Greeting Everyone! Hope All is going good today in this blog we are going to Learn How to Utilize Your Testing work using nc with banner grabbing , file transferring , Linux reverse shell, grabbing the http banner etc. How Linux nc command help us to perform different activity .
Before Start Example session Your Question is what is netcat(nc)?
Netcat know as nc command which is linux cli based command network utility which use tcp and udp connection to read and write a network connection . nc is used By an Tester or an attacker in different way . netcat can connect to destination through a anonymous proxy server . it Encrypt communication over SSL & over IPv4 IPv6. This tool is very Help
Usage Of netcat (Basic Command of netcat -nc) Lets see how this tool work deeper ?
First run Your Terminal and run command nc -h which give us all functionality different flag set that we can utilize using nc flag which help us to gather more information and easily create reverse connection through another machine using cli.

As Above picture we see There is different set of flag that we can use in our further step.
Now, Utilize port Scanning with nmap Here we can perform against our target system using nc
Used command : nc -v -n -z 192.168.0.82 10-50 Here -v verbose [use twice to be more verbose] -n numeric-only IP addresses -z [used for scanning]
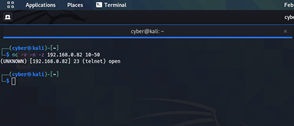
As above picture we see target has open 23 telnet we scan for 10=50 and found one port is open .
Now utilize banner grabbing using nc , Here we will perform banner grabbing using nc we will use command ,
Used Command: nc IP.0.0.1 22
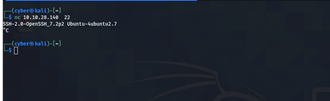
As above picture we see we banner garb against port 22 and we are able to manipulate version of ssh .
Now utilize netcat to grab banner http , Here we will see how netcat help us to grabbing http banner here we will use command ,
Used command: printf “GET / HTTP/1.0rnrn” | nc IP here used printf to print response which carries “GET / HTTP ”
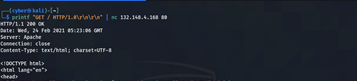
As above picture we see How we can grabbing http response using netcat tool .
Conclusion : Hope You Learned something new This blog covered how we can utilize netcat to gather different information no matter is target is global or local in above we also perform some eg: from global target hope You enjoyed this blog In next blog we will learn how to use nc to get reverse shell for both windows and linux system .
Thanks For Reading……. See You In Another Blog!
Stick With Our Blog : https://securiumsolutions.com/
Author : Pallab Jyoti Borah | VAPT Analyst



