Greeting Everyone ! Today in this blog post we will explore about SSTI Vulnerability this vulnerability is Based On Injection attack . In this Blog we will see How SSTI Work how to find this Vulnerability How to mitigate against Risk.
What is SSTI Server side template injection?
Every website using template engine this helps to display the dynamic data over the web page template engine are used to display information about user and products iteam of content.. Some time Developer mistakes Unsafely embedding user input in templates enables Server-Side Template Injection, this based on attack scenario XSS Or directly attack web servers’ internals structure and often possible for Remote Code Execution (RCE).
Some Of Most Popular Templates That used:
- Smarty,Twigs -> php Template
- Velocity, Thymeleaf –> java Template
- Cheetah, juno -> python Template
How It work?
Supposed Below Request sent By us To the server As To execute against Template injection polyglot payload which is a sequence of special characters and got executed , EG:
http://site.com?value={{7*2}} -> Output : 14

Example Attack:
Here we have Our lab for demonstrate Against SSTI Vulnerability Now we have vulnerable web app ,

As above lab we have Site which is based On Shoping site Now For Lab We required Burpsuite And Now After Setup burp capture View order request through Burp ,
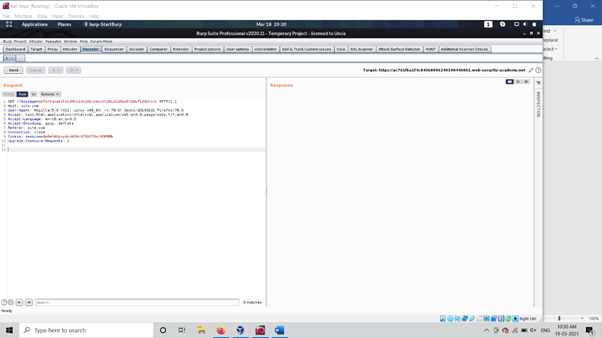
As above picture we see It gives us a parameter which carries some message that product is out of scope now We have One parameter message= For checking vulnerability . Now Change value of message parameter and execute our polyglot payload <%= 7*7 %>
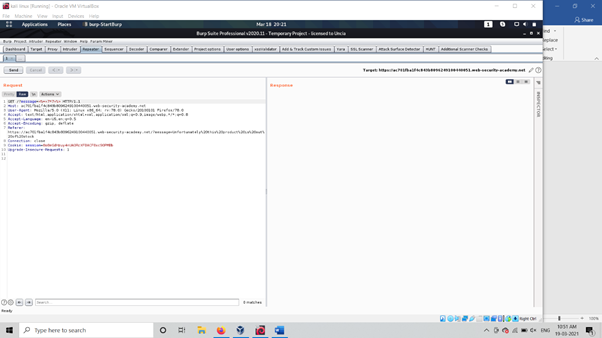
As above picture we change message parameter value Now As output of Request from server we manipulated as below screenshot:
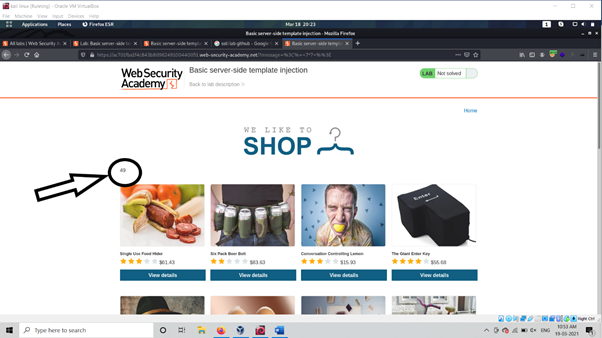
As above picture as we manual for the template engine and output is t 49 that answer of 7*7 .
Now How template injection could lead to delete Internal structure Or cause to OS command injection , As now we have One file Which os carlos file now using Some command line interface we able to delete those files , As Below Screenshot:
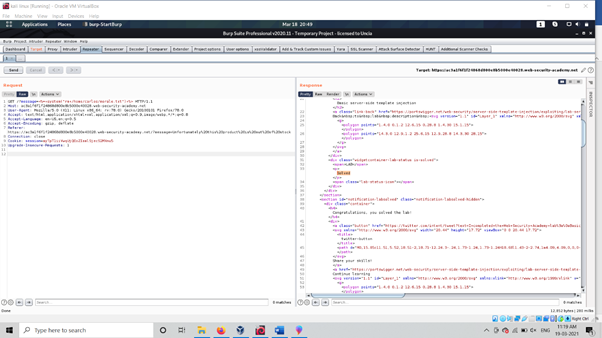
As above picture we are able to delete carlos file as we used system command rm to remove <%=+system(“rm+/home/carlos/morale.txt”)+%> This is how template Injection Attack work This is very rarely found security issue On website due to developer mistake or weak configuration of template .
How to mitigate against risk:
- Framework and Library updates up to date .
- Input Sanitization validate user input .
- Use sandbox withing a safe environment
Conclusion :In this blog we discussed How SSTI Vulnerability work How To test For SSTI Vulnerability As we see example attack scenario how to mitigate against Risk . Keep Reading Our Blog !
Thanks For Reading……. See You In Another Blog!
Stick With Our Blog : https://securiumsolutions.com/
Author : Pallab Jyoti Borah | VAPT Analyst