March 15, 2023 / By securium solutions
In the previous blog we learnt how to setup ICSim blog now we will know about few attacks with the lab setup. How to perform few attacks like Replay attack, Taking control of the Signal light, Taking Control of the Car Hacking, Car Doors and Taking Control of Speedometer (Car Hacking Lab).
Before that lets discuss about few of the topics that we need to know.
Introduction to CAN
Controller Area Network (CAN) is a communication protocol used in embedded systems and in-vehicle networks for real-time communication between microcontrollers and devices. It was originally developed by Robert Bosch GmbH in the 1980s and has since become a widely adopted standard for automotive and industrial applications.
CAN allows multiple nodes on a network to communicate with each other without a central computer. It uses a two-wire bus, a twisted-pair of wires, for transmitting and receiving messages. Each node on the network has a unique identifier and can send and receive messages based on that identifier.
CAN messages are transmitted using a time-triggered protocol, where each node has a specific time window during which it can transmit messages. This helps to prevent collisions and ensure reliable communication.
CAN is known for its high reliability, low cost, and ability to support real-time communication. It is widely used in the automotive industry for applications such as engine control, anti-lock braking systems, and airbag systems, as well as in industrial automation and other embedded systems.
Setting up the virtual Environment
You can run the following commands to set up a virtual can interface:
./setup_vcan.sh
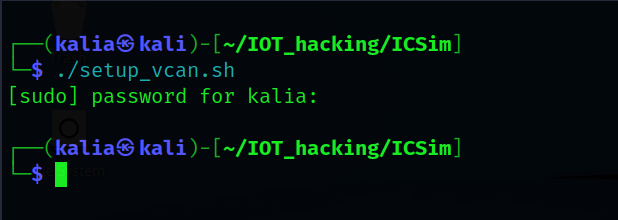
To verify vcan0 interface :
ifconfig vcan0

Running the dashboard
In order to run the dashboard, you could run a file called icsim with an argument vcan0, the interface we created earlier.
