What is GitHub Dorking?
With the help of advanced search queries on the Github you can find sensitive information or exposed information on GitHub repositories. GitHub search functionality helps to locate the publicly available codes, credentials, api-keys, configurations, and the data that could be sensitive.Why GitHub Dorking is Important ?
Sensitive Data Exposure: GitHub is the platform commonly used by the developers to store the codes, and sometimes mistakes like accidentally pushing the sensitive data (API Keys, Passwords, Configurations, etc.) can lead to sensitive data exposure which can later be compromised by the hacker. If the hacker gets the credentials of a database he can dump or leak the whole information of the users(Credit card details, credentials,etc.) or company internal information (employee code, salary details, bank details).Common GitHub Dorking Techniques:
| GitHub Dork | About |
| filename:abcd | Search for files with a specific name in repositories |
| language:abcd | Search results based on the programming language of the files or repositories |
| org:abcd | Retrieves repositories belonging to a specific organization |
| extension:abcd | Locates files with a specific file extension |
| user:abcd | Retrieves repositories associated with a specific user or organization |
- client_secret
- user_password
- OTP
- authorization_bearer:
- auth
- user_pass
- passcode
- password hash
- api_key
- authentication
- client_id
- “api token”
- password
- api_token:
- secret
- “api keys”
- oauth
- user auth
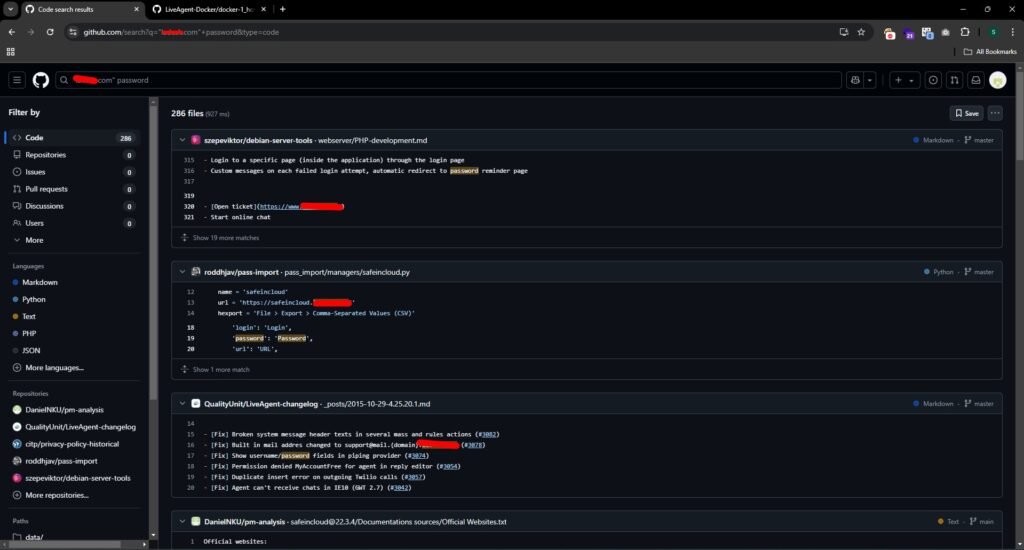
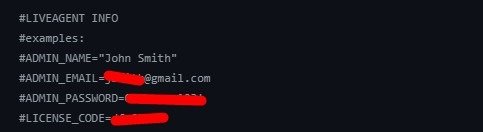 GitHub Dork to find all types of passwords – “target.com” password
GitHub Dork to find all types of passwords – “target.com” password




