Hello Everyone
Password Penetration Testing
In this article, we will get to know about password penetration testing and various ways to pen-test them. We will also cover things like where passwords are stored in Windows/Linux, common attacks, and good password hygiene to follow. Also, some points to consider in a password pentest.
What is a password:
A password is a secret series of characters allowing a user to access a computer, program, or file. A super secure password has all of the following features:
- Letters: Can be English or another language and a mixture of small and capital letters. A-Z and a-z.
- Number: any combination from 0-9
- Special characters: @!#$?>- and many more
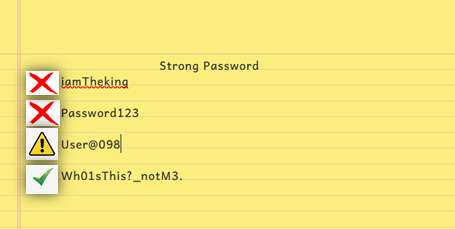
Another thing to note is that a password shouldn’t be a dictionary word and should be kept as long as possible to make password cracking difficult. And having MFA enabled can make hackers rethink their target.
Need for a secure password:
- Weak/guessable passwords have a very big impact leading to a full system/ company takeover.
- Users personal data can be fully leaked just by having a weak password.
- Users can suffer financial losses and mental issues following the impact.
- It can help categorize different users for proper access control.
Passwords can be stored in the system in the following ways: Clear text (self-explanatory),
obfuscated(password can be reverted back to plain text), and hashed(no way to
get original text even if the attacker has it).
Password cracking techniques:
Following are some of the ways in which an attacker can try to crack your passwords:
- Dictionary attack: A user’s account is tried for various passwords from a dictionary file, which is a list of dictionary words.
- Brute Forcing attack: The tool tries to use all possible combinations to break passwords.
- Hybrid attack: add numbers and symbols to a dictionary file and we have a hybrid attack.
- Syllable attack: this attack is composed of mixing dictionary and brute force attacks.
- Rule-based attack: This attack is possible once an attacker has some clues as to the pattern that his victim uses in password creation or due to site restrictions.
Tools: Cain & Abel
Categorization of password attacks:
Passive online attacks:
- Wire sniffing
- MitM
- Replay attack
Active online attacks:
- Password guessing
- Keyloggers/spyware/malware
- Hash injection attack
Offline attacks:
- Rainbow attack
- Pre-computed hashes
- Distributed network attack
Non-digital attacks:
- Shoulder surfing
- Dumpster diving
- Social engineering
Tools:
Wireshark, TCPDUMP, Ettercap, FGPDUMP, RainbowCrack, and ElcomSoft distributed password recovery.
Windows password storage:
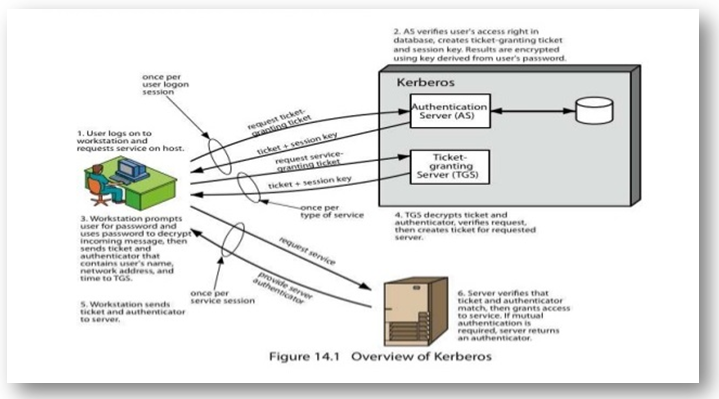
Windows users’ passwords are hashed and then stored in the Security Accounts Manager (SAM) db. LM and NTLM authentication protocols were used in the past, but now Microsoft has shifted to more secure Kerberos.
SAM file can be accessed from C:windowssystem32configsam
Linux password storage:
Previously, Linux would store user info and hashed passwords in a file called “ETCPASSWD” readable by non-root users. Nowadays, Linux stores ‘x’ in place of hashed passwords in “ETCPASSWD” and another file, readable by only root, “ETCSHADOW” or “ETCSECURITYPASSWD” including hashed passwords and other details.
Password penetration testing:
We have already covered what’s pen testing in our previous blogs so refer to that if you haven’t already. Following are some of the steps to be followed while doing a pentest, mainly dealing with passwords.
1. Id target’s personal profile.
Gain target personal details from social media sites like Facebook, Instagram, Twitter, and Google and from job searching sites like LinkedIn, naukari.com, monster, internshala. Other people searching sites like pipl.com, intelius.com, searchbug.com, 411.com, and 123people.com can also be used but they are either paid or not effective.
2. Non-digital attacks (refer above)
3. Build a custom wordlist specific to the target
After collecting details about the target, we use dictionary builder tools to create a wordlist or make one manually of possible passwords.
4. Password guessing
Try to use the default creds associated with that particular device/service. Also, having a custom wordlist try to use it to see if we gain access using automation.
5. Perform each of the password attacks mentioned before.
6. Extract and decipher the sam and shadow files.
7. Use automated/online tools to crack passwords: l0phtcrack, john the ripper, Ophcrack, LSASecretsView.
Good Password management hygiene:
- Following are some of the measures to follow to keep passwords safe and strong:
- Have policies for password creation, management, and expiration.
- Use multi-factor authentication(MFA) and auto account lockouts after some idle time.
- Storage and transmission of only salted hashed passwords.
- Implement proper authorization controls to prevent data leaks.
- Use onscreen keyboards to defeat keyloggers.
- Prevent account logins after a certain number of failed attempts or from unknown locations/time without MFA.
Conclusion:
In this article, we learned about password management and some good practices to follow including password penetration testing basics. In my next blog, we will discuss other penetration testing topics so stay tuned.
Author
Vishal Thakur
Network Security Analyst Intern