./icsim vcan0
The dashboard, including the speedometer, turn lights, brakes, and doors, will not function at this time. It is because there is no traffic on the vcan0 interface.To simulate traffic on interface vcan0, we must first start the controller using the following command :
./controls vcan0
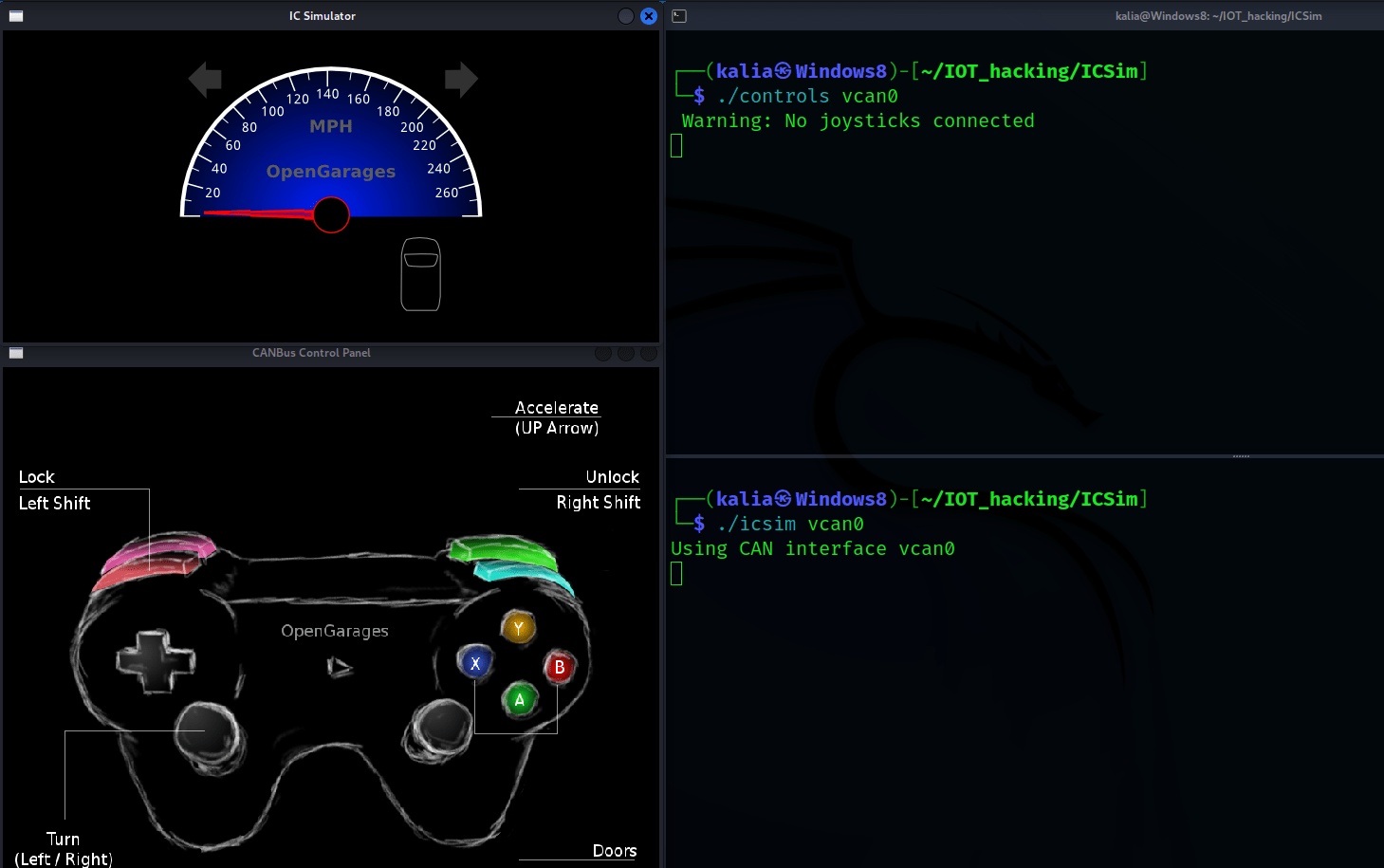
Controler Setting
ICSim Actions | Keys |
Accelerate | Up Arrow |
Left/Right turn Signal | Left/Right Arrow |
Unlock Front L/R Doors | Right-Shift+A,Right-Shift+B |
Unlock Back L/R Doors | Right-Shift+X,Right-Shift+Y |
Lock All Doors | Hold Right Shift key,Tap Left Shift |
Unlock All Doors | Hold Left Shift key,Tap Right Shift |
Sniffing the CAN frames generated by ICSim
To sniff the packets, we’ll use cansniffer, a utility provided by can-utils.You can start cansniffer by opening a new terminal and using the following commnad for Car Hacking Lab:
cansniffer -c vcan0
The -c option is used to indicate the changes in bytes of the frame.


The CAN frames show very quick changes, making it difficult to keep up with the rate of communication.This communication would take place quickly in a real car.Arbitration ID filtering can help you keep up.
If you only want to see unique frames, press ‘—’ and then ‘000000’ followed by the Enter key.This will clear all the IDs from cansniffer, and you can then filter out by pressing + followed by ID and then entering the key.
To perform a replay attack with ICSim, you must first start ICSim and be able to see the frames using cansniffer.
Now we will use candump with the -l option to log and save the frames. In the meantime, we will increase the throttle and turn on the turn signal indicator by pressing the left and right arrow keys.
Also, to lock all doors, press “right shift + tap left shift,” and to unlock them, press “left shift + tap right shift”.
