Hardware Hacking can be really interesting and fun to do and often times a person can become helpless if he does not follow the right approach. In this blog, we intend to guide you through the process of hardware hacking. A direction of how to approach a hardware device and what steps you need to follow in order to extract useful information from the device.
The following are the steps involved in a Hardware hacking methodology:
1 Information gathering and reconnaissance: The first step is to identify all the elements present on the device hardware and then look online and try to identify the datasheets for those elements.
Once you find the datasheet, tons of information can be found about the target in the datasheet.
In many popular hardware devices, you might be able to find information online.
2 Identify the communication interfaces: Information is shared among the devices with the help of common protocols. It is always useful to identify them.
The protocols are divided into two groups
1) Serial: in a Serial interface, the data gets transferred one bit at a time, which even though slower than parallel, but has an advantage of requiring a lesser number of pins.
2) Parallel: Parallel interfaces allow multiple bits of data exchange are happening at the same time, thus requiring a large number of pins to facilitate that
3 Finding hardware communication techniques: The pinouts which we need to identify are Tx, Rx, GND, and Vcc.
1) GND (Ground): The first step is to identify the GND which does not require any power and can be done by using the multimeter on continuity mode and then connecting the red probe to one of the pins and the black probe to a metallic surface. Try to test out each of the pins, and once you hear a beep sound, that pin is the GND.
2) Tx (Transmit): This requires power on the device. Following the previous procedure of sticking the black probe to the metallic surface and the red probe to each of the pins, once a voltage fluctuation is observed and rests on a high value will give you the Tx.
3) Vcc (Voltage Common Collector): The pin which has a constant high value upon sticking the red probe and keeping the black probe on a metallic surface is the Vcc.
4) Rx (Receiver): The pin which has significantly less voltage upon sticking the red probe and keeping the black probe on a metallic surface is the Rx.
4 Connecting the device to our system: In order to maintain communication between the device and the attacking system middle device needs to be connected which can be a UART or a raspberry pi.
UART: UART stands for Universal Asynchronous Receiver/Transmitter. It’s not a communication protocol like SPI and I2C, but a physical circuit in a microcontroller, or a stand-alone IC. A UART’s main purpose is to transmit and receive serial data.

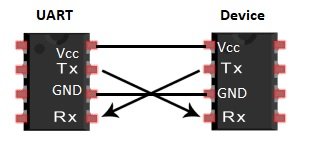
The following connections should be made in order to maintain a communication.
Vcc – Vcc
GND – GND
Tx – Rx
Rx – Tx

The following connections should be made in order to maintain communication.
Vcc – Vcc
GND – GND
Tx – GPIO
Rx – GPIO
(GPIO are the general purpose I/O pins which can be used for any general purpose).
5 Software exploitation using connected hardware: Any IoT device you use, you will be interacting with firmware, and this is because firmware can be thought of as the actual code that runs on an IoT or embedded device here you can either extract the firmware or dump (download) the contents from the firmware. If you manage to extract the firmware, you can have access to sensitive information (user info, passwords) and directories that were present on the device.
6 Backdooring: Finally after having access to the shell, you can maintain the access by uploading a payload in order to use the device in the future.
We hope you find this blog useful. Here is the link for our next blog in the hardware hacking series.
Author
Md Usman Rais
Cyber Security Intern




