Greeting Everyone! Today we will learn how to exploit buffer overflow using with immunity debugger and mona modules.
Steps I covered in buffer overflow.
- Spiking
- Fuzzing
- Finding the offset
- Overwriting the EIP (Extended instruction pointer)
- Finding the bad characters
- Finding the right module
- Generate shell code and gain shells
Download vuln-server – https://github.com/stephenbradshaw/vulnserver
Download immunity debugger – https://www.immunityinc.com/products/debugger/
Download the mona module – https://github.com/corelan/mona
What is buffer overflow?
Buffers are memory storage regions that temporarily hold data while it is being transferred from one location to another. A buffer overflow (or buffer overrun) occurs when the volume of data exceeds the storage capacity of the memory buffer. As a result, the program attempting to write the data to the buffer overwrites adjacent memory locations.
For example, a buffer for log-in credentials may be designed to expect username and password inputs of 8 bytes, so if a transaction involves an input of 10 bytes (that is, 2 bytes more than expected), the program may write the excess data past the buffer boundary.
Buffer overflows can affect all types of software. They typically result from malformed inputs or failure to allocate enough space for the buffer. If the transaction overwrites executable code, it can cause the program to behave unpredictably and generate incorrect results, memory access errors, or crashes.

Setup mona module :-
copy mona.py from download folder then go to C:Program FilesImmunity IncImmunity DebuggerPyCommands and paste mona.py
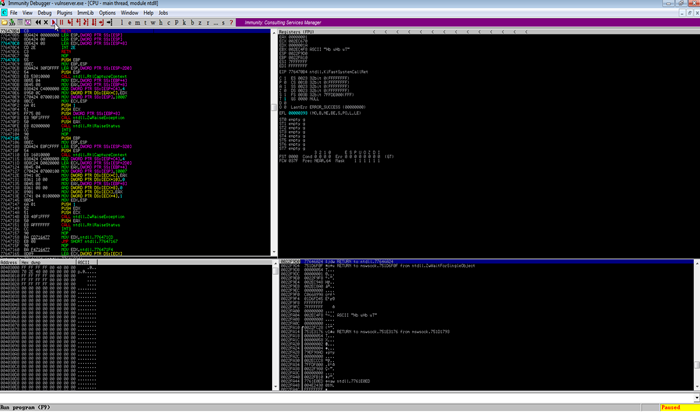
Now right click on immunity debugger and run as administrator When Immunity loads, click the open file icon, or choose File -> Open. Navigate to the vulnserver folder location and then select vulnserver.exe and click on “open” by default application paused click on play button to run the vulnserver
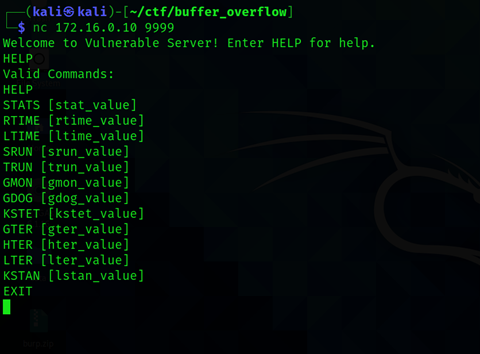
1. Spiking – If the software running with two or more input parameters so we can use a spiking script to check which input parameter is vulnerable to buffer overflow vulnerability. When we connect with nc to vuln-server there is one option present HELP now we see too many options. We will check each an every option with spiking.
Spiking script – now we create a spiking script I know the TRUN parameter is vulnerable but you can try with each and every parameter.
Where choose input parameter:- in the s_string(“ VALUE ”) put the name of parameter.
Save file with .spk extension
- s_readline();
- s_string(“TRUN “);
- s_string_variable(“0”);
Now the time to run the script
generic_send_tcp <ip of target machine> 1337 spiking.spk 0 0
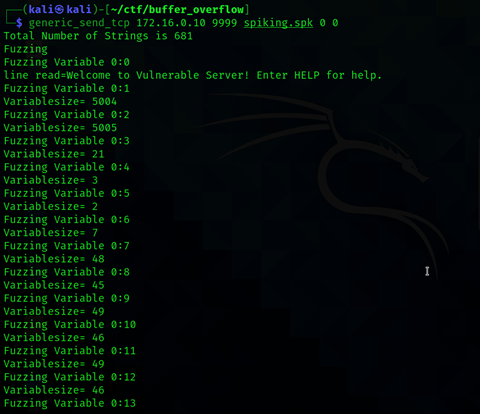
After some time vulnserver stopped responding

Conclusion :- In this section we learned what is buffer overflow attack, download vulnserver, download immunity debugger, how to set up mona module, how to spinking every input parameter for check buffer overflow vulnerability. In the upcoming section I will cover all the process one by one.
Thanks For Reading……. See You In Another Blog!
Stick With Our Blog: Click Here
Author
Shubham Jaiswal
WEB VAPT (Intern)



