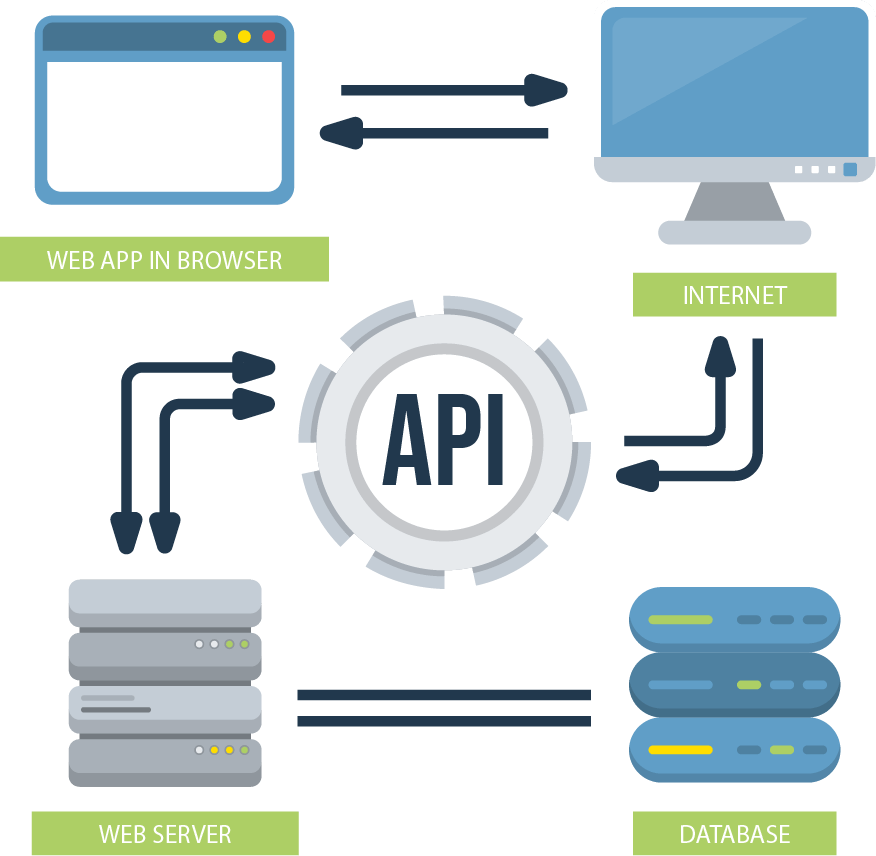
Why API & Web Application Penetration Testing Required?
As the reliance on API & Web Applications Penetration Testing In UAE continues to grow, it’s essential to ensure that these systems are secure from potential threats. API & Web Applications Penetration Testing In UAE is a critical component of a robust security program, as it helps to identify and remediate vulnerabilities before they can be exploited by malicious actors.
API & Web Applications Penetration Testing is required because it helps organizations to comply with industry regulations and standards. Many industries, such as finance and healthcare, are subject to strict regulations that require the protection of sensitive information. API & Web Application Penetration Testing can help organizations to meet these requirements and to avoid costly penalties for non-compliance.
In addition, API & Web Application Penetration Testing is a proactive approach to security. By finding and fixing vulnerabilities before they can be exploited, organizations can prevent security incidents from occurring. This can help to protect sensitive information, maintain the trust of customers and partners, and minimize the impact of a potential security breach.
Finally, API & Web Application Penetration Testing is necessary because the threat landscape is constantly evolving. New threats emerge every day, and it’s important for organizations to stay ahead of the curve. API & Web Application Penetration Testing can help organizations to identify and remediate vulnerabilities that may not have been discovered through other means, such as automated security scans.