Greeting Everyone ! Today We are going to discuss How android content provider are vulnerable for exploit . How an attacker can Take advantage Of exported content provider it . We will Learn How drozer help us to verify Vulnerable content provider If your doing penetration testing Against Your targeted Website.
What Is Content Provider ?
In Android Content provider are act to store data application In one page and make it available for different Application whenever it need. We Use content provider to allow other application to access data with some specific requirement.
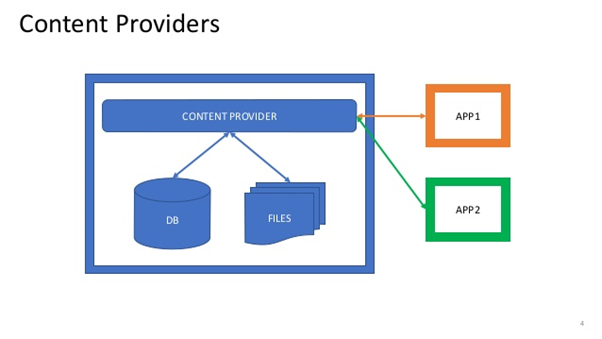
How Android Application Are Vulnerable for Exploiting Content Provider?
Now here we will use tool drozer which make our testing phase more easy drozer is design for To automatically found Vulnerable activity , content provider And it will assessment against Our targeted Application.
To Install Drozer: drozer
Now For Testing Purpose We have Vulnerable apk Android-InsecureBankv2
Genymotion For Virtual Android environment.
Now, Run drozer From Your terminal By using command:
- Drozer console connect
Now List all application packages available Inside Your Phone we will use command:
- Run.app.package.list
Now to find out exported content provider from Our targeted Apk package we will iuse command :
- run app.provider.info -a com.android.insecurebankv2
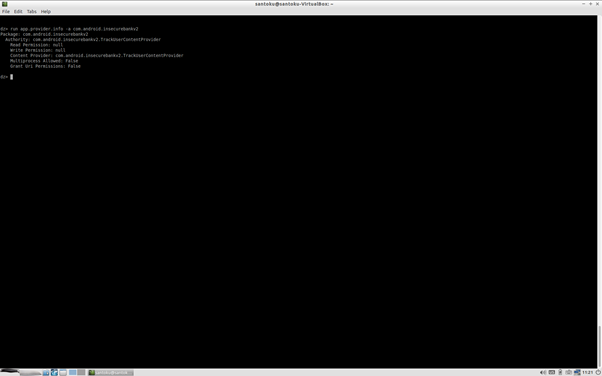
As above repose we found read and write permission are null Now we can extract vulnerable content provider using drozer,
Now we will find out accessable content uris using drozer we will use command:
- run scanner.provider.finduris -a com.android.insecurebankv2
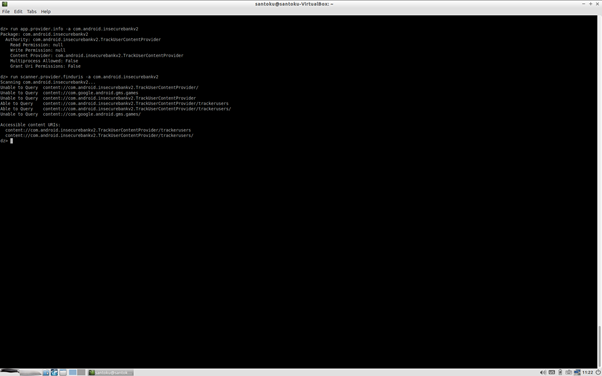
Now we see we have all Content provider Which we can access we see content:// uri which is accessable .
Now we can access query Vulnerable content provider we will use command:
- run app.provider.query content://com.android.insecurebankv2.TrackUserContentProvider/trackusers
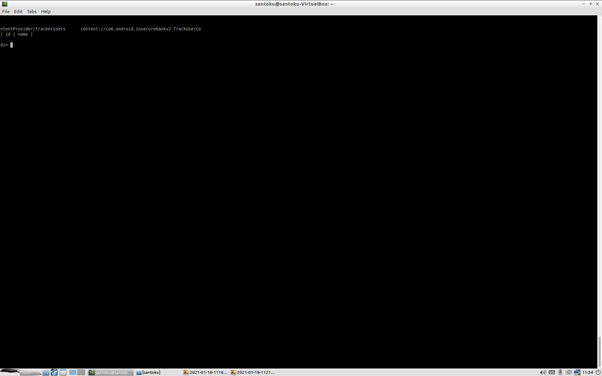
Now we found Accessable Content provider trackusers which an bad actor can access vulnerable uri This returns a table of usernames and user ID’s from an SQLite database that tracks the login of users as implied by the name of the content provider.
Conclusion: In this walkthrough we Tested Against Android Vulnerable content Provider How This content provider are Vulnerable We used drozer to make our testing phase more easy This is basic idea how we can exploit how this content uri can be access by an attacker.
References: https://medium.com/bugbountywriteup/android-insecurebankv2-walkthrough-part-2-429b4ab4a60f
Thanks For Reading……. See You In Another Blog!
Stick With Our Blog : https://securiumsolutions.com/
Author : Pallab Jyoti Borah | VAPT Analyst



