Enumeration is one of the crucial phase in penetration testing. The result of the enumeration can lead to discovery of vulnerabilities that can be directly exploited. Enumeration allows to gather information such as usernames, group names, host names, algorithms etc.
The Nmap Scripting Engine (NSE) is one of the strong features on Nmap allowing users to write simple scripts to automate tasks in networking.
Today, we will be focusing on how to enumerate a target IP using Nmap Scripting Engine (NSE).
We will be making use of Metasploitable 2 as our target system.
Firstly, we will be running a basic scan on the target IP
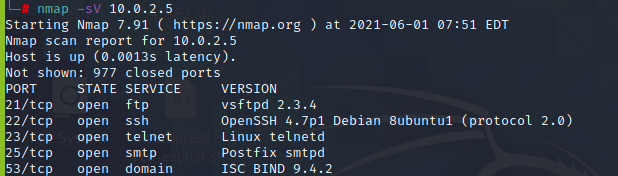
After the scan is done, we now know which ports and services are running on the network.
Nmap has pre-built scripts for which you can use to enumerate the target.
However, the list is quite long and can be difficult to search for the desired script. To avoid this, we will make use to ‘grep’ to refine our search.
Our target service is ssh, so we will be searching for the scripts using the keyword “ssh”.
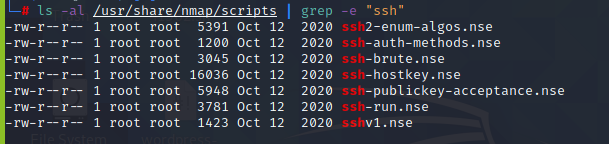
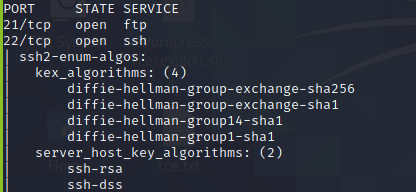
We wish to find algorithms used for ssh, so we have selected ‘ssh2-enum-algos.nse’ script.
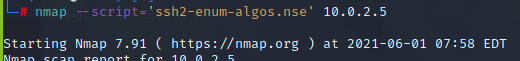
Here are the algorithms used for ssh which can be used to determine any weak algorithms used.
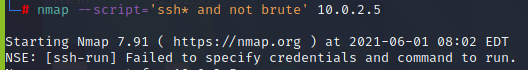
Furthermore, w can also make use of wildcard ‘*’ to enumerate using all the scripts available for a particular service.
We used ssh* and not brute to avoid brute forcing the target.
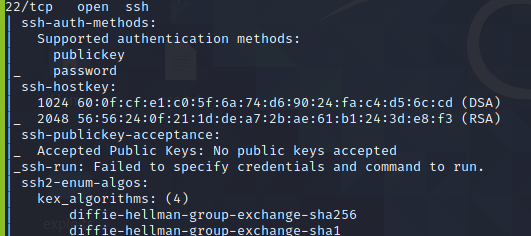
This blog demonstrated the use of nmap scripts. However, you can add more creativity to your search to get enhanced results.
Author: Mohammad Usman Rais (IT Security Engineer)



