Greeting everyone! Hope All going well Today In This Blog We will explore How To utilize the Content Discovery Phase While You’re Doing a Vulnerability assessment Against Your targeted Web Application. We Will explore one of the best tools ffuf which is fast web fuzzer.
Content:
- What is ffuf?
- Installation Of ffuf?
- Example usage of ffuf?
- What advantage of ffuf?
- Conclusion
What is ffuf?
As You may know some awesome tools such as dirsearch, dirb, go buster, and wfuzz basically default with Kali System or Some Linux distribution. FFUF which is named “Fuzz Faster You Fool” is an open-source web fuzzing tool, that discovers elements and content within web applications or web servers in a fast manner. Ffuf has different functionalities Such as fuzz directory, vhost discovery, and Fuzzing based On parameter GET as POST.
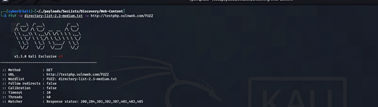
Installation of ffuf?
How To install ffuf As we know ffuf is developed By go language so before Installation You need to make the environment for go installation
To install ffuf :
- git clone https://github.com/ffuf/ffuf
- cd ffuf
- go get
- go build
go build which complied with Go Installation. To check the installation Guide through their official Website https://github.com/ffuf/ffuf
Example usage of ffuf?
First, let’s check if Your ffuf is successfully Installed Or Not
Command: ffuf -h
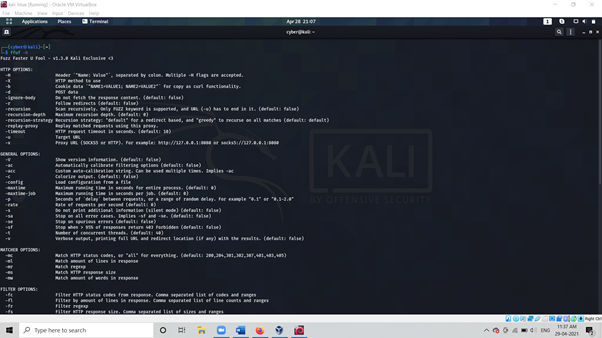
As above picture, we used -h to check its usage different flag which we will utilize During your Testing.
Basics flags:
- -u: the target URL
- -c: Add color to the output
- -r: follow redirects
- -t: timeout in seconds (default 10)
- -x: send through a proxy
Now let’s discover content, directory That is present On Our target Domain directory and contents that can be discovered with the following command :
Ffuf -w wordlist.txt -u http://target.com
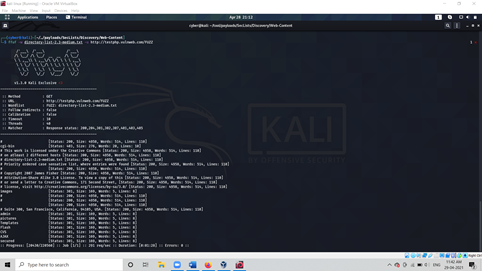
As above we used -w which carries our wordlist -u for specific URLs and made sure to set the endpoint as fuzz
Example.com/FUZZ . As an above picture, we have some directory Structures with 301, 403, 200, etc.
Now we only need a Directory which a response code is 200 And we want to skip the response and need specific extension type Here will use the command :
ffuf -w wordlist.txt -w http://yourdomain.txt/FUZZ -e php,.html -mc 200
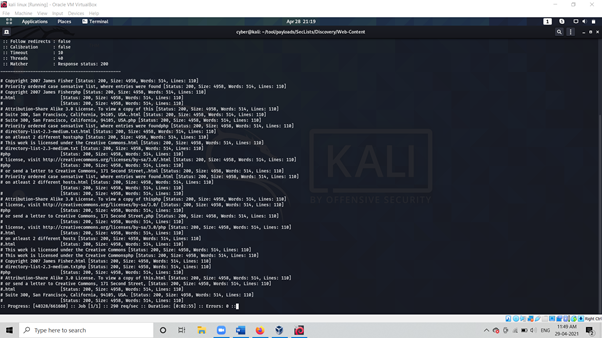
As above We see That the output is able to get a Specific Response with Specific File Extension.
Now fuzz specific Parameter field using ffuf. here we will use the command:
ffuf -w param.txt -u http://testphp.vulnweb.com/search.php?test=FUZZ -fs 4242
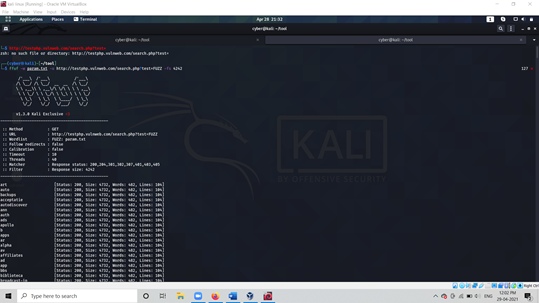
As above we set parameter list to fuzz against Specific field and This also assumes an response size of 4242 bytes for invalid GET parameter name.
Lookup website vhost using ffuf is also help us to lookup vhost against our target we will use command :
ffuf -w host.txt -u https://target -H “Host: FUZZ” -fs 4242
We used the default virtualhost response size is 4242 bytes, we can filter out all the responses of that size (-fs 4242)while fuzzing the Host – header.
This Article is Only for Educational Purpose if your Doing Penetration Testing this tool help you in your Recon process which is also possible to Manipulate backend confidential data .
Advantage of ffuf ?
- This is fast web fuzzer tool which allow us to fuzz against host , parameter , endpoint directory .
- We can specify different flags which utilize our testing phase.
- Ffuf is easy to use and open-source
Conclusion: In This Blog we discussed how To use ffuf tool we discus some of its example how utilize this tool on your testing phase . Hope You learn some thing new ! cheers !
Thanks For Reading……. See You In Another Blog!
Stick With Our Blog: Click Here
Author
Pallab Jyoti Borah
VAPT Analyst



