Greeting Everyone ! Hope all Going Well ! As Many people Has doubt regarding DOM based XSS so in this post we are going to discuss How DOM Based XSS Work How It Exploitable Withing Vulnerable Web Application How DOM Actually Work ?
Before We Start If You don’t Know What Is Javascript DOM See Our Las blog
Let’s Start with How This DOM based XSS Work?
DOM XSS Document Object Model Cross site scripting which is same as Basic XSS but As is Webapplication fail to filter DOM Data that Entered By User Which causes DOM Based XSS in Simple Word . Here The attacker able to manipulate data to include XSS content on the web pagemalicious by executing JavaScript code.
For Those Who have no Idea about html and DOM syntax html is programming that we design our web application using different element and DOM can be accessed with JavaScript .
Let’s See a example How Dom Present In Our Programming
<html>
<head>
<title>dom </title>
</head>
<body>
<script>
var x = document.location.hash.substr(1);
window.location=x;
</script>
</body>
</html>
As above code section we see <script> tag which consist dom element As above we see it redirect user through window.location=”” but if we use some javascript content eg: javascript:alert(“xss”) it may execute and as result XSS will triggered .
An Another Example Supposed Web Application Has Functionality to Search Insite Web Application With below Code Sample:
<html>
<h1>Search<h1>
<div id ="searchquery"> </div>
<script>
var keyword = location.search.substring(3);
document.querySelector('searchquery').innerHTML = keyword;
<script>
</html>
As Above code It take user search input in javascript Element As Whatever user will search it will manipulate through ‘search quesry’
Above if we input javascript:prompt(document.cookie) which we can manipulate any user session cookie as which is most dangerous issue for any web application.
Let’s See an example with lab :
I refer You go through : https://portswigger.net/web-security/cross-site-scripting/dom-based/lab-document-write-sink
Now we have Targeted Website Where We have Functionality To Search Inside Web application,
Now as above picture we see Search functionality and if we look the search code that manipulate Use input in Programming way ,
- <script> function trackSearch(query) { document.write(‘<img src=”/resources/images/tracker.gif?searchTerms=’+query+'”>’);
- } var query = (new URLSearchParams(window.location.search)).get(‘search’);
- if(query) {
- trackSearch(query);
- }
- </script>
Now as we see window.location.search which carries user input What ever User search inside Application here if we Execute some javascript element such as <svg/onload=alert(“xss”);> Now it executed in location ‘search’
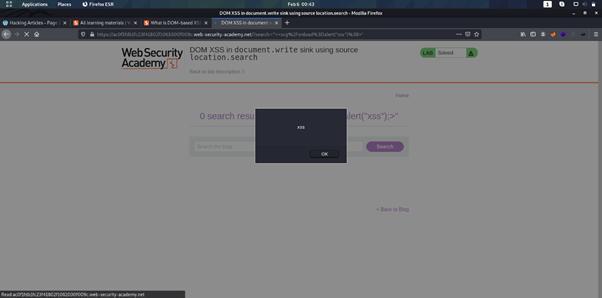
As we see Our script was successfully executed and look for code what happen inside it ,

Our Script Was executed inside (‘search’) cause due To improper validation of DOM Element This is how DOM XSS Work .
Hope now Your Doubt Cleared how Dom XSS work I would like to cover Some mitigation Steps To Protect against DOM XSS.
- Proper validation of user input As Use a JavaScript Framework
- Frameworks like Ember, AngularJS and React use templates that already check for possible XSS attacks and sanitize the user input.
- Use CSP to protect against issue Modern browsers support Content-Security Policies that allow the author of a web-page to control where JavaScript (and other resources) can be loaded and executed from.
Thanks For Reading……. See You In Another Blog!
Stick With Our Blog : https://securiumsolutions.com/
Author : Pallab Jyoti Borah | VAPT Analyst