candump -l vcan0
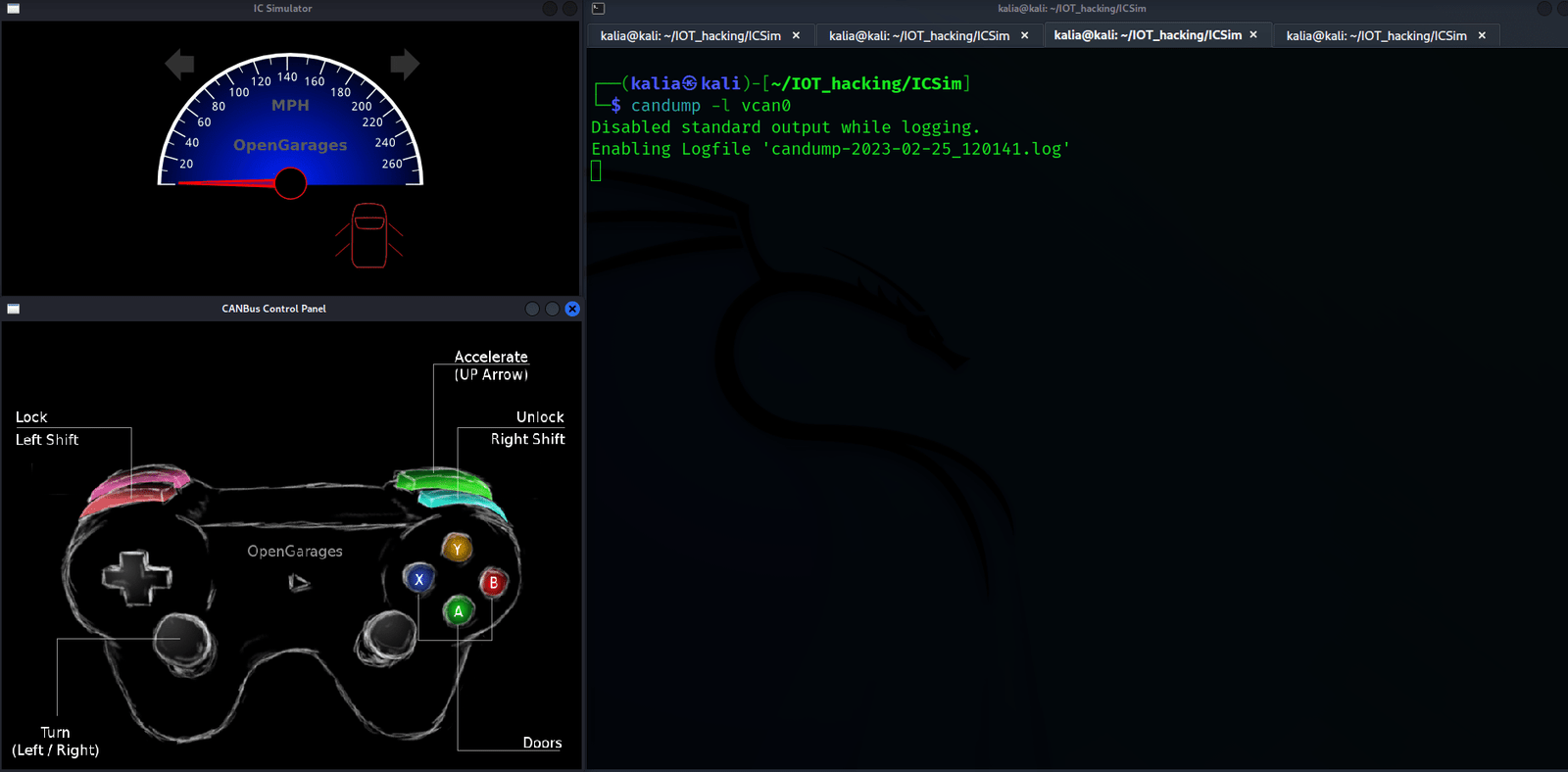
Now candump will now be stopped, and a file called candump-XXXXX.log will be created.
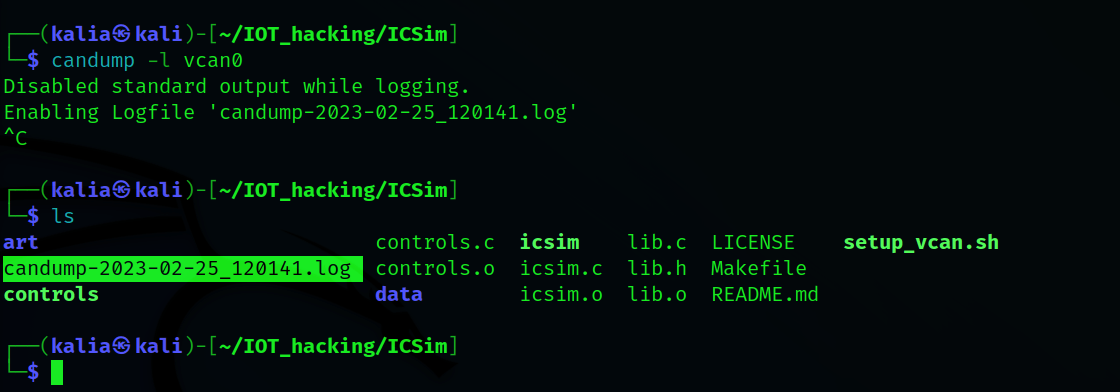
Canplayer will be used to replay those packets.As we’ll be using a file as input to canplayer, the -I option must be enabled.
canplayer -I candump-XXXXXX.log
You can see that a replay attack has been performed, the turn signals, speedometer and door lock should be working as you had done earlier.
Author
By Monika Sharma
Cybersecurity Intern





