Home » Risk Assessment Services » VAPT Services » API & Web Applications Penetration Testing
In the fast-paced world of technology, APIs and web applications play a critical role in businesses of all sizes. These applications serve as the backbone of many organizations, connecting various systems and enabling the exchange of data. However, with the increasing reliance on these technologies, it’s imperative to ensure their security. This is where API & Web Application Penetration Testing comes into the picture.
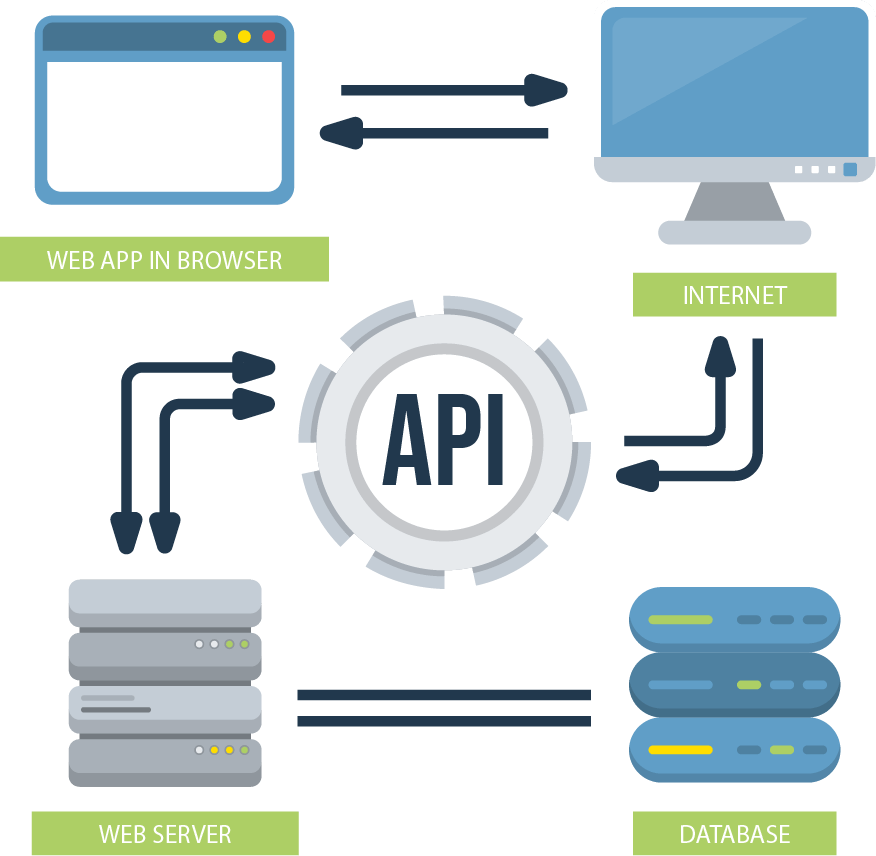
API Web Application Penetration Testing is a security process that involves simulating real-world attacks to identify vulnerabilities in APIs and web applications. The goal is to find and fix any security flaws before they can be exploited by malicious actors. In this way, businesses can proactively protect themselves against data breaches, unauthorized access, and other security incidents.
As the reliance on APIs and web applications continues to grow, it’s essential to ensure that these systems are secure from potential threats. API & Web Application Penetration Testing is a critical component of a robust security program, as it helps to identify and remediate vulnerabilities before they can be exploited by malicious actors.
API & Web Application Penetration Testing is required because it helps organizations to comply with industry regulations and standards. Many industries, such as finance and healthcare, are subject to strict regulations that require the protection of sensitive information.
In addition, API & Web Application Penetration Testing is a proactive approach to security. By finding and fixing vulnerabilities before they can be exploited, organizations can prevent security incidents from occurring.
Finally, API & Web Application Penetration Testing is necessary because the threat landscape is constantly evolving. New threats emerge every day, and it’s important for organizations to stay ahead of the curve. API & Web Application Penetration Testing can help organizations to identify and remediate vulnerabilities that may not have been discovered through other means, such as automated security scans.
Our Methodology to perform API & Web Application Penetration Testing
Preparation and Planning: During this stage, we work with our clients to understand their specific needs and requirements. We will also obtain all necessary permissions and review the scope of the API & Web Application Penetration Testing.
Information Gathering: During this stage, we will gather information about the target API & Web Application, such as the technology used, architecture, and any existing security measures.
Threat Modeling: During this stage, we will identify potential threats to the target API & Web Application and prioritize them based on the likelihood and impact of exploitation.
Testing: During this stage, we will use a combination of automated tools and manual testing to identify and validate vulnerabilities in the target API & Web Application. Our testing methodology includes both black box and white box testing, to ensure a thorough assessment.
