As we move forward to our next blog in hardware hacking series, we will be focusing on firmware analysis. In our previous blog we have discussed the methodology for hardware hacking
Let’s first discuss what exactly is firmware. It is software program permanently carved into a hardware device like keyboards, hard drives etc. It is then programmed in a way that gives permanent instructions that allows the devices to communicate with other devices and perform basic input/output tasks. It is stored in the flash ROM of the hardware device. The firmware can be erased and also rewritten.
Firmware Analysis
Firmware analysis can be really useful as it gives a person firmware files, including archives, compressed data and filesystems. There various types of sensitive information and vulnerabilities that could be discovered after performing a firmware analysis.
Below are the few vulnerabilities listed:
- Third party components
- Default or undocumented credentials
- Hardcoded cryptographic secrets
- Backdoor accounts
- Vulnerable service configuration
Steps for firmware analysis:
1) The first step of firmware analysis is to obtain the firmware which can be extracted from a device or found on vendor website.
2) The next step is the extraction of firmware files from the downloaded firmware. This can be done using some tools that we have discussed in this blog.
3) The final step will be finding sensitive files and directories within the extracted firmware files.
In this blog we have provided a practical explanation of firmware analysis, and by following the steps one can easily perform a firmware analysis.
As we have discussed above the steps of firmware analysis, we will download the firmware file WNAP320FirmwareVersion2.0.3.zip in the directory /home/it/tools/firmware-analysis-toolkit
Then we will check the details of the file WNAP320FirmwareVersion2.0.3.zip using binwalk
And after checking the details of the file, we will then extract the file WNAP320FirmwareVersion2.0.3.zip using binwalk -e

The extracted files will be placed in the directory _WNAP320FirmwareVersion2.0.3.zip.extracted
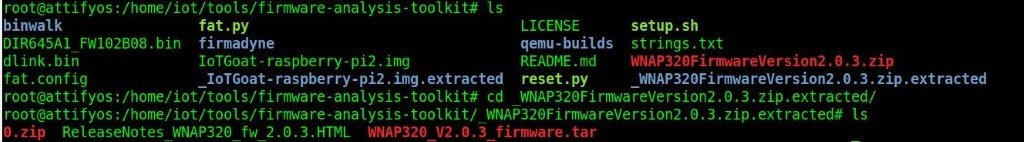
After entering into _WNAP320FirmwareVersion2.0.3.zip.extracted. We see a file with name rootfs.squashfs .
We will now perform the same previous extraction process on that file using binwalk –e
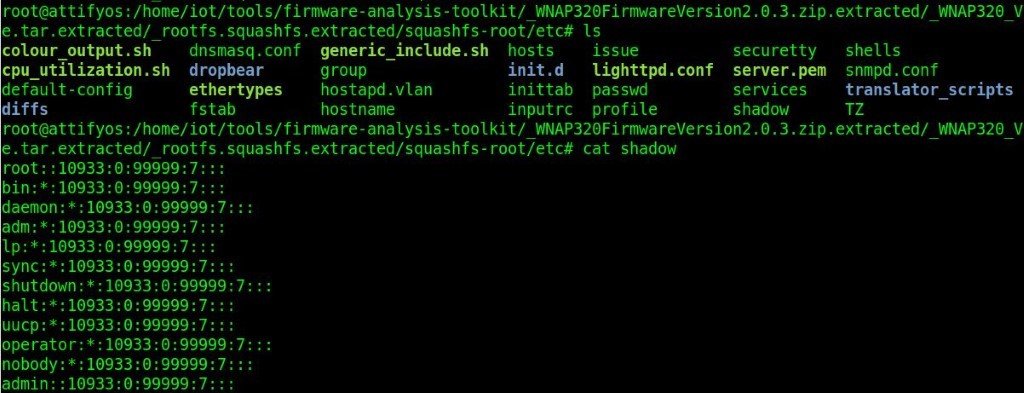
It will give the extracted firmware files in the directory _rootfs.squashfs.extracted. We will enter into the directory /_rootfs.squashfs.extracted/squashfs-root/etc
Here we will be able find useful files like shadow and passwd which can give you sensitive information like login credentials of admin and other users in the form of hashes which be easily cracked using a hash crack software. It’s just an example to show you how to reach to a point where we can discover sensitive information. While performing the actual firmware analysis we can have a much broader scope.
Another way to discover sensitive files is to upload the firmware on IoT Auditor which will give you a list of files that are sensitive.

After completing a successful firmware analysis we can move on to the next process that is firmware emulation which allow us to run the actual firmware and discover more information. We will be covering firmware emulation in our next blog.
Authors: Mohammad Usman Rais & Vishal Thakur | Network Security Analyst Interns



