Google.
We recommend using Tor’s default privacy search engine DuckDuckGo, its ‘Onion’ variant, or Startpage (which uses non-tracked Google results), all of which come pre-installed alongside Google.

Do #4: Consider Running a Tor Relay.
You need to have a Linux computer running Debian or Ubuntu to host a reliable relay. In Windows, you need to run a Linux distro as a virtual machine to set up your relay. It’s a bit of a hassle, but at least it will keep your Tor traffic separate from the rest of your system.
Don’t #4: Share Your Real Email Address.
A disposable email service such as Maildrop or the brilliant Fake Name Generator can create a temporary address and identity for site registrations and keep your Tor persona separate from your standard web one.
Do #5: Use Tor for Anonymous Email.
You can use your favourite email services in Tor, although Google may ask you to verify your Gmail account. However, the content of your messages won’t be encrypted in transit. Tor will, of course, disguise where you are, but unless you’re using a disposable email address (see above), anyone intercepting your messages will see your real email address and, potentially, your name.
Don’t #5: Go Overboard with Browser Add-Ons.
Because Tor is based on Firefox, it is still possible to install your favorite add-ons to suit your preferences, which is understandable if you are planning to use Tor as your default browser. Don’t be tempted! Even if extensions aren’t infected with malware (as some Chrome ones were recently found to be), they may seriously compromise your privacy.
Recommendation: Next Blog will be on how to get into the Dark Web.
Thank you for your time.