Reporting: After the testing is complete, we will provide our clients with a comprehensive report that includes a detailed analysis of all vulnerabilities identified, along with recommendations for remediation. Our report is easy to understand, and includes clear, actionable recommendations.
Remediation and Verification: After the report is provided, we will work with our clients to help them remediate any vulnerabilities identified. We will also verify that the remediation has been effective.
REST (Representational State Transfer) is a lightweight, flexible API that is designed to work with the HTTP protocol. It uses a simple, standardized structure and is easy to implement and use.
SOAP (Simple Object Access Protocol) is a more complex API that is designed for secure, enterprise-level applications. It uses XML to encode its messages and provides a more secure and reliable way of exchanging data.
Access control: Access control determines who has access to what information and functionality in the API & Web Application. If access control is not implemented correctly, an attacker may be able to bypass it and gain access to sensitive information.
Input validation: Input validation is one of the most critical areas for API & Web Applications. If inputs are not validated properly, an attacker may be able to inject malicious code or data into the system.
Data storage: The way in which data is stored and processed is critical for the security of API & Web Applications. If data is not stored securely, it may be vulnerable to attack. For example, storing sensitive information in plaintext or using weak encryption algorithms can make it easier for an attacker to access the data.
Error handling: Poor error handling can lead to sensitive information being disclosed to attackers. For example, error messages that reveal too much information about the system can make it easier for an attacker to identify and exploit vulnerabilities.
Session management: Session management is critical for API & Web Applications, as it determines how user sessions are managed and authenticated. If session management is not implemented correctly, an attacker may be able to hijack user sessions and gain unauthorized access to sensitive information.
Access to the target system: To perform a penetration test, we must have access to the target API & Web Application. This may involve obtaining permissions from the client or accessing a test environment that has been set up for this purpose.
Information about the target system: We need to gather information about the target system, such as the technology used, architecture, and any existing security measures. This information will help us to prioritize our testing and ensure that we cover all relevant areas.
Testing tools and techniques: We use a combination of automated tools and manual techniques to perform our penetration tests. The tools and techniques we use will depend on the specific requirements of the target system and the scope of the test.
Reporting and remediation: After the test is complete, we will provide our clients with a comprehensive report that includes a detailed analysis of all vulnerabilities identified, along with recommendations for remediation. Our report is easy to understand and includes clear, actionable recommendations.
Remediation and verification: After the report is provided, we will work with our clients to help them remediate any vulnerabilities identified. We will also verify that the remediation has been effective.


Securium Solutions is the ideal choice for API and Web Application Penetration Testing services due to its exceptional expertise and comprehensive approach.
Skilled Ethical Hackers: Our team consists of highly skilled ethical hackers who possess deep knowledge and experience in identifying vulnerabilities and weaknesses in APIs and web applications.
Thorough Testing Methodology: We follow a systematic and rigorous testing methodology, ensuring that every aspect of your API and web application is thoroughly examined for potential security flaws.
Customized Approach: Our experts tailor their testing approach to suit your specific requirements, considering the unique characteristics and functionalities of your APIs and web applications.
Advanced Tools and Techniques: We leverage cutting-edge tools and techniques to simulate real-world attack scenarios, uncovering vulnerabilities that could be exploited by malicious actors.
Detailed Reporting: Our comprehensive reports provide a clear overview of identified vulnerabilities, their potential impact, and actionable recommendations for remediation.
Securium Solutions uses a combination of automated tools and manual techniques to perform API & Web Application Penetration Testing. Our team of experts has extensive experience in this field, and we use a methodology that is designed to identify all relevant vulnerabilities in the target system. We start by gathering information about the target system, and then use this information to prioritize our testing and ensure that we cover all relevant areas.
No penetration testing service can guarantee that all vulnerabilities will be found. However, at Securium Solutions, we use a comprehensive testing methodology and the latest tools and techniques to ensure that we identify as many vulnerabilities as possible. Our team of experts has extensive experience in this field, and we are committed to providing the highest quality of service to our clients.
Securium Solutions understands the importance of protecting sensitive information, and we have strict protocols in place to ensure that all sensitive information is handled securely. Our team is trained in the proper handling of sensitive information, and we use encrypted communication channels and secure data storage to ensure that all information is protected.
Yes, we can provide sample reports from previous API & Web Application Penetration Testing engagements to give you an idea of the level of detail and quality of our reporting. These reports will give you an idea of the types of vulnerabilities that we identify, the methods that we use to identify them, and the recommendations that we make for remediation.
At Securium Solutions, we are committed to providing the highest quality of service to our clients, and we are always available to answer any questions that you may have about our API & Web Application Penetration Testing services. Whether you need a one-time test or ongoing monitoring and testing services, we have the expertise and resources to meet your needs.